What to do if my Ricoh Aficio MP C2050 says 'An authentication error occurred because the user name contains a space, colon (:), or quotation mark ("))'?

 Loading...
Loading...
What to do if my Ricoh Aficio MP C2050 says 'An authentication error occurred because the user name contains a space, colon (:), or quotation mark ("))'?
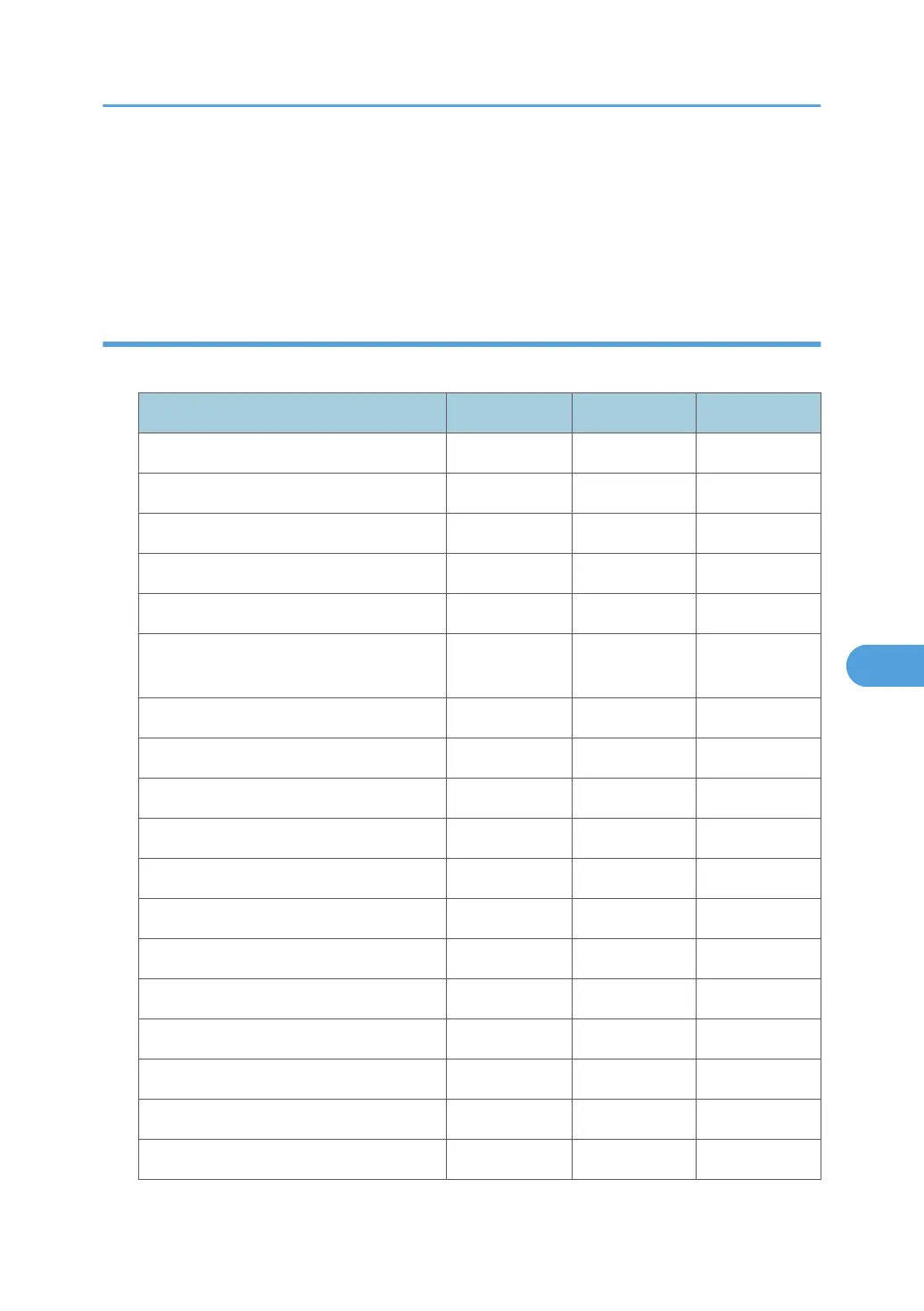
| output speed | 20 ppm BW & Full-Color |
|---|---|
| warm-up time | 25 seconds |
| first copy time full-color | 9.5 seconds |
| copy resolution | 600 x 600 dpi |
| original capacity | 50 sheets |
| dimensions | 23.1" x 25.8" x 33.3" (587 x 655 x 845 mm) |
| weight | 220 lbs |
| power requirements | 120V, 60Hz, 12A |
| cpu | RM7035C @ 533MHz |
|---|---|
| memory | 768 MB (512 MB + 256 MB) RAM (Standard); 1GB RAM (Maximum) |
| max. print speed | 20 ppm BW & Full-Color |
| max. print resolution | 1200 x 1200 dpi |
| standard interfaces | 10Base-T/100Base-TX Ethernet (RJ-45), USB 2.0 Device, USB 2.0 Host I/F |
| scanner resolution | From 100 to 600 dpi (1200 dpi for TWAIN) |
|---|---|
| scanning speed bw | 41 ipm |
| scanning speed full-color | 26 ipm |
| scan area main scan | 11.7" (297mm) |
| scan area sub scan | 17" (432mm) |
| output speed | 25 ppm BW & Full-Color |
|---|---|
| warm-up time | 25 seconds |
| first copy time full-color | 9.5 seconds |
| copy resolution | 600 x 600 dpi |
| original capacity | 50 sheets |
| dimensions | 23.1" x 25.8" x 33.3" (587 x 655 x 845 mm) |
| weight | 220 lbs |
| power requirements | 120V, 60Hz, 12A |
| cpu | RM7035C @ 533MHz |
|---|---|
| memory | 768 MB (512 MB + 256 MB) RAM (Standard); 1GB RAM (Maximum) |
| max. print speed | 25 ppm BW & Full-Color |
| max. print resolution | 1200 x 1200 dpi |
| standard interfaces | 10Base-T/100Base-TX Ethernet (RJ-45), USB 2.0 Device, USB 2.0 Host I/F |
| scanner resolution | From 100 to 600 dpi (1200 dpi for TWAIN) |
|---|---|
| scanning speed bw | 41 ipm |
| scanning speed full-color | 26 ipm |
| scan area main scan | 11.7" (297mm) |
| scan area sub scan | 17" (432mm) |
Step-by-step guide to configuring the machine's security settings and administrator account.
Explains how to improve security through authentication and access limits.
Outlines the machine's security features like authentication and encryption.
Covers methods to restrict access to machine settings and stored data.
Details the roles and responsibilities of different administrator types.
Explains the concept and types of administrator authentication.
Provides instructions on how to activate and configure administrator authentication.
Step-by-step guide for setting up administrator accounts and privileges.
Explains the purpose of user authentication for preventing unauthorized access.
Guides on activating and configuring user authentication methods.
Details the method of limiting access based on user codes.
Explains using the Address Book for user authentication.
Details embedding patterns to discourage or prevent unauthorized copying of documents.
Explains securing copying by embedding hidden text patterns.
Covers setting permissions for accessing stored scan files and Document Server files.
Explains setting passwords for stored files for enhanced protection.
Details methods to prevent data leaks during transmission via network.
Explains using S/MIME for encrypted email transmission and electronic signatures.
Guides on encrypting data stored on the hard disk to prevent leakage.
Covers methods for overwriting and erasing data from the hard disk.
How to prevent unauthorized changes to machine settings by users.
Setting permission levels for users to change machine settings.
Specifying which machine functions are accessible to users.
Covers viewing, deleting, and transferring machine log files.
Methods to limit network access by IP address, ports, or protocols.
How to encrypt passwords for transmission to prevent them from being analyzed.
Explains establishing secure communication using SSL, SNMPv3, and IPsec.
Details on configuring IPsec for secure data packet transmission.
Overview of extended security features and their configuration.
Encrypting passwords transmitted during user authentication via printer drivers.
Guides on encrypting data stored in the machine's Address Book.
Locking files with passwords to prevent unauthorized access and guessing attacks.
Addresses issues where users cannot operate the machine due to authentication problems.
Provides solutions for scenarios where the machine is unresponsive to users.
Details supervisor roles in managing administrator accounts and passwords.
Lists all settings configurable by the machine administrator.
Lists all settings configurable by the network administrator.
Lists all settings configurable by the file administrator.