52
Security Profiles
You can change the current security profile from the Summary page. For
more information, see “Summary”, 35.
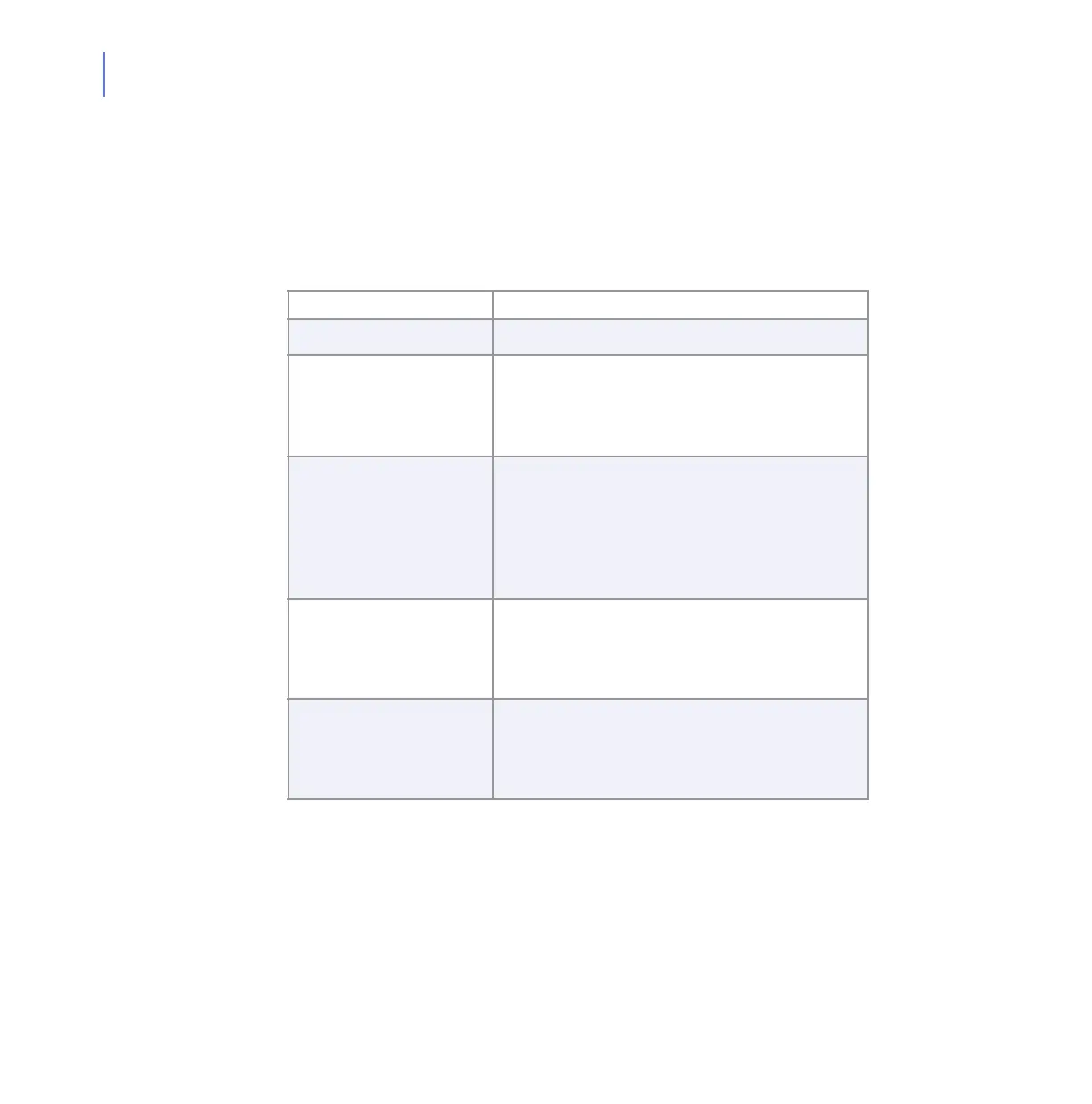
The following table contains a list of the security profiles available in the
product and the type of traffic each of them either allow or deny.
Security profiles Description
Block All Blocks all network traffic (excluding loopback).
Server Allows only IP configuration via DHCP, DNS
lookups and ssh protocol out and in.
The server profile has to be customized
before it can be taken into use.
Mobile Allows normal web browsing and file retrievals
(HTTP, HTTPS, FTP), as well as e-mail and
Usenet news traffic. Encryption programs,
such as VPN and SSH are also allowed.
Everything else is denied. Local rules can be
added after the malware probes detection.
Home Allows all outbound TCP traffic and FTP file
retrievals. Everything else is denied. Local
rules can be added to enable new network
functionality.
Office Allows all outbound TCP traffic and FTP file
retrievals. Everything else is denied by
default. With this profile, a firewall should exist
between 0.0.0.0/0 and the host.
 Loading...
Loading...