Reading the data
When using the electron microscope, the data, represented by an electric charge, becomes visible. It is possible
to read the whole device memory.
Micro probing and internal fault injection
Micro probing consists in interacting with the device at metal layer level. Thin electrodes are used to establish an
electrical contact directly with the surface of the device so that the attacker can observe, manipulate, and interfere
with it while the device is running.
Device modification
More sophisticated tools can be used to perform attacks. FIB (focused ion beam) workstations, for example,
simplify the manual probing of deep metal and polysilicon lines. They also can be used to modify the device
structure by cutting existing or creating new interconnection lines and even new transistors.
3.4 IoT system attack examples
This section presents typical examples of attacks on an IoT system. Fortunately, most of these attacks can be
countered by enabling security feature (hardware countermeasures) and secure application architecture (software
countermeasures). The countermeasures are detailed in the next sections.
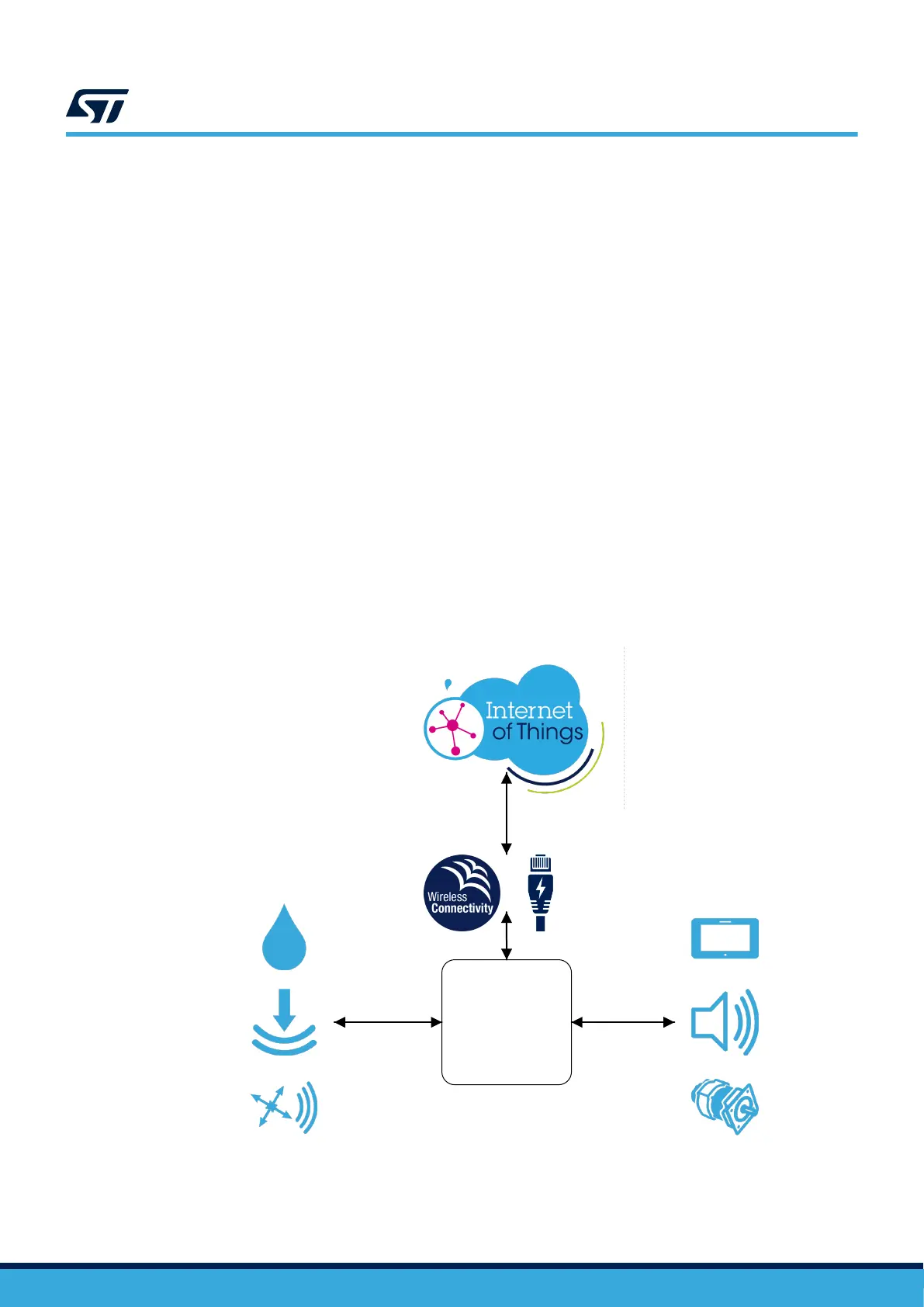
An IoT system is built around a STM32 microcontroller with connectivity systems (such as Ethernet, Wi-Fi
®
,
Bluetooth
®
Low Energy or ,LoRa
®
,) and sensors and/or actuators (see the figure below). The microcontroller
handles the application, data acquisition and communications with a cloud service. The microcontroller may also
be responsible for the system maintenance through firmware update and integrity check.
Figure 2. IoT system
DT50946V1
STM32
Connectivity
Sensors
Actuators
AN5156
IoT system attack examples
AN5156 - Rev 8
page 12/56

 Loading...
Loading...