• Drive management
• Encryption control/key management
• Diagnostic extraction
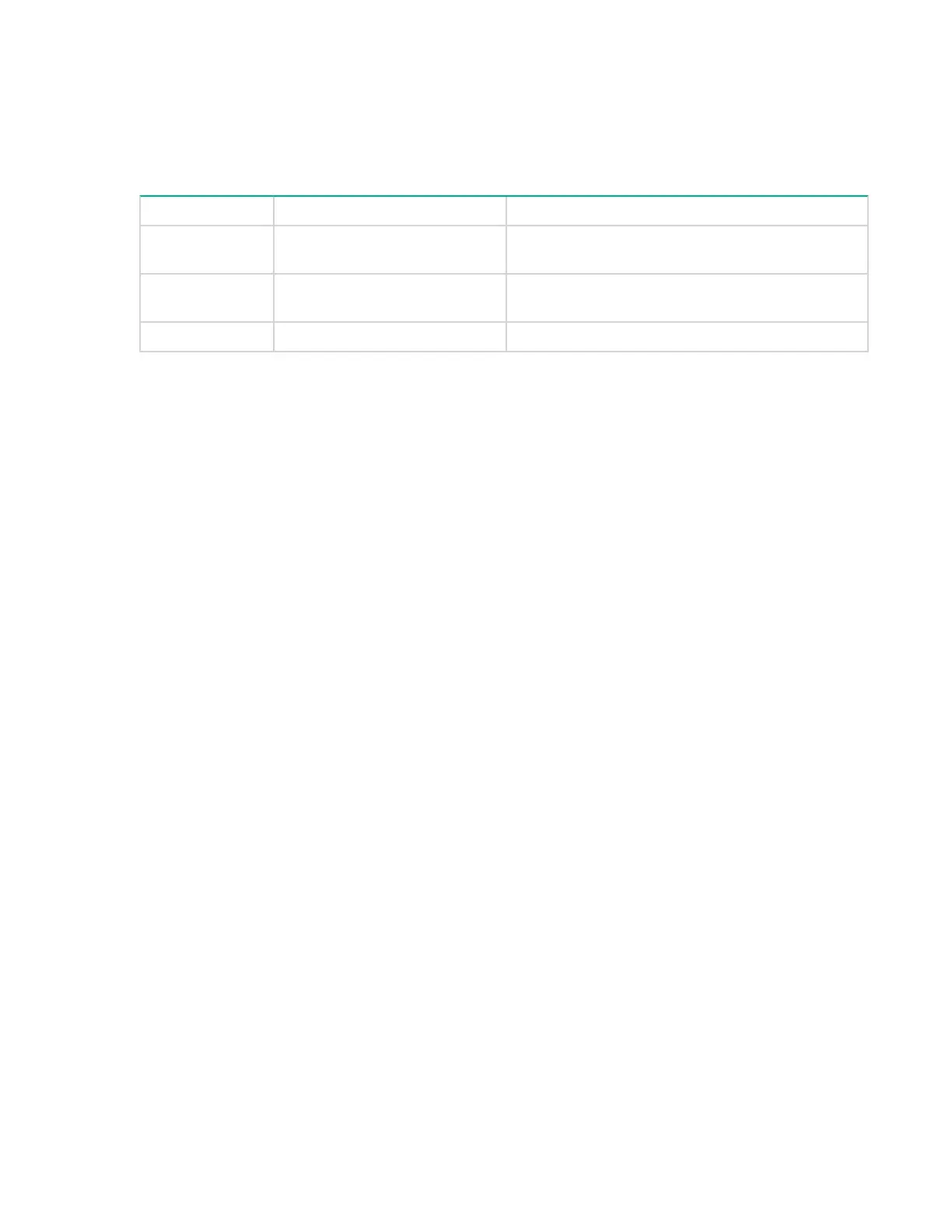
The iADT port supports the following network services through the 10/100 Mbps Ethernet port:
Service Name Port Number/Base Protocol Description
iADT 4169/TCP Internet Automation Device Interface using
nonsecure ADT protocol over TCP (see ADT-2).
iADI-TLS 9614/TCP Internet Automation Device Interface using secure
ADT protocol over TCP (see ADT-2).
iADT-DISC 4169/TCP iADT Discovery over UDP (see ADT-2).
How the drive will be configured depends upon the overall configuration of the data storage site. The site
consists of a number of entities:
• Host computers performing backups
• Tape libraries (automation devices)
• Tape drives installed in tape libraries (drives may provide connectivity between the library and hosts)
• Management hosts performing security configuration
• Encryption key managers (EKMs)
• Hosts accessing the drives for debugging information
It may be necessary for a drive to communicate directly with a network entity, such as an external Key
Manager, which requires network traffic to pass through a router on the edge of the library. It requires
careful configuration of the router to ensure security of the network inside the library.
The network inside a library is configured using techniques unique to that library. This section only gives
guidance on the goals of that configuration. The library network configuration has two purposes:
• To permit communication among the library, all drives, and any other entities.
• To ensure the security of those communications.
If the network connects only the library and drives, there can be no physical connection between the
network and any network outside the library. If it is not feasible, then IP packets to or from the following
port numbers will be blocked:
• iADT (TCP/4169)
• iADT-TLS (TCP/9614)
• iADT-DISC (UDP/4169)
If an external host (such as an external Key Manager) requires access to the library only and the library
has two Ethernet ports with a firewall between them, then one port will be used only for external access
and the other for internal access. The situation is effectively the same as the previous paragraph.
If an external host requires access to drives, only the minimum number of protocols will be allowed to
pass into and out of the library. Any connections carrying SCSI commands will be secured by using the
iADI-TLS port. Either of these will require security configuration to be performed on the drive.
56 Special features for automation
 Loading...
Loading...











