using a 128/192/256-bit key.
Integrity
Verification
Algorithm
Select a verification algorithm applied to an IKE session.
The router supports the following verification algorithms:
MD5 (Message Digest Algorithm): Generate a 128-bit message digest for a message to
prevent this message from being falsified.
SHA1 (Secure Hash Algorithm): Generate a 160-bit message digest for a message. It is
more difficult to crack SHA1than to crack MD5.
Diffie-Hellman algorithm group information that is used to generate a session key to encrypt
an IKE tunnel.
The PFS (Perfect Forward Secrecy) feature enables IKE Stage 2 negotiation to generate a new
key material that has no association with any key material generated in Stage 1 negotiation.
Therefore, the Stage 2 key is safe even if the IKE1 Stage 1 key is cracked. If PFS is not used,
the Stage 2 key will be generated according to the key material generated in Stage 1. Once
the Stage 1 key is cracked, the Stage 2 key used to protect communication data will also be
placed in jeopardy. This will seriously threaten communication security of both parties.
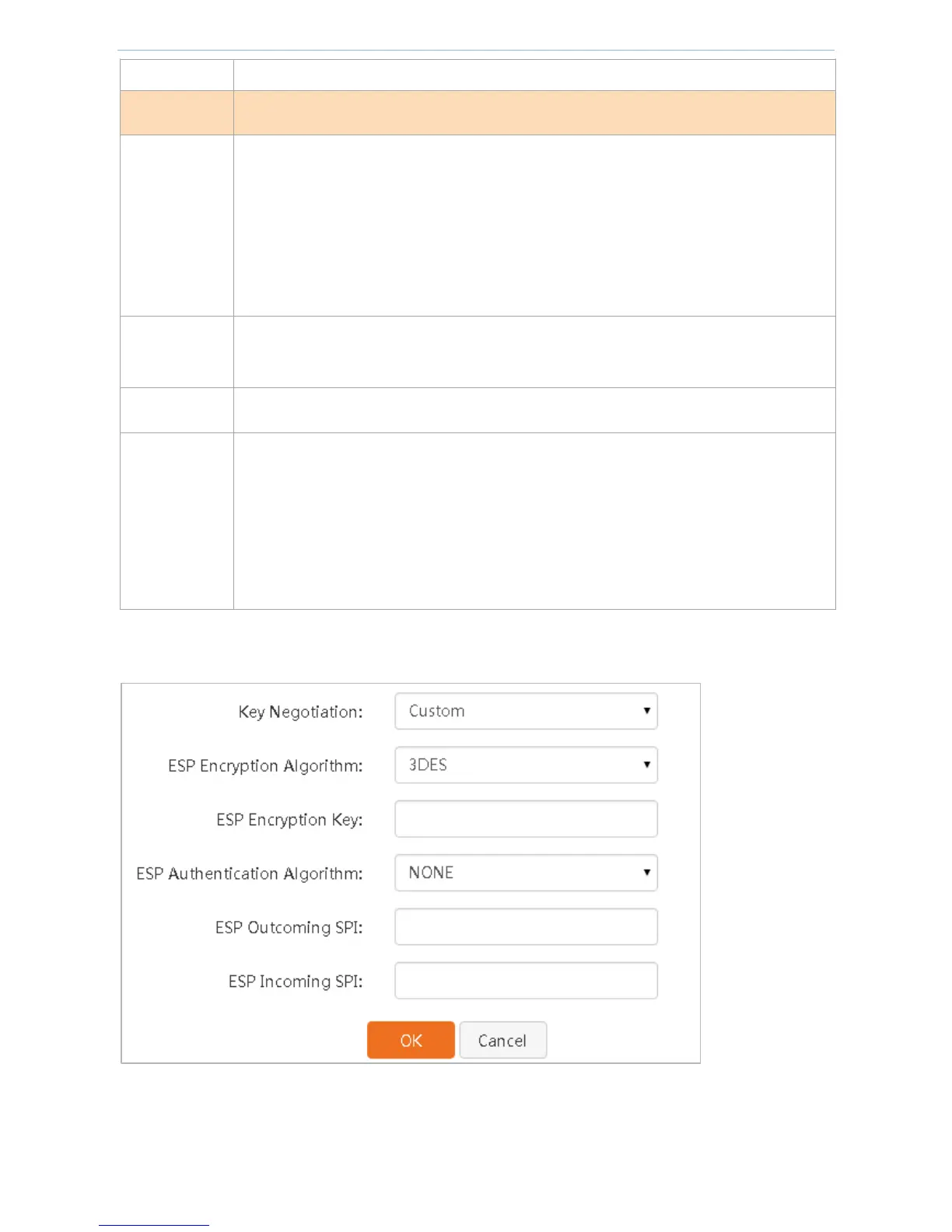
Key Negotiation — Custom
When key negotiation is Custom, the page is shown in the figure below.
 Loading...
Loading...