Architecture
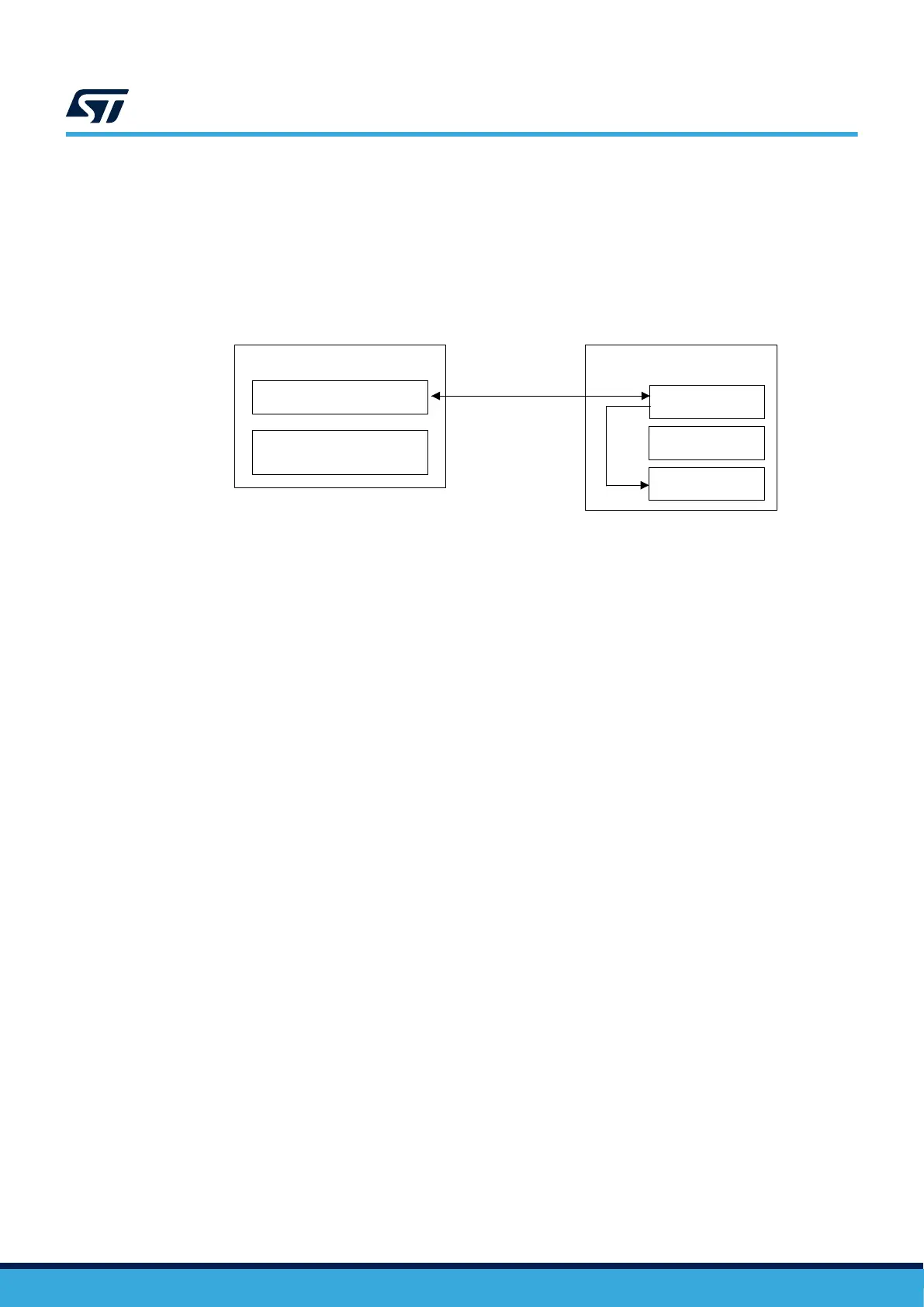
An SFU transfer involves two entities: the firmware owner (OEM) and the device to be updated (see the figure
below). As the communication channel is generally considered as nonsecure since it is subject to eavesdropping,
the overall security responsibility is shared between the sender (firmware owner server) and the receiver (the
device).
Figure 7. Secure server/device SFU architecture
DT50951V1
Secure server/HSM
Device STM32xx
Encrypted and signed
new firmware
STM32 MCU
Current firmware
New firmware
SFU firmware
SFU control software
Communication
channel
Application
From OEM side, a secure server is maintained that is responsible for sending the encrypted (if confidentiality is
required) and signed firmware to an authenticated device.
The SFU application running on device is in charge of the following:
• authentication and integrity checking of the loaded image before installing it
• decrypting the new firmware if confidentiality is required
• checking the new firmware version (anti-rollback mechanism)
5.3.3 Configurations
The ST proprietary SBSFU is very configurable. The most important configuration option is the choice to use
a single or dual image handling of application code. Each has a separate example. Single image leaves more
space for application code. Two or more images add some advanced features to the image handling.
The second most important option is the cryptographic scheme selection. There are usually the following choices:
• ECDSA asymmetric cryptography for firmware verification with AES-CBC or AES-CTR symmetric
cryptography for firmware encryption
• ECDSA asymmetric cryptography for firmware verification without firmware encryption
• X509 certificate-based ECDSA asymmetric cryptography for firmware verification without firmware
encryption
• AES-GCM symmetric cryptography for both firmware verification and encryption
For more details, see the document [9] or the document Integration guide for the X
‑
CUBE
‑
SBSFU STM32Cube
Expansion Package (AN5056).
5.4
Arm TF-M solution
Arm trusted firmware existed for chips based on Cortex-A when the secure Cortex-M33 core was introduced with
Armv8-M architecture. A more compact TF-M open source implementation of PSA standard was provided as a
reference secure firmware framework.
For STMicroelectronics MCUs that take advantage of the Armv8 architecture (such as STM32H5, STM32L5, and
STM32U5 devices), the SBSFU is replaced with the TF-M based solution.
For a documentation on TF-M itself, refer to the UM2851, and use Arm resources as well as the code comments.
For guidance on TF-M integration on the STM32L5 and STM32U5 devices, refer to the user manuals Getting
started with STM32CubeL5 TF-M application (UM2671) or Getting started with STM32CubeU5 TF-M application
(UM2851).
Refer to document [7] for a detailed comparison when migrating from X-CUBE-SBSFU package SBSFU to TF-M.
AN5156
Arm TF-M solution
AN5156 - Rev 8
page 25/56

 Loading...
Loading...