Implementing IPSec Network Security on Cisco IOS XR Software
Information About Implementing IPSec Networks
SC-100
Cisco IOS XR System Security Configuration Guide
Reverse-Route Injection
Reverse-Route Injection (RRI) is the ability of static routes to be automatically inserted into the routing
process for those networks and hosts protected by a remote tunnel endpoint. These protected hosts and
networks are known as remote proxy identities.
Each route is created on the basis of the remote proxy network and mask, with the next hop to this
network being the remote tunnel endpoint. By using the remote tunnel endpoint as the next hop, the
traffic is forced through the crypto process to be encrypted.
After the static route is created on the VPN router, this information is propagated to upstream devices,
allowing them to determine the appropriate VPN router in which to send returning traffic to maintain
IPSec state flows. Being able to determine the appropriate VPN router is particularly useful when
multiple VPN routers are used at a site to provide load balancing or automatic switchover, or when the
remote VPN devices are not accessible through a default route. Routes are created in either the global
routing table or the appropriate virtual route forwarding (VRF) table.
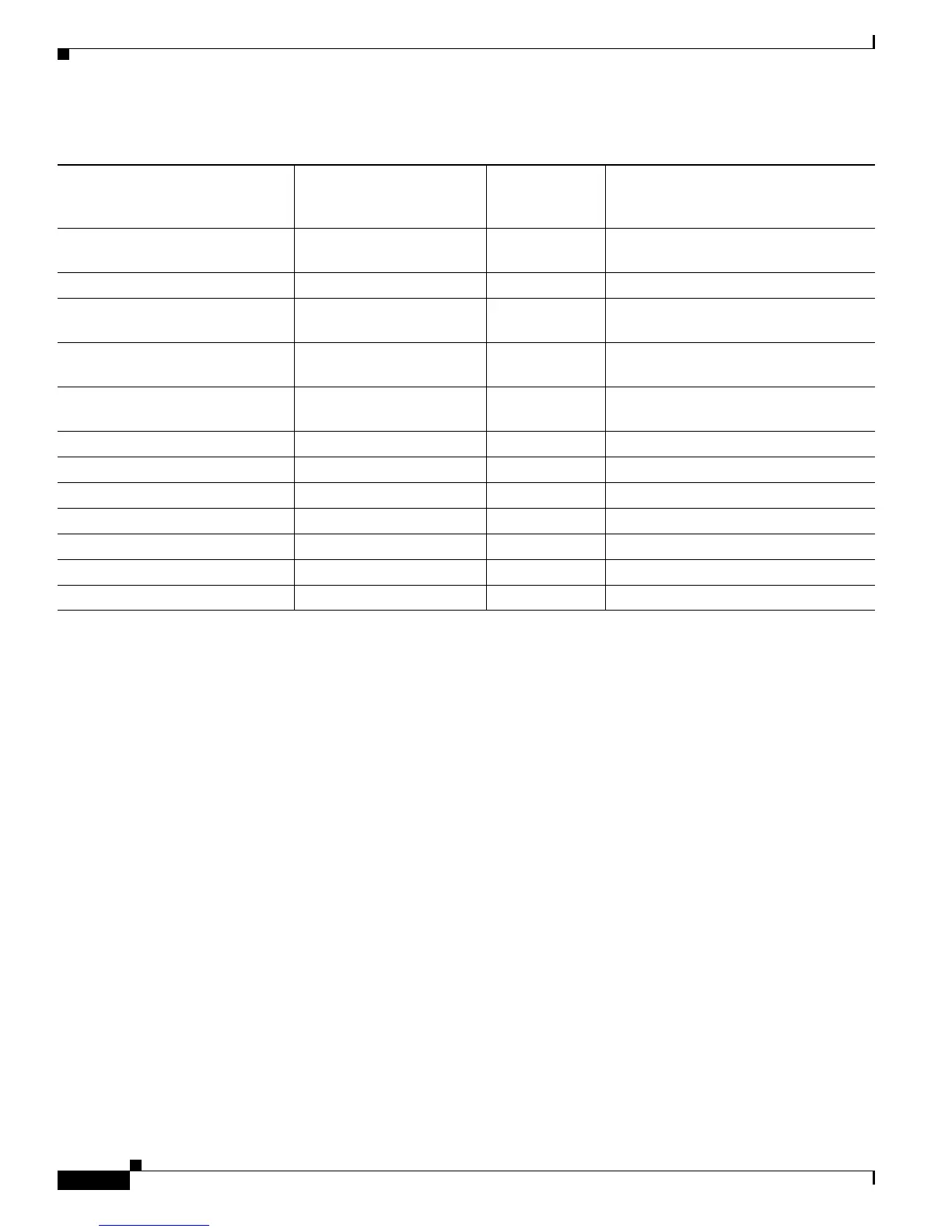
Table 4 Pre-Fragmentation for Cisco IPSec VPN SPA Dependencies
Pre-Fragmentation for IPSec VPN
SPAs Feature State (Enabled or
Disabled)
Service IPSec Interface
“crypto ipsec df-bit”
Configuration
Incoming Packet
DF Bit State Result
Enabled crypto ipsec df-bit copy 0 Fragmentation occurs before
encryption.
Enabled crypto ipsec df-bit copy 1 Packets are dropped.
Enabled crypto ipsec df-bit clear 0 Fragmentation occurs before
encryption.
Enabled crypto ipsec df-bit clear 1 Packets are sent to egress interfaces (not
fragmented before encryption).
1
1. A packet that is sent to egress interfaces can get fragmented on an egress LC under the following conditions: Packet exceeds the MTU of the egress
physical interface. The df-bit is not set on the outer IP header.
Enabled crypto ipsec df-bit set 0 Fragmentation occurs before
encryption.
Enabled crypto ipsec df-bit set 1 Packets are dropped.
Disabled crypto ipsec df-bit copy 0 Packets are sent to egress interfaces.
1
Disabled crypto ipsec df-bit copy 1 Packets are dropped.
Disabled crypto ipsec df-bit clear 0 Packets are sent to egress interfaces.
1
Disabled crypto ipsec df-bit clear 1 Packets are sent to egress interfaces.
1
Disabled crypto ipsec df-bit set 0 Packets are sent to egress interfaces.
1
Disabled crypto ipsec df-bit set 1 Packets are dropped.

 Loading...
Loading...











