HackRF
The content of the file instructs udev to look out for devices with Vendor ID and Product ID matching HackRF devices.
It then sets the UNIX permissions to 660 and the group to plugdev and creates a symlink in /dev to the device.
After creating the rules file you can either reboot or run the command udevadm control --reload-rules as root
to instruct udev to reload all rule files. After replugging your HackRF board, you should be able to access the device
with all utilities as a normal user. If you still can’t access the device, make sure that you are a member of the plugdev
group.
7.1.3 PyBOMBs
If you are using PyBOMBS, note that the HackRF recipe intentionally does not install the udev rules to avoid installation
failures when run as non-root.
7.1.4 Power saving and USB autosuspend
A common problem for laptop users could power management enabling USB autosuspend, which is likely if
hackrf_info returns an error of hackrf_open() failed: Input/Output Error (-1000) on the first execu-
tion, and works if you run it a second time directly afterwards. This can be confirmed by running LIBUSB_DEBUG=3
hackrf_info and checking that the error is a broken pipe.
To fix this, you need to disable USB autosuspend for HackRF. If you use the TLP power manager you can add the
HackRF USB VID/PIDs to the USB_BLACKLIST line in /etc/default/tlp (under Archlinux create a file /etc/
tlp.d/10-usb-blacklist.conf, under Ubuntu the config file can be found at /etc/tlp.conf):
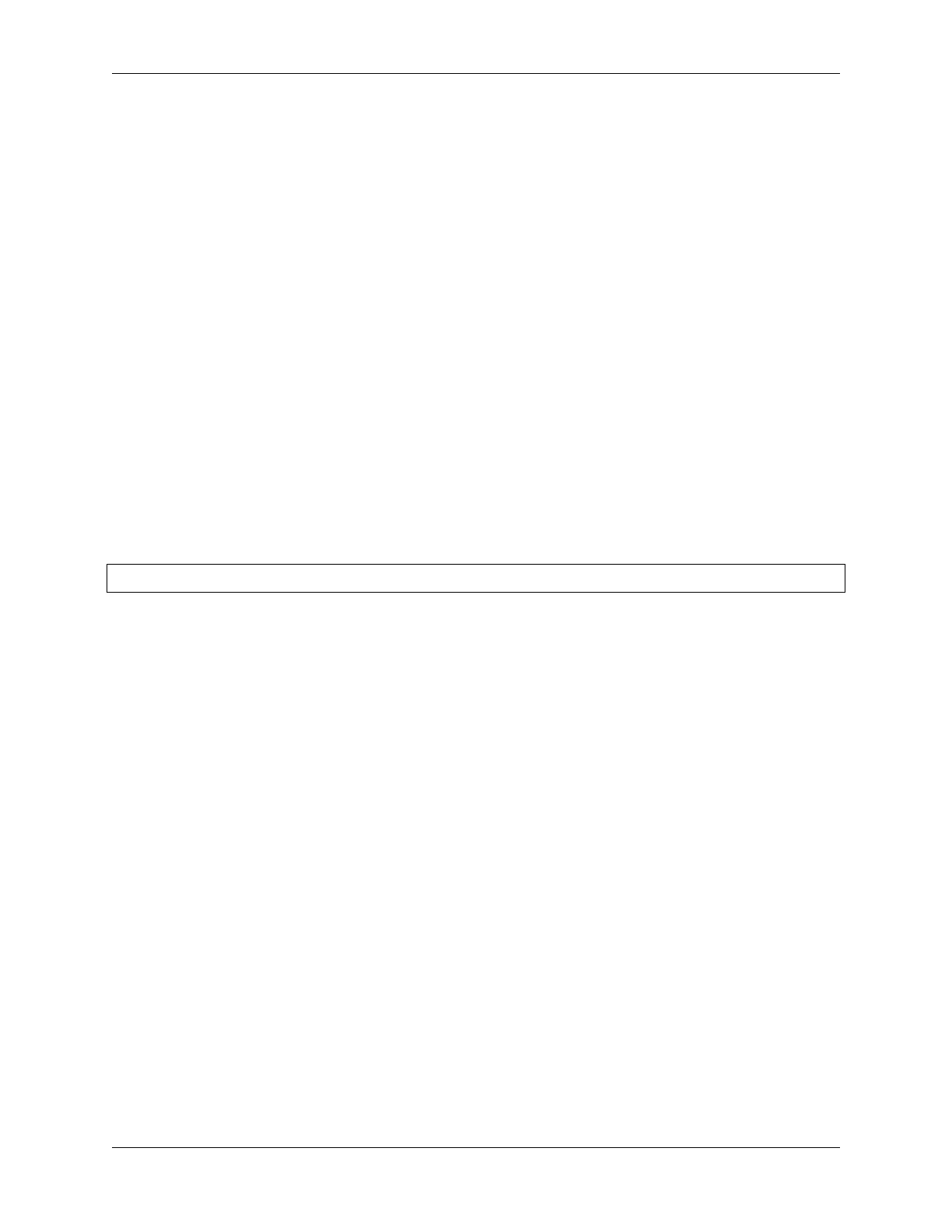
USB_BLACKLIST="1d50:604b 1d50:6089 1d50:cc15 1fc9:000c"
and restart TLP using tlp restart or systemctl restart tlp.
7.1.5 hackrf kernel module
If the command hackrf_info failed with “hackrf_open() .. HACKRF_ERROR_NOT_FOUND” error message, this
could be also a problem of a kernel driver. Some ubuntu versions, like Ubuntu 15.04 with installed gnuradio has a
kernel driver pre-installed. In this case you probably will get some syslog kernel messages like:
• kernel: [ 8932.297074] hackrf 1-9.4:1.0: Board ID: 02
• kernel: [ 8932.297076] hackrf 1-9.4:1.0: Firmware version: 2014.08.1
• kernel: [ 8932.297261] hackrf 1-9.4:1.0: Registered as swradio0
• kernel: [ 8932.297262] hackrf 1-9.4:1.0: SDR API is still slightly experimental and functionality changes may
follow
when you plug in the the HackRF module. Use the command dmesg to check the last system log entries. If you try to
start hackrf_info it will terminate with the error message and the system log will show a message like:
• kernel: [ 8967.263268] usb 1-9.4: usbfs: interface 0 claimed by hackrf while ‘hackrf_info’ sets config #1
To solve this issue check under root account if is there is a kernel module hackrf loaded: lsmod | grep hackrf. If
there is a hackrf kernel module, try to unload it with rmmod hackrf. You must do this command as root, too. After
this the command hackrf_info (and all other hackrf related stuff) should work and the syslog usbfs massage should
vanish.
After a reset or USB unplug/plug this kernel module will load again and block the access again. To solve this you have
to blacklist the hackrf kernel module in /etc/modprobe.d/blacklist(.conf) The current filename of the blacklist file may
differ, it depends on the current ubuntu version. In ubuntu 15.04 it is located in /etc/modprobe.d/blacklist.conf. Open
this file under root account with a text editor an add the following line at the end:
24 Chapter 7. FAQ

 Loading...
Loading...