5
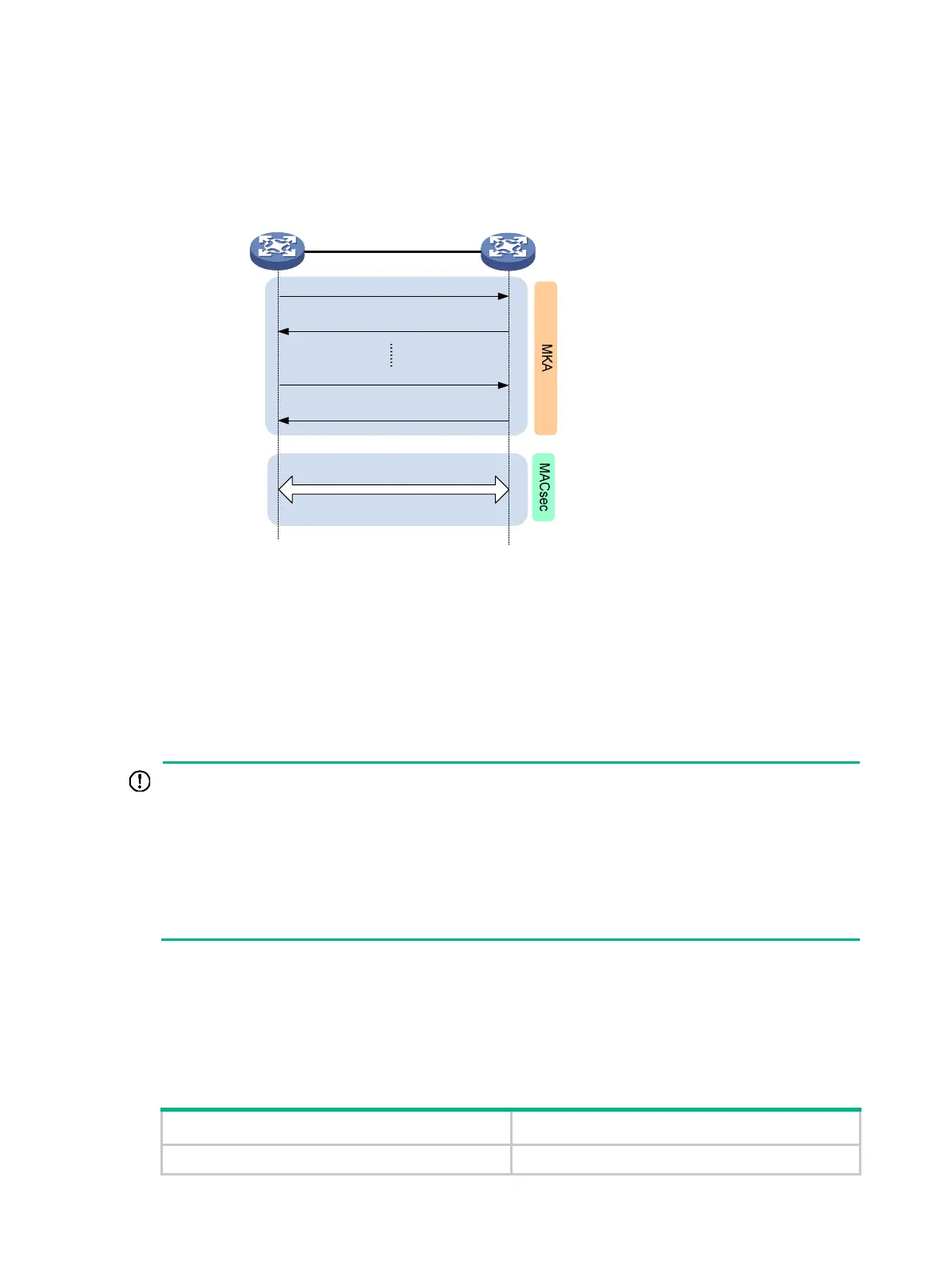
In this mode, the session negotiation, secure communication, and session termination processes are
the same as the processes in client-oriented mode. However, MACsec performs a key server
selection in this mode. The port with higher MKA key server priority becomes the key server, which is
responsible for the generation and distribution of SAKs.
Figure 4 MACsec interactive process in device-oriented mode
Protocols and standards
• IEEE 802.1X-2010, Port-Based Network Access Control
• IEEE 802.1X-2006, Media Access Control (MAC) Security
Feature and hardware compatibility
IMPORTANT:
MKA cannot be enabled on MACsec-incapable interfaces. In this switch series, the following
interfaces are MACsec-capable:
• The leftmost eight interfaces (GigabitEthernet x/0/1 through GigabitEthernet x/0/8) on each
switch.
• The interfaces on LSWM2XGT2PM(JH156A) and LSWM2SP2PM(JH157A) interface modules
installed on switch models except HPE 5510 24G SFP 4SFP+ HI 1-slot Switch (JH149A). The
interface modules do not support hot swapping if MKA is enabled on such interfaces.
MACsec configuration task list
In device-oriented mode, the MACsec configuration takes effect on Layer 2 and Layer 3 Ethernet
ports. In client-oriented mode, the MACsec configuration takes effect only on 802.1X-enabled ports.
To configure MACsec, perform the following tasks:
Tasks at a glance Remarks
(Required.)
Enabling MKA
N/A
EAPOL
EAPOL-MKA: key server
Device A
EAPOL-MKA: MACsec capable
EAPOL-MKA: key name, SAK
EAPOL-MKA: SAK installed
Session
negotiation
Secure
communication
Secured frames
Device B

 Loading...
Loading...



















