Secure process isolation strategy
At reset, the privileged mode is the default one for any process. The SB application is then executed in privileged
mode. The idea is to isolate secure processes (such as SB, OS kernel, key manager, or SFU) from unsecured or
untrusted processes (user applications).
Table 14. Process isolation
Firmware type Mode Resources access
Secure firmware (such as SB or OS kernel) Privileged Full access
All remaining firmware Unprivileged MPU controlled access: no access, RO, RW
An OS kernel can manipulate MPU attributes dynamically to grant access to specific resources depending on
the currently running task. Access right can be updated each time the OS switches from one task to another.
When to use the MPU
The MPU is used at runtime to isolate sensitive code, and/or to manage access to resources depending on
the process currently executed by the device. This feature is useful especially for advanced embedded operating
systems that incorporate security in their design.
Note: The MPU is available on all STM32 devices except the STM32F0 (see the various programming manuals for
more details).
6.11 Customer key storage (CKS)
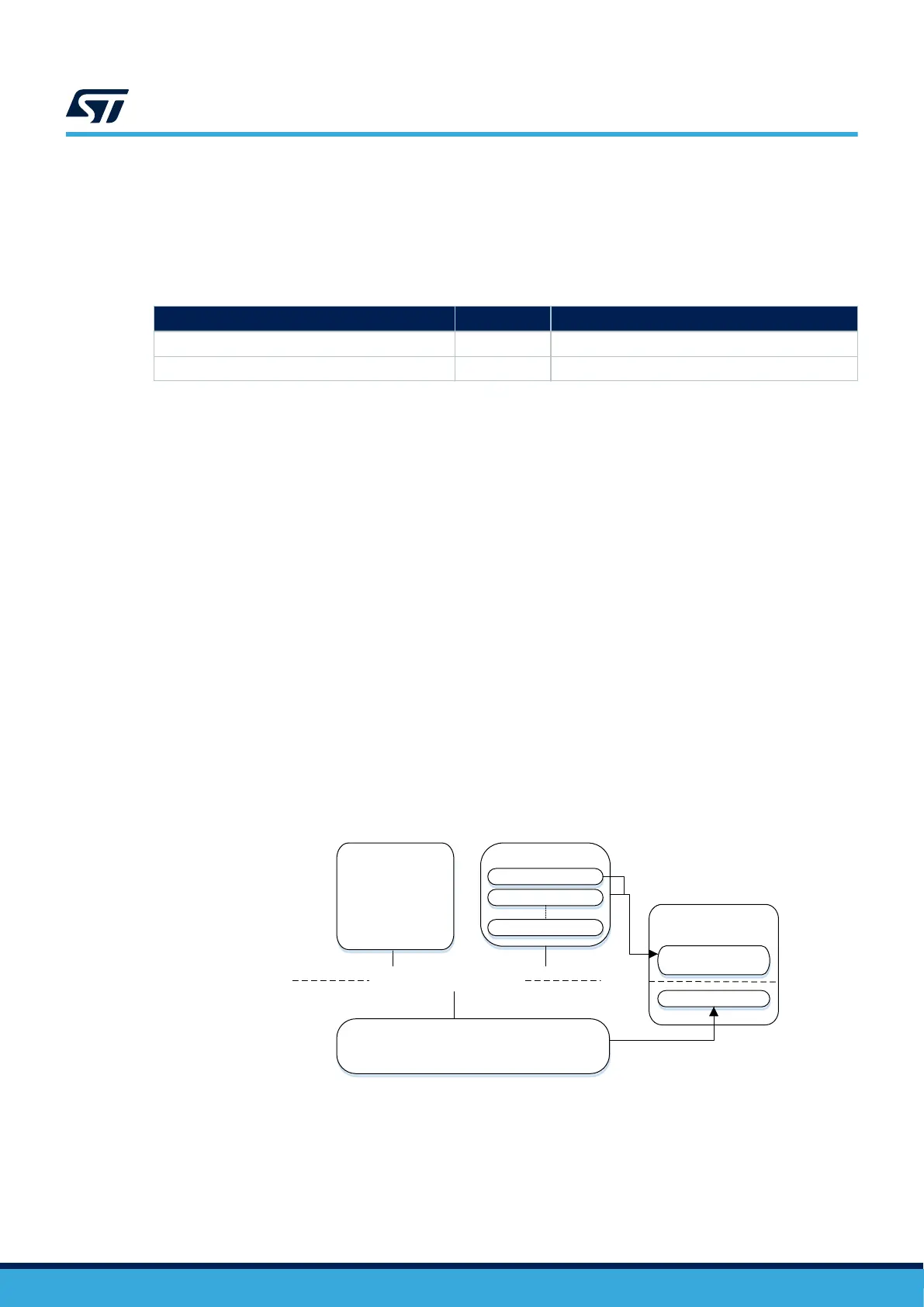
STM32WB series are dual-core devices with one core (CPU1) for user application, and another core (CPU2)
dedicated to the wireless real-time aspect execution (either Bluetooth® Low Energy, ZigBee, or thread protocols).
The flash memory used by CPU2 is isolated from the CPU1 or external access. Communication between the two
cores is ensured by a mailbox and an interprocess channel control hardware block (IPCC).
In addition to the wireless stack execution, the CPU2 offers a secure storage service for cryptographic keys used
with a dedicated AES hardware peripheral (see Figure 13). The AES key register is accessible only to the CPU2,
preventing access to the key by an untrusted process running on the CPU1, or by the debug port.
After the keys have been provisioned inside the secure area, the user application can use them by calling a
secure load service with an index referencing the key and no more the key itself.
Figure 13. Dual-core architecture with CKS service
DT61168V1
CKS
User application
CPU2
CPU1
IPCC and mailbox
Wireless stack
AES hardware
Secure key
register
Data register
Key 0
Key 1
Key n
When to use the CKS
The CKS must be used when a user application relies on AES encryption or decryption. Provisioned keys can be
stored in a secure area, so that no other internal process or external access can read their value.
Note: The CKS is available on STM32WB series only.
AN5156
Customer key storage (CKS)
AN5156 - Rev 8
page 38/56

 Loading...
Loading...