IPSec VPN IPSec VPN concentrators
FortiGate-50A Installation and Configuration Guide 199
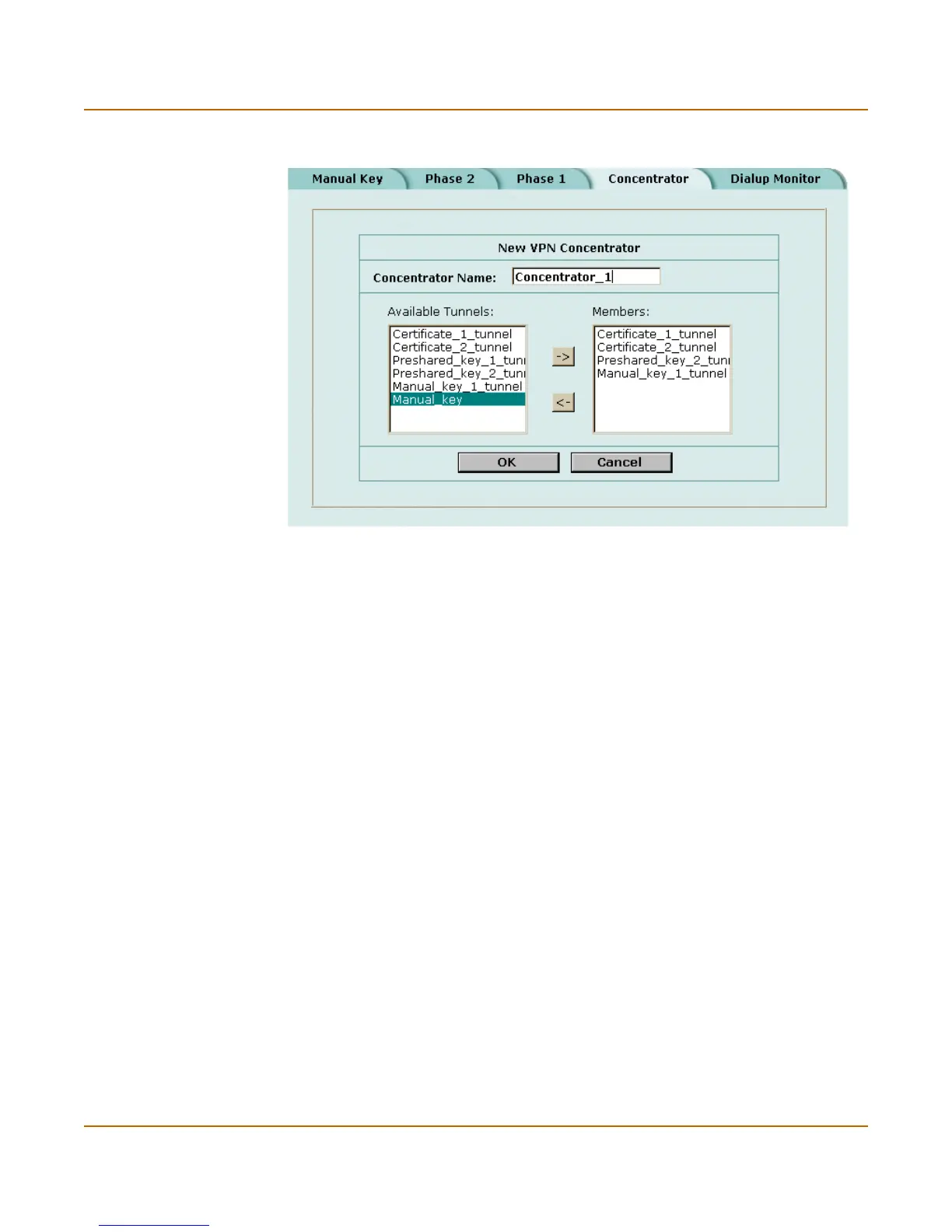
Figure 26: Adding a VPN concentrator
VPN spoke general configuration steps
A remote VPN peer that functions as a spoke requires the following configuration:
• A tunnel (AutoIKE phase 1 and phase 2 configuration or manual key configuration)
for the hub.
• The source address of the local VPN spoke.
• The destination address of each remote VPN spoke.
• A separate outbound encrypt policy for each remote VPN spoke. These policies
allow the local VPN spoke to initiate encrypted connections.
• A single inbound encrypt policy. This policy allows the local VPN spoke to accept
encrypted connections.
To create a VPN spoke configuration
1 Configure a tunnel between the spoke and the hub.
Choose between a manual key tunnel or an AutoIKE tunnel.
• To add a manual key tunnel, see “Manual key IPSec VPNs” on page 181.
• To add an AutoIKE tunnel, see “AutoIKE IPSec VPNs” on page 182.
2 Add the source address. One source address is required for the local VPN spoke.
See “Adding a source address” on page 194.
3 Add a destination address for each remote VPN spoke. The destination address is the
address of the spoke (either a client on the Internet or a network located behind a
gateway).
See “Adding a destination address” on page 194

 Loading...
Loading...











