Accessing the switch 25
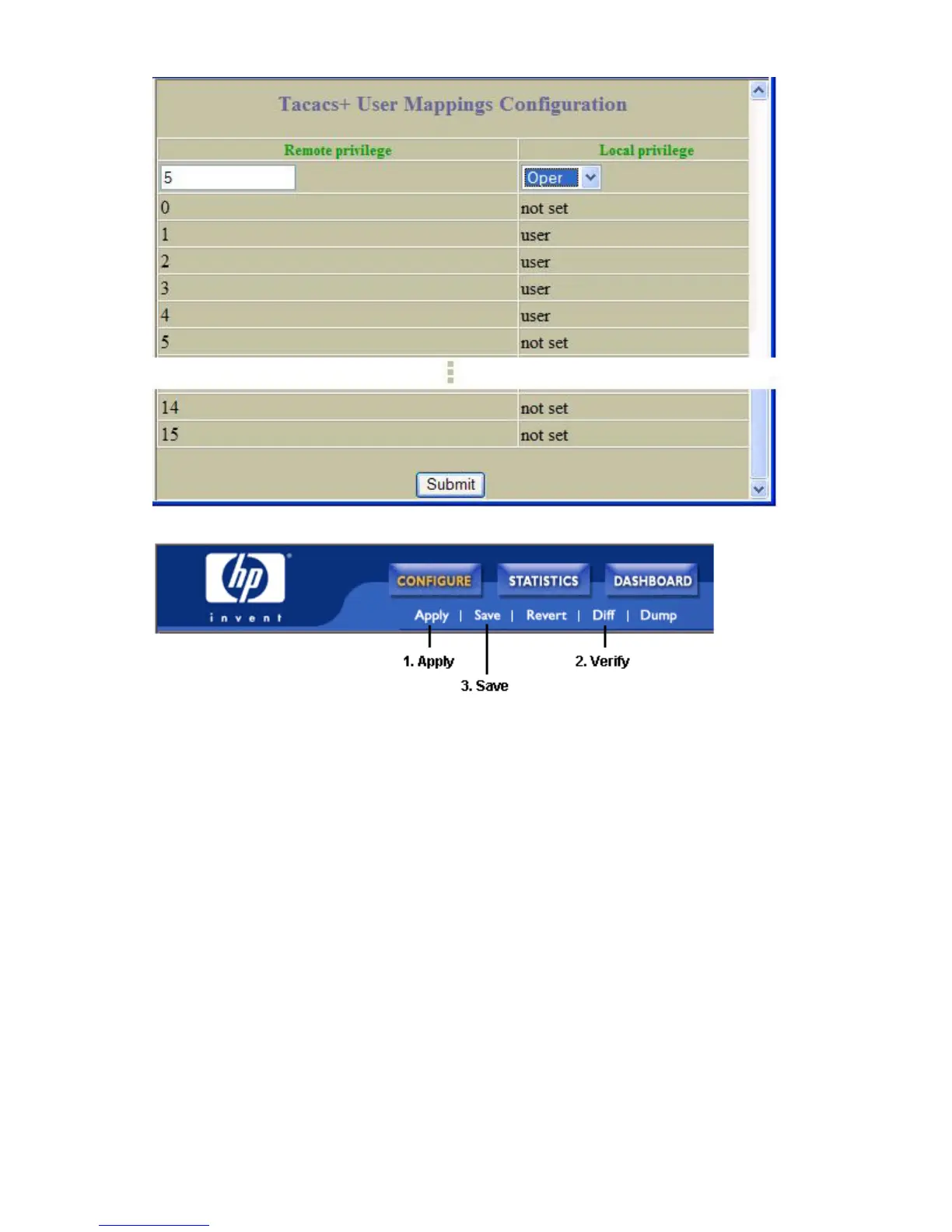
e. Configure custom privilege-level mapping (optional). Click Submit to accept each mapping change.
2. Apply, verify, and save the configuration.
Secure Shell and Secure Copy
Secure Shell (SSH) and Secure Copy (SCP) use secure tunnels to encrypt and secure messages between a remote
administrator and the switch. Telnet does not provide this level of security. The Telnet method of managing a switch
does not provide a secure connection.
SSH is a protocol that enables remote administrators to log securely into the switch over a network to execute
management commands. By default, SSH is disabled (off) on the switch.
SCP is typically used to copy files securely from one machine to another. SCP uses SSH for encryption of data on the
network. On a switch, SCP is used to download and upload the switch configuration via secure channels. By default,
SCP is disabled on the switch.
The switch implementation of SSH is based on version 1.5 and version 2.0, and supports SSH clients from version
1.0 through version 2.0. Client software can use SSH version 1 or version 2. The following SSH clients are
supported:
• SSH 3.0.1 for Linux (freeware)
• SecureCRT® 4.1.8 (VanDyke Technologies, Inc.)
• OpenSSH_3.9 for Linux (FC 3)
• FedoraCore 3 for SCP commands
• PuTTY Release 0.58 (Simon Tatham) for Windows
 Loading...
Loading...















