20
5. Advanced user
5.1 Import and export settings
Importing and exporting configurations of ESET
Cybersecurity is available in Advanced mode under
Setup.
Both Import and Export use archive files to store the
configuration. Import and export are useful if you need
to backup the current configuration of ESET
Cybersecurity to be able to use it later. The export
settings option is also convenient for users who wish to
use their preferred configuration of ESET Cybersecurity
on multiple systems - they can easily import the
configuration file to transfer the desired settings.
5.1.1 Import settings
Importing a configuration is very easy. From the main
menu, click Setup > Import and export settings ... and
then select the Import settings option. Enter the name
of the configuration file or click the Browse... button to
browse for the configuration file you wish to import.
5.1.2 Export settings
The steps to export a configuration are very similar.
From the main menu, click Setup > Import and export
settings ... Select the Export settings option and enter
the name of the configuration file. Use the browser to
select a location on your computer to save the
configuration file.
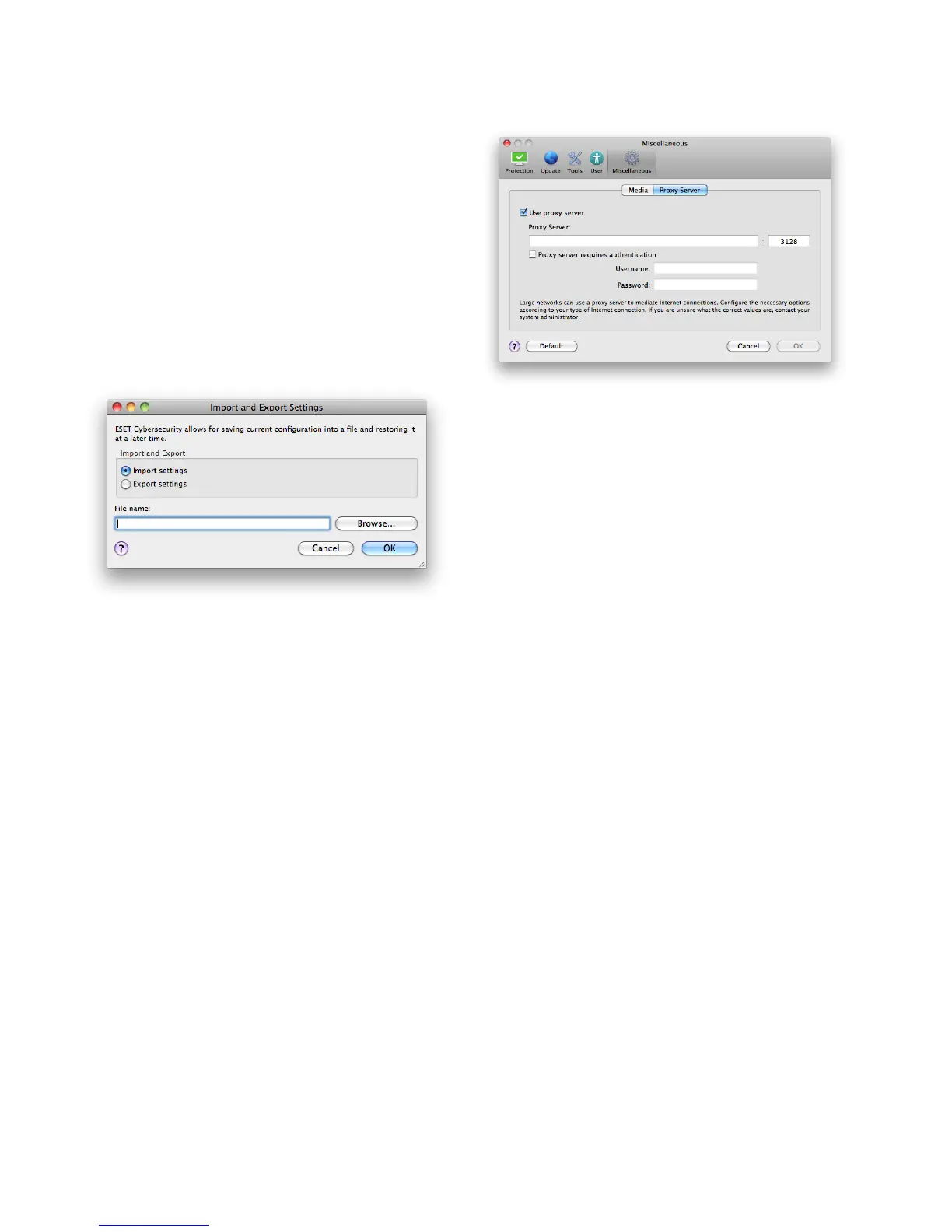
5.2 Proxy server setup
Proxy server settings can be configured under
Miscellaneous > Proxy Server. Specifying the proxy
server at this level defines global proxy server settings
for all of ESET Cybersecurity. Parameters here will be
used by all modules requiring connection to the
Internet.
To specify proxy server settings for this level, select the
Use proxy server check box and then enter the address
of the proxy server into the Proxy Server field, along
with the port number of the proxy server.
If communication with the proxy server requires
authentication, select the Proxy server requires
authentication checkbox and enter a valid Username
and Password into the respective fields.
5.3 Removable media blocking
Removable media (i.e., CD or USB key) may contain
malicious code and put your computer at risk. To block
removable media, check the Enable removable media
blocking option. To allow access to certain types of
media, uncheck desired media volumes.

 Loading...
Loading...











