Rockwell Automation Publication 2080-UM002N-EN-E - November 2022 225
Chapter 11
Controller Security
Micro800 security generally has two components:
• Exclusive Access that prevents simultaneous configuration of the controller by two
users
• Controller Password Protection that secures the Intellectual Property contained
within the controller and prevents unauthorized access
Protected Mode To maintain the secure operation of your Micro800 controllers, operations that can disrupt
controller operation are restricted based on the controller operating mode.
Exclusive Access Exclusive access is enforced on the Micro800 controller regardless of whether the controller is
password-protected or not. This means that only one Connected Components Workbench
software session is authorized at one time and only an authorized client has exclusive access
to the controller application. This ensures that only one software session has exclusive access
to the Micro800 application-specific configuration.
Exclusive access is enforced on Micro800 firmware revision 1 and 2. When a Connected
Components Workbench software user connects to a Micro800 controller, the controller is
given exclusive access to that controller.
Password Protection By setting a password on the controller, a user effectively restricts access to the programming
software connections to the controller to software sessions that can supply the correct
password. Essentially, Connected Components Workbench software operation such as upload
and download are prevented if the controller is secured with a password and the correct
password is not provided.
Micro800 controllers with firmware revision 2 and later are shipped with no password but a
password can be set through the Connected Components Workbench software (version 2 or
later).
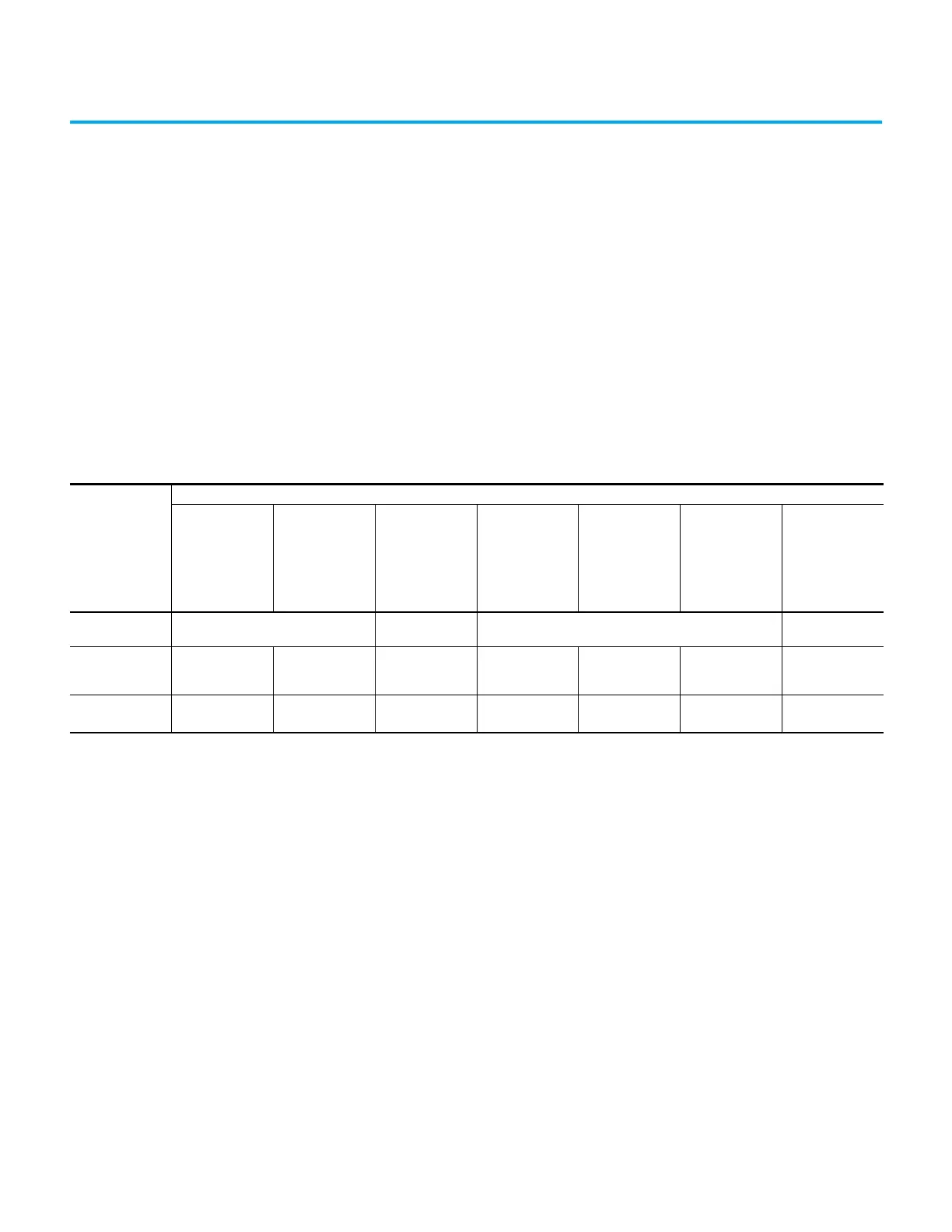
Table 58 - Protected Operations on Micro800 Controllers
Current Controller
Operation
Activity
Firmware Update
Request
Ethernet Port
Configuration
Setting
(1)
(through
Connected
Components
Workbench or
RSLinx)
Serial and USB
Port Configuration
Changes
Lost Password
Recovery
Password Change
Controller Mode
Change
I/O Configuration
Change
Controller in
Program Mode
Accepted Not Allowed Accepted Not Allowed
Controller with
Password Protected
in Run Mode
Rejected
Not Allowed
(2)
Not Allowed Rejected Rejected Rejected Not Allowed
Controller in Hard
Run Mode
(3)
Rejected Not Allowed Not Allowed Rejected Rejected Rejected Not Allowed
(1) Ethernet configuration includes IP address, subnet mask, gateway, port speed/duplex and so on.
(2) Difference between Not Allowed and Rejected is that Not Allowed activities can only be done during offline while Rejected activities can be performed but do not take effect.
(3) Hard Run Mode can only be in Micro830, Micro850 and Micro870 controllers with Mode switch to RUN.

 Loading...
Loading...











