22 • DM NVX System Design Guide – DOC. 7977F
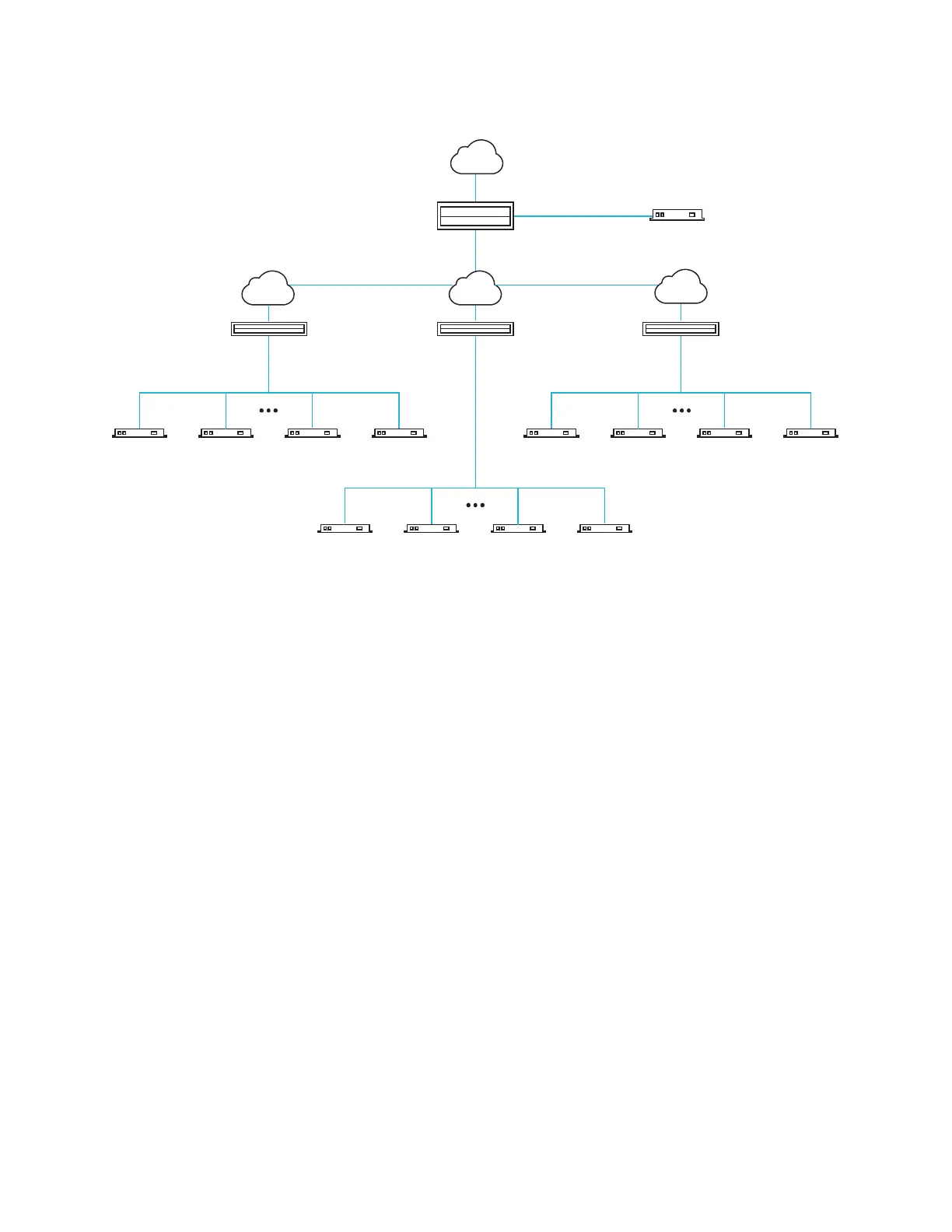
PIM Multicast Routing Protocol for an IP Network
Network Security
Security requires the support of particular capabilities within all devices on the network.
DM NVX networks employ the following security features:
• 802.1X authentication is used to ensure that devices on the network have been
authorized by the network administration team. Unauthorized devices are
prevented from being added to the network and from having access to sensitive
content.
• Active Directory services for endpoint administration can be used to ensure that
administrative privileges for DM NVX devices can be centrally managed, granted,
and revoked when necessary.
• DM NVX endpoints use Advanced Encryption Standard (AES) block cipher with
Public Key Infrastructure (PKI) for stream encryption to protect content from
unauthorized access as it crosses the network.
• SSL-based secure Cresnet over IP (CIP) for DM NVX control ensures that control
processors and DM NVX devices communicate with the intended party device and
that any unauthorized device on the network cannot monitor commands
and status.
• SSH-based command line console access for device configuration and status
protects the device console from access by unauthorized users.
SSL-based Cresnet over IP and SSH-based command line console access are
automatically configured within DM NVX devices and support software. The designer
should focus on 802.1X and Active Directory services within the design.
Net
work
switch
(PIM enabled)
N
et
w
or
k swi
t
ch
Network switch
Network switch
DM NVX
LAN
LAN
LAN
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
DM NVX
VLAN
VLAN
VLAN
VLAN
DM-XIO-DIR-ENT

 Loading...
Loading...











