Appendix A Cryptography - Main concepts
Integrity, authentication, and confidentiality
The objectives of cryptography are threefold:
• Confidentiality: protection of sensitive data against unauthorized read accesses
• Authentication: guarantee of the message sender identity
• Integrity: detection of any message corruption during transmission
To meet these objectives, all secure data flows rely on more or less complex combinations of the below
algorithms:
• Secret key/symmetric cryptography
• Public key/asymmetric cryptography
• Hashing
These algorithms are described in this appendix.
A.1 Secret key algorithms
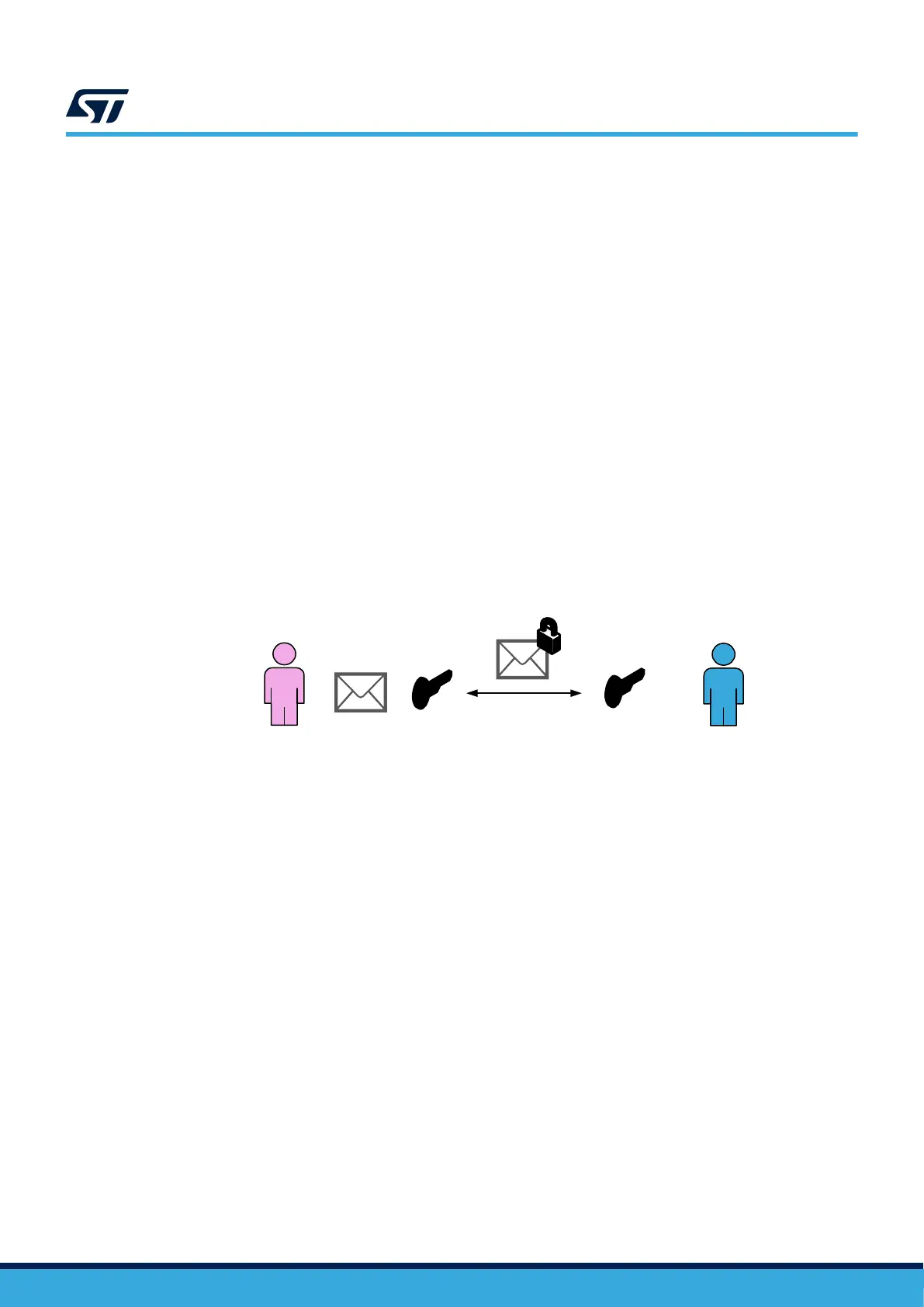
This family of algorithms ensures confidentiality by ciphering a clear plain text with a secret key shared between
the transmitter and the receiver. This technique is referred to as symmetric cryptography because the same key is
used for ciphering and deciphering.
Figure 15. Symmetric cryptography
DT50955V1
John Doe1
Secret key
Secret key
John Doe2
The inherent weakness of these algorithms is the key sharing between both parties. It may not be an issue in
secure environments (such as manufacturing plants), but when both parties are distant, the key transfer becomes
a challenge.
Among all secret key algorithms, block-based algorithms are very common since they can be efficiently
accelerated by hardware or software parallel implementations. Typical AES (advanced encryption standard)
algorithms operate on clear blocks of 128 bits. They produce ciphered blocks of the same length using keys
of 128, 192, or 256 bits. The different ways to chain consecutive blocks are called “mode of operations”. They
include cipher block chaining (CBC), counter mode (CTR) and Galois counter mode (GCM).
Since these algorithms are deterministic, they always mix input data with a random value, known as nonce, used
only for one session as initialization vector.
AN5156
Cryptography - Main concepts
AN5156 - Rev 8
page 45/56

 Loading...
Loading...