Configuring Port-Based and Client-Based Access Control (802.1X)
How RADIUS/802.1X Authentication Affects VLAN Operation
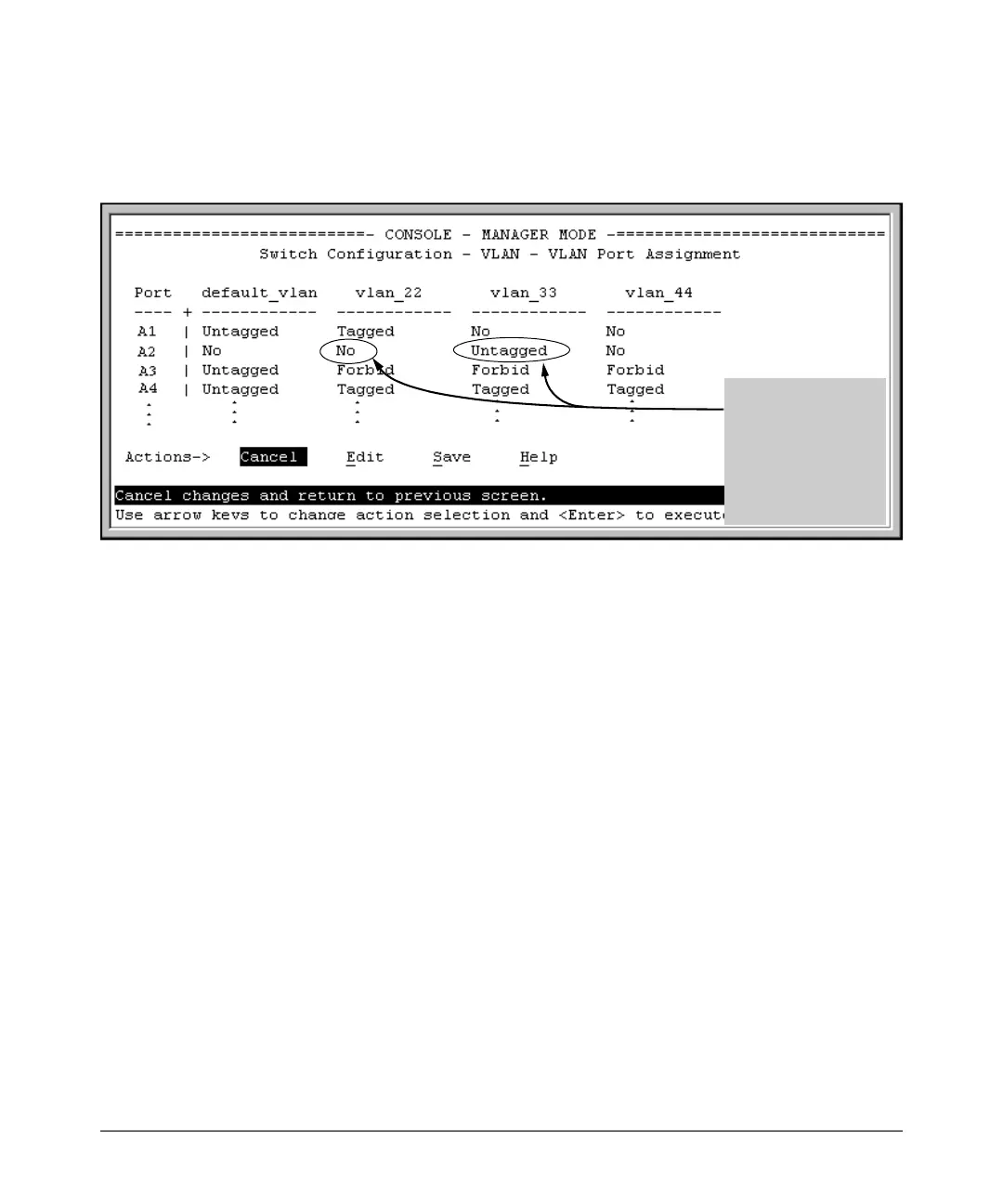
For example, suppose that a RADIUS-authenticated, 802.1X-aware client on
port A2 requires access to VLAN 22, but VLAN 22 is configured for no access
on port A2, and VLAN 33 is configured as untagged on port A2:
AnScenario:
authorized 802.1X
client requires access
to VLAN 22 from port
A2. However, access
to VLAN 22 is blocked
(not untagged or
tagged) on port A2 and
Figure 10-7. Example of an Active VLAN Configuration
In figure 10-7, if RADIUS authorizes an 802.1X client on port A2 with the
requirement that the client use VLAN 22, then:
■ VLAN 22 becomes available as Untagged on port A2 for the duration of
the session.
■ VLAN 33 becomes unavailable to port A2 for the duration of the session
(because there can be only one untagged VLAN on any port).
You can use the show vlan < vlan-id > command to view this temporary change
to the active configuration, as shown below:
■ You can see the temporary VLAN assignment by using the show vlan < vlan-
id > command with the < vlan-id > of the static VLAN that the authenticated
client is using.
10-50

 Loading...
Loading...











