DVX IPPBX
108 / 130
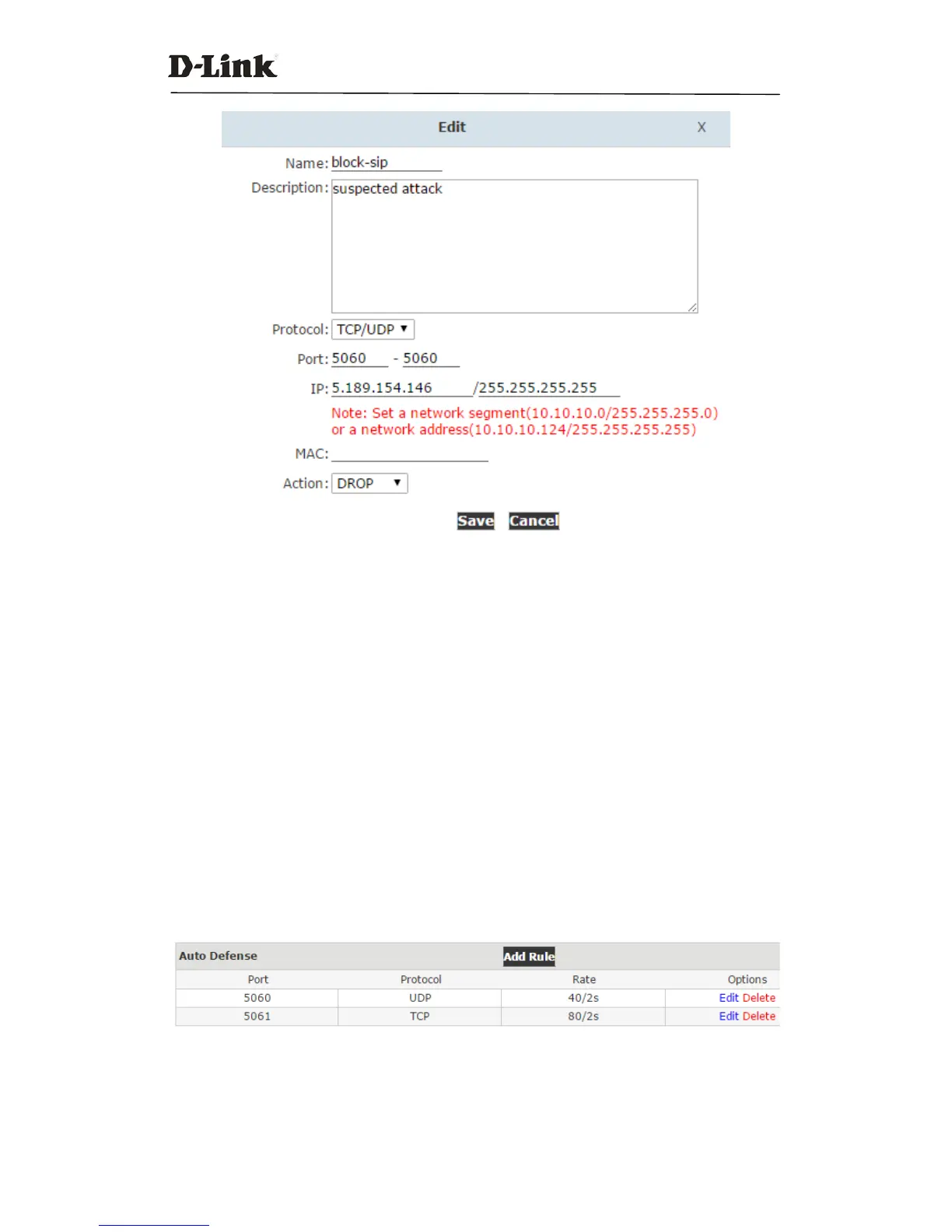
Name: A name for this rule.
Description: Optional, you may describe why this rule has been created.
Protocol: Transmission protocol, UDP, TCP or UDP with TCP.
Port: Service port number.
IP: Can be an IP address or a network address.
MAC:Action to be taken according to the Mac address of a device instead of its IP
Address.This only works with devices within the same local network because Mac address
are not routable.
Action:Select “Drop” to block and “Accept” to grant.
Auto Defense
DVX IPPBX system uses Fail2Ban to perform intrusion detection,iptables is used for blocking any
attack attempts.
Fail2Ban is an intrusion prevention framework written in the Python programming language. It
works by reading Asterisk logs and some other logs in the IPPBX system, anduses iptables profiles
to block brute-force attempts.
In the Auto Defense section you can define some custom rules to help the IPPBX system
determine brute-force attempts.
Click “Add Rule” button to add a new custom rule.
 Loading...
Loading...