SB main functionalities:
• Check the STM32 security configuration and set up runtime protections.
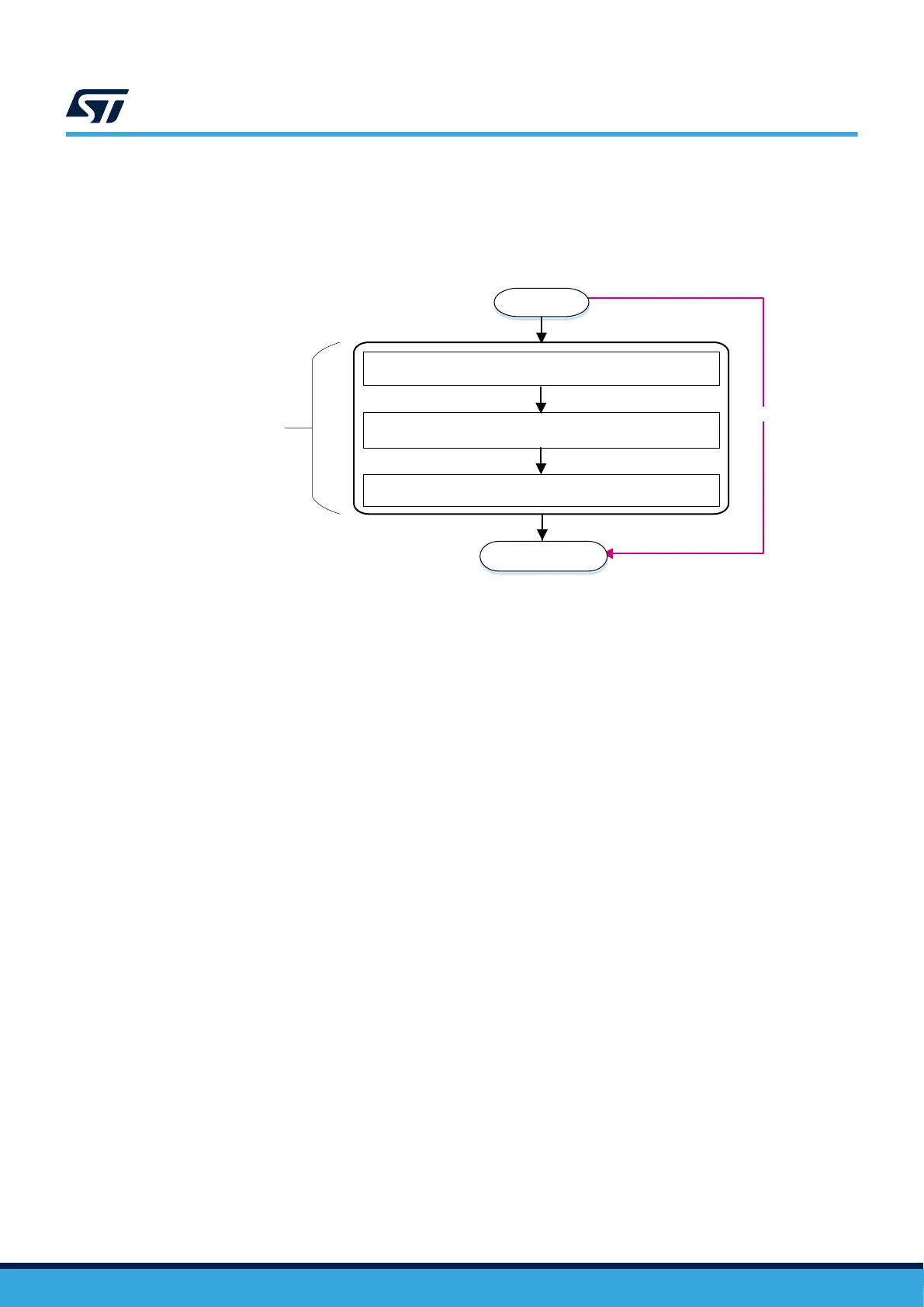
• Assert the integrity and authenticity of the user application images that are executed (see the figure below).
Figure 6. Secure boot FSM
DT50950V1
Compute and check the user application firmware signature
Check device security configuration (option bytes)
Set security peripheral configuration (MPU, firewall, or IWDG)
X
Secure boot
Reset
User application
Device security check
This part of the SB application checks if static configurations are correct, and sets the dynamic ones. Static
secure configurations are defined by option bytes (RDP, PCROP, WRP, and HDP). Dynamic protections must be
programmed (firewall, MPU, tamper detection, and IWDG).
Integrity and authenticity check
The firmware integrity is performed by hashing the application image (with MD5, SHA1, or SHA256 hash
algorithms), and comparing the digest with the expected one. This way, the application firmware is considered
error-free.
An authenticity check is added if the expected tag is encrypted with a key shared between the firmware owner
and the device. This key is stored in a protected area of the device.
Protection attributes
The SB firmware must have the following attributes to fulfill its role:
• It must be the device-unique entry point (no bypass).
• Its code must be immutable.
• It must have access to sensitive data (such as certificates or application signatures).
The most sensitive SB part takes benefit from process and data isolation features, like firewall, MP, U or secure
hide protection. the implementation depends on the STM32 available features.
5.3.2 Secure firmware update (SFU)
The SFU provides a secure implementation of in-field firmware updates, enabling the download of new firmware
images to a device.
The firmware update is a sensitive operation that must protect two parties:
• the device owner: the goal is to avoid loading a corrupted firmware (intentionally or not) that can damage
the device.
• the application owner (OEM): needs to protect his firmware from being cloned or loaded into
an unauthorized device.
AN5156
STMicroelectronics proprietary SBSFU solution
AN5156 - Rev 8
page 24/56
 Loading...
Loading...