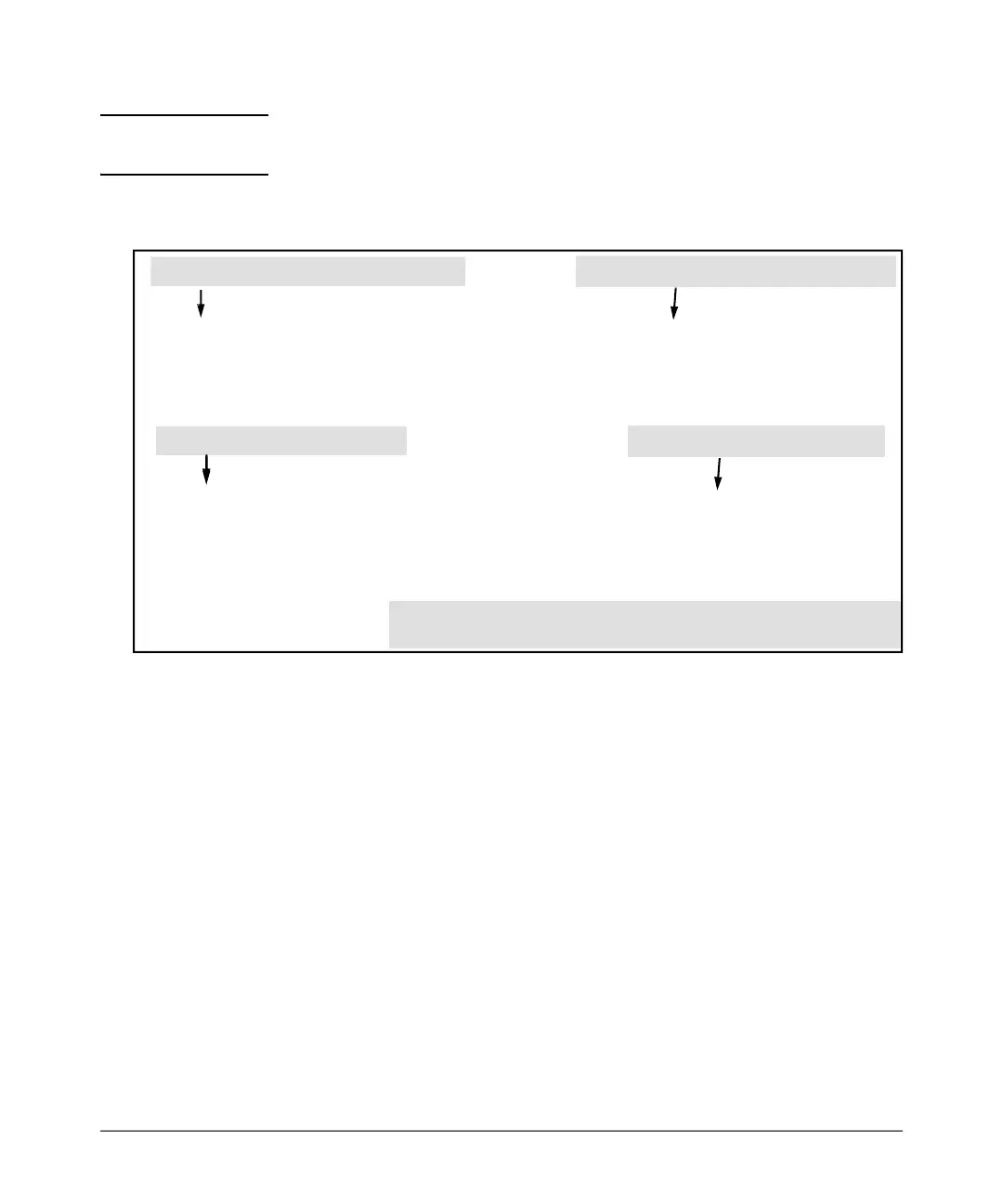
Client’s Password (MAC Authentication)
RADIUS Authentication and Accounting
Configuring a RADIUS Server To Specify Per-Port CoS and Rate-Limiting Services
Note For syntax details on RADIUS-based ACLs, refer to “Format Details for ACEs
Configured in a RADIUS-Based ACL” on page 6-40.
Client’s Username (802.1X or Web Authentication)
Client’s Password (802.1X or Web Authentication)
mobile011 Auth-Type:= Local, User-Password == run101112
HP-IP-FILTER-RAW = “permit in tcp from any to 10.10.10.101”,
HP-IP-FILTER-RAW += “deny in tcp from any to any”,
HP-IP-FILTER-RAW += “permit in ip from any to any”
)
)
Client’s Username (MAC Authentication
Client’s Password (MAC Authentication
08E99C4F0019 Auth-Type:= Local, User-Password == 08E99C4F0019
HP-IP-FILTER-RAW = “permit in tcp from any to 10.10.10.101”,
HP-IP-FILTER-RAW += “deny in tcp from any to any”,
HP-IP-FILTER-RAW += “permit in ip from any to any”
Note that when the client MAC address is used for authentication, this address is used
in both the username and password spaces in the entry.
Figure 6-15. Example of Configuring the FreeRADIUS Server To Support ACLs for the Indicated Clients
Format Details for ACEs Configured in a RADIUS-Based ACL.
Any instance of a RADIUS-Based ACL is structured to filter authenticated
client traffic as follows:
■ Applies only to inbound client traffic on the switch port the authenti-
cated client is using.
■ Allows only the “any” source address (for any authenticated IP device
connected to the port).
■ Applies to all IP traffic from the authenticated client or to a specific
type of IP traffic type from the client. Options include TCP, UDP, or
any other type of IP traffic that is identified by an IP protocol number.
(More information on protocol numbers is provided in the following
ACL syntax description.) Has one of the following destination types:
• A specific IP address
• A contiguous series of IP address or an entire subnet
6-40

 Loading...
Loading...











