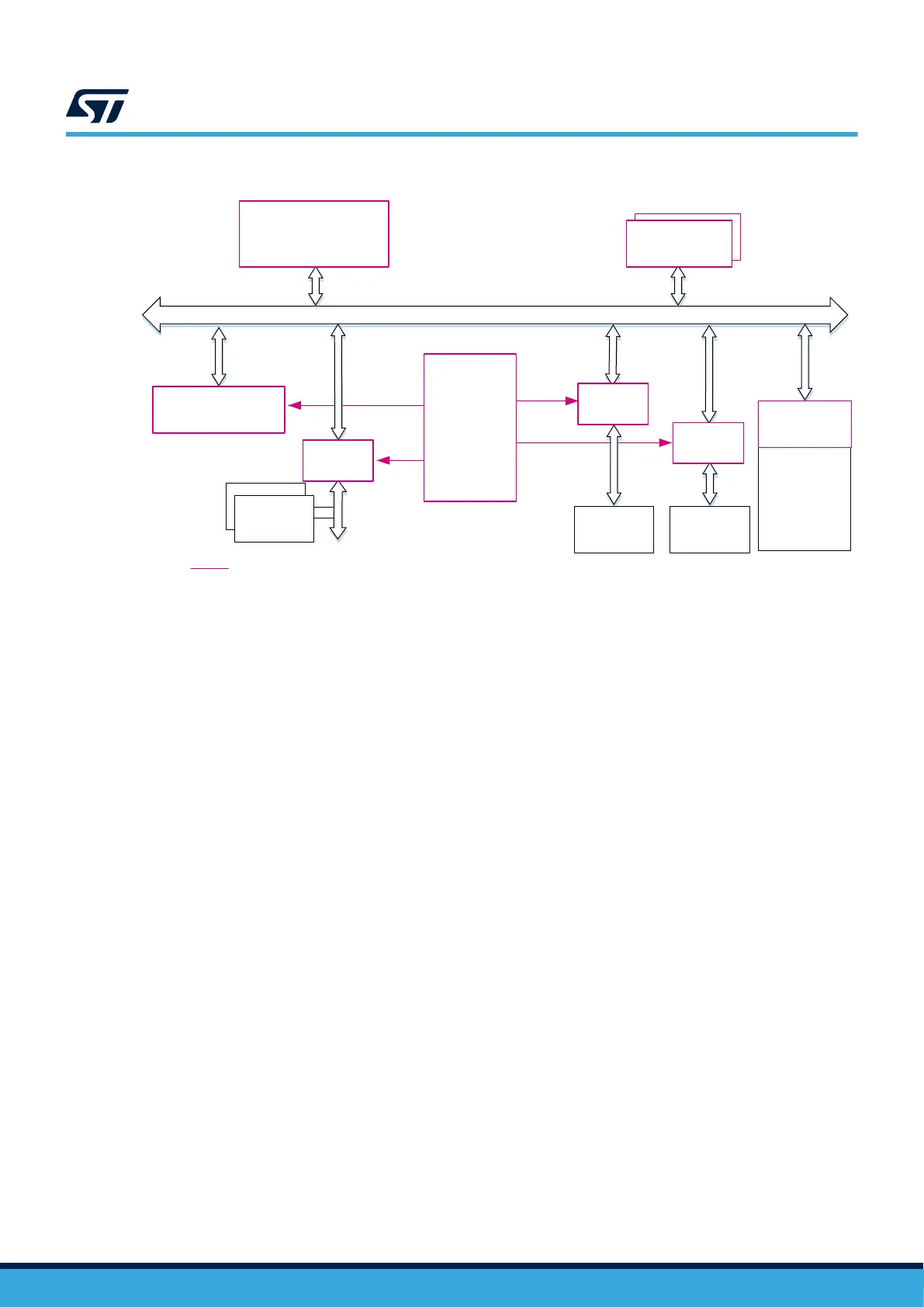
Figure 9. TrustZone® implementation at system level
DT63688V1
Flash
memory
AHB5
APB
Armv8-M
Cortex-M33
SAU/MPU
AHB master
AHB peripherals
AHB/APB
bridge
GTZC
MPCBB
MPCWM
Internal
SRAM
External
memory
APB
peripheral
TrustZone specific implementation
Secure
watermarks and
block based
6.5.1 Core state
The core state depends on the region of the current running code. When the code runs from a secure region,
the core is in secure state. Otherwise, the core is in nonsecure state.
6.5.2 Secure attribution unit (SAU)
The SAU is a hardware unit coupled to the core (as the MPU). The SAU is responsible for setting the security
attribute of the AHB5 transaction. The security attribute of a transaction is fixed by the targeted address of
a memory-mapped resource (memory areas or peripherals). Depending on the SAU configuration, an address is
tagged as secure, nonsecure callable (NSC), or nonsecure. The NSC is a subdomain of the secure domain, that
allows a gateway to be defined for nonsecure code to access the secure domain at a specific entry point.
The SAU is configurable by secure firmware. It can be configured at boot for a fixed configuration, or can be
dynamically modified by a secure firmware.
Note: A security attribute cannot be modified to be less secure (by security order: secure > NSC > nonsecure)
than a default attribute set by hardware through an IDAU (implementation defined secure attribute).
Refer to implementation details of each device in the reference manual.
Address aliasing
The security attribute is set depending on the fixed resource address. However, a memory‑mapped resource can
be set either as secure or nonsecure, depending on the application. To overcome this apparent contradiction,
two addresses are assigned to each memory-mapped resource: one used when the resource must be accessed
in secure mode, one used in nonsecure mode. This mechanism is called address aliasing.
The address aliasing allows also all peripheral accesses to be grouped in only two regions instead of multiple
scattered regions. Finally, the IDAU splits the memory-mapped resources in the following regions:
• peripherals secure/nonsecure regions
• flash memory secure/nonsecure regions
• SRAM secure/nonsecure regions
Refer to device reference manual for the detailed configuration.
AN5156
TrustZone®
AN5156 - Rev 8
page 33/56

 Loading...
Loading...