5
2. Installation
Before you begin the installation process, please close all
open programs on your computer. ESET Cybersecurity
contains components that may conflict with other
antivirus programs that may already be installed on your
computer. ESET strongly recommends that you remove
any other program to prevent potential problems. You
can install ESET Cybersecurity from an installation CD or
from a file available on the ESET website.
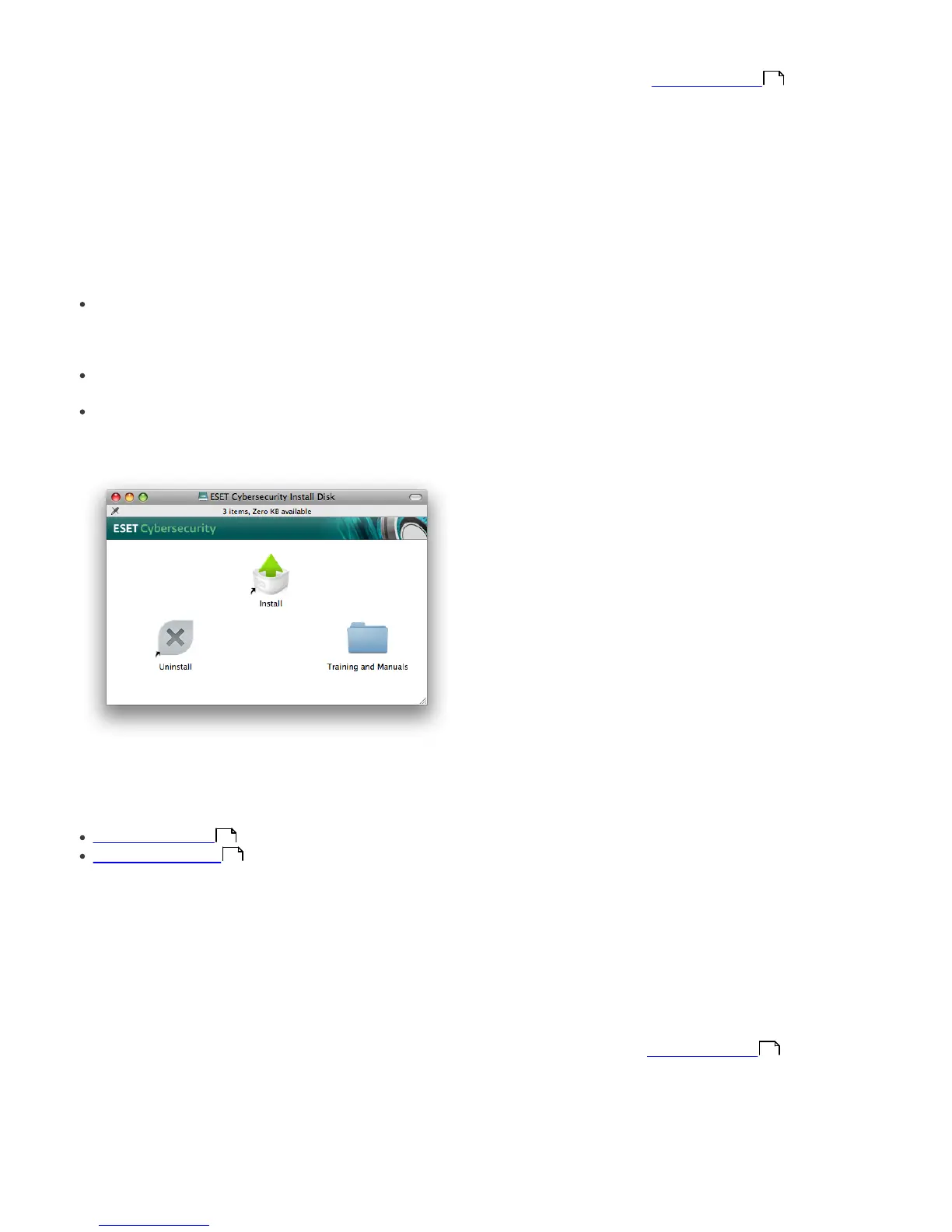
To launch the installer wizard, do one of the following:
If you are installing from the installation CD, insert the
CD into the CD-ROM drive and the menu screen will
appear. Double-click on the ESET Cybersecurity
Installation icon to launch the installer.
If you are installing from a downloaded file, double-
click the file you downloaded to launch the installer.
Additional features, including manuals, training, and
uninstalling can be accessed by double-clicking on the
appropriate icon from the menu screen.
Launch the installer and the installation wizard will guide
you through the basic setup. After agreeing to the End
User License Agreement, you can choose from the
following installation types:
Typical installation
Custom installation
2.1 Typical installation
Typical installation includes the configuration options
that are appropriate for most users. The settings provide
maximum security combined with excellent system
performance. Typical installation is the default option
and is recommended if you do not have particular
requirements for specific settings.
The ThreatSense.Net Early Warning System helps
ensure that ESET is immediately and continuously
informed of new infiltrations in order to quickly protect
our customers. The system allows for submission of new
threats to ESET Threat Lab, where they are analyzed,
processed and added to the virus signature database. By
default, the Enable ThreatSense.Net Early Warning
System option is selected. Click Setup... to modify
detailed settings for the submission of suspicious files.
(For more information see ThreatSense.Net ).
The next step in the installation process is to configure
Detection of potentially unwanted applications.
Potentially unwanted applications are not necessarily
malicious, but can often negatively affect the behavior of
your operating system. These applications are often
bundled with other programs and may be difficult to
notice during the installation process. Although these
applications usually display a notification during
installation, they can easily be installed without your
consent. Select the Enable detection of potentially
unwanted applications option to allow ESET
Cybersecurity to detect this type of threat
(recommended). If you do not wish to Enable this
feature, select the Disable detection of potentially
unwanted applications option.
The final step in Typical installation mode is to confirm
installation by clicking the Install button.
2.2 Custom installation
Custom installation is designed for experienced users
who wish to modify advanced settings during the
installation process.
If you are using a proxy server you can define its
parameters now by selecting the I use a proxy server
option. Enter the IP address or URL of your proxy server
in the Address field. In the Port field, specify the port
where the proxy server accepts connections (3128 by
default). In the event that the proxy server requires
authentication, enter a valid Username and Password
to grant access to the proxy server. If you are sure that
no proxy server is used, choose the I do not use a proxy
server option.If you are not sure, you can use your
current system settings by selecting Use system
settings (Recommended).
In the next step you can Define privileged users that will
be able to edit the program configuration. From the list
of users on the left side, select the users and Add them
to the Privileged Users list. To display all system users,
select the Show all users option.
The ThreatSense.Net Early Warning System helps
ensure that ESET is immediately and continuously
informed of new infiltrations in order to quickly protect
our customers. The system allows for submission of new
threats to ESET Threat Lab, where they are analyzed,
processed and added to the virus signature database. By
default, the Enable ThreatSense.Net Early Warning
System option is selected. Click Setup... to modify
detailed settings for the submission of suspicious files.
For more information see ThreatSense.Net .
The next step in the installation process is to configure
detection of potentially unwanted applications.
Potentially unwanted applications are not necessarily
malicious, but can often negatively affect the behavior of
your operating system. These applications are often
bundled with other programs and may be difficult to
5
5
18
18

 Loading...
Loading...











