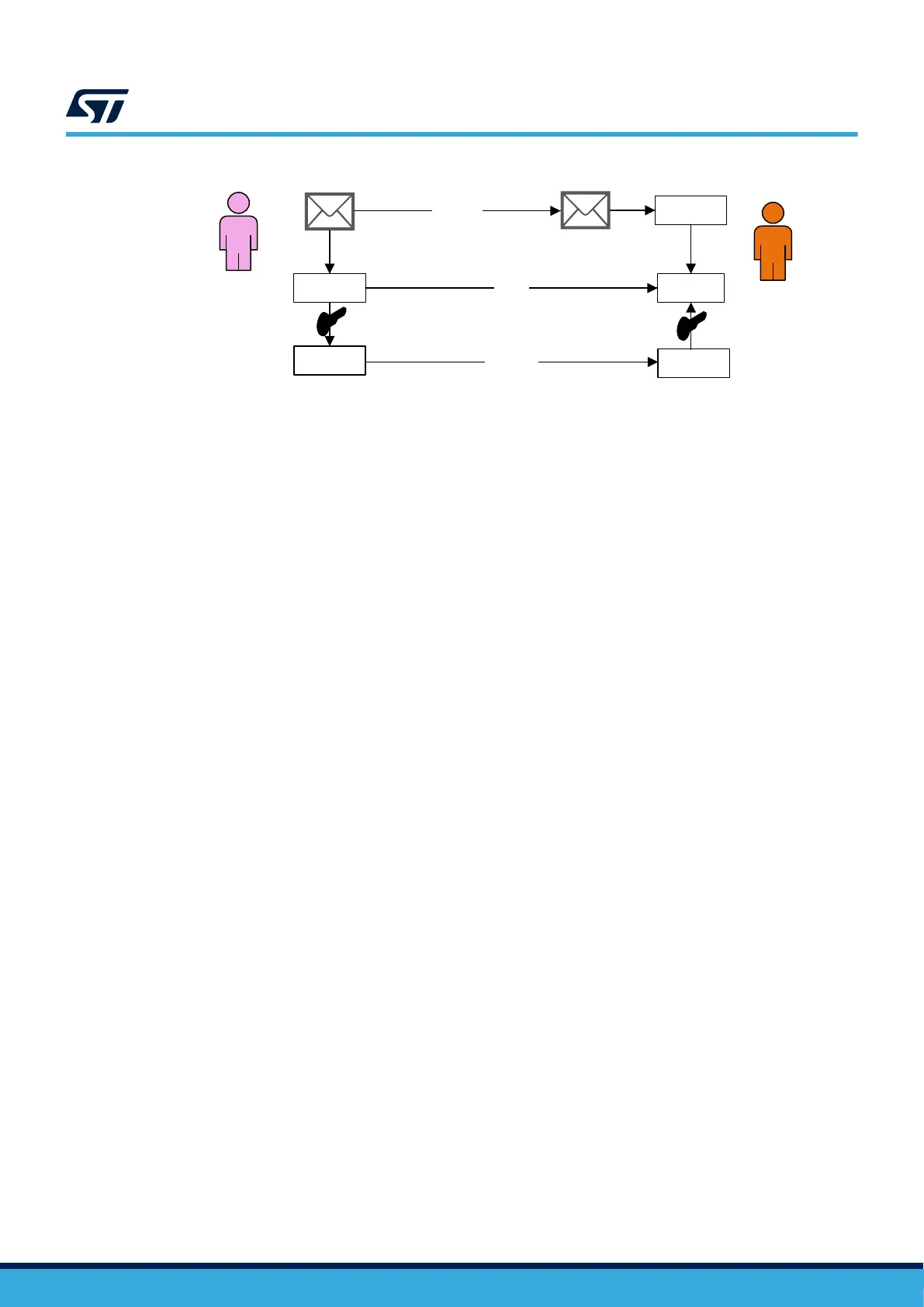
Figure 20. Signature generation with public key algorithm
DT50960V1
HASH
HASH
=?
John Doe1
John Doe2
Signature
Digest
Message
Signature
Signature
Private
key
Public
key
Certificate
A certificate is related to public key algorithms. It authenticates the public key in an asymmetric transfer. It is used
to counteract usurpation by an attacker that substitutes the right public key by his own key. A certificate consists in
the public key signed by a certificate authority (CA) private key. This CA is considered as fully trusted.
In addition to the public key, the certificate also contains version numbers, validity period and some IDs.
AN5156
MAC or signature and certificate
AN5156 - Rev 8
page 48/56

 Loading...
Loading...