A.3 Hash algorithms
Hash algorithms guarantee the message integrity. They generate a unique fixed-length bitstream from a message
called the digest. Any difference in the input message produces a totally different digest. The digest cannot be
reversed to retrieve the input message.
Hashing can be used independently from message encryption.
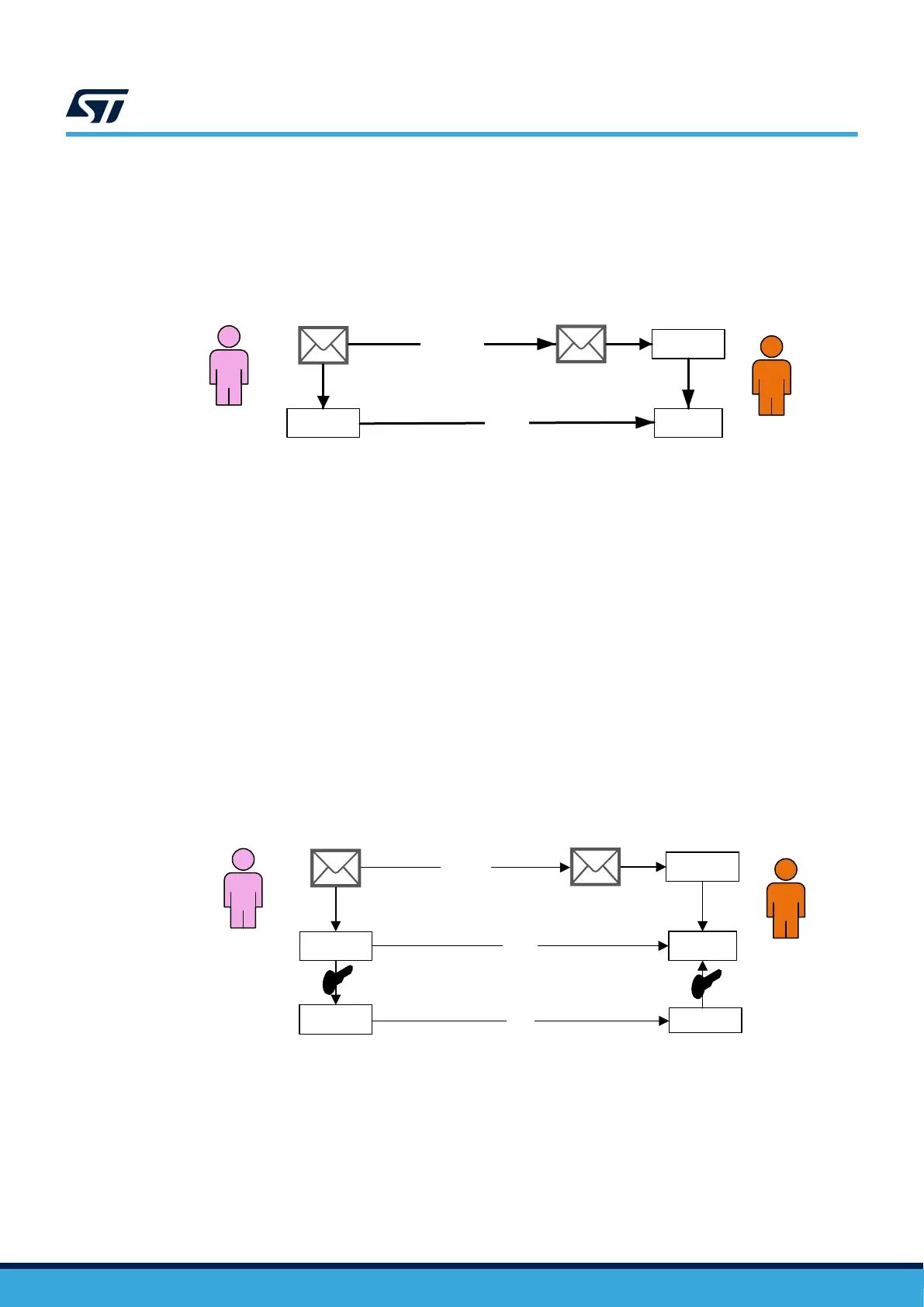
Figure 18. Message hashing
DT50958V1
Digest
Message
HASH
HASH
=?
John Doe1
John Doe2
The difference with classic CRC is the robustness due to operations that are more complex and a much higher
digest length: up to 512 bits instead of 16 or 32 bits. As an example, CRC are reserved for fast integrity checks
during data transfers. Digest length makes them virtually unique and ensures that no collision occurs.
Typical algorithms are the MD5 (128-bit digest), SHA-1 (160-bit digest), SHA-2 (224-, 256-,384-, or 512-bit
digest), and SHA-3 (224-, 256-, 384-, or 512-bit digest).
A.4 MAC or signature and certificate
MAC and signature
The message authentication code (MAC) and the signature add authentication to integrity by encrypting the
message hash. The difference between MAC and signature is that the MAC generation uses a symmetric key
algorithm (Figure 19), while the signature uses the message sender private key (Figure 20).
The signature adds non-repudiation dimension to authentication:
• A private key is not supposed to be revoked (its lifetime goes beyond the transfer operation), while a secret
key may have a limited lifetime (limited to this transfer).
• The private key used for signature is never shared, its security is higher than a secrete key.
Figure 19. MAC generation with secrete key algorithm
DT50959V1
HASH
HASH
=?
John Doe1
John Doe2
MAC
Digest
Message
MAC
MAC
Secret
key
Secret
key
AN5156
Hash algorithms
AN5156 - Rev 8
page 47/56

 Loading...
Loading...