SSH Key Management
Secure Shell (SSH) is UNIX-based command interface and network protocol used to gain secure access to a remote computer,
execute commands on a remote machine or to transfer files between machines. It was designed as a replacement for Telnet and
other insecure remote shell protocols which send information, including passwords, as plain text.
SSH uses RSA public key cryptography for both connection and authentication. Two common ways of using SSH are:
Use automatically generated public-private key pairs to encrypt the network connection and then use password
authentication to log on.
Use a manually generated public-private key pair to perform the authentication and allow users or programs to log in
without using a password.
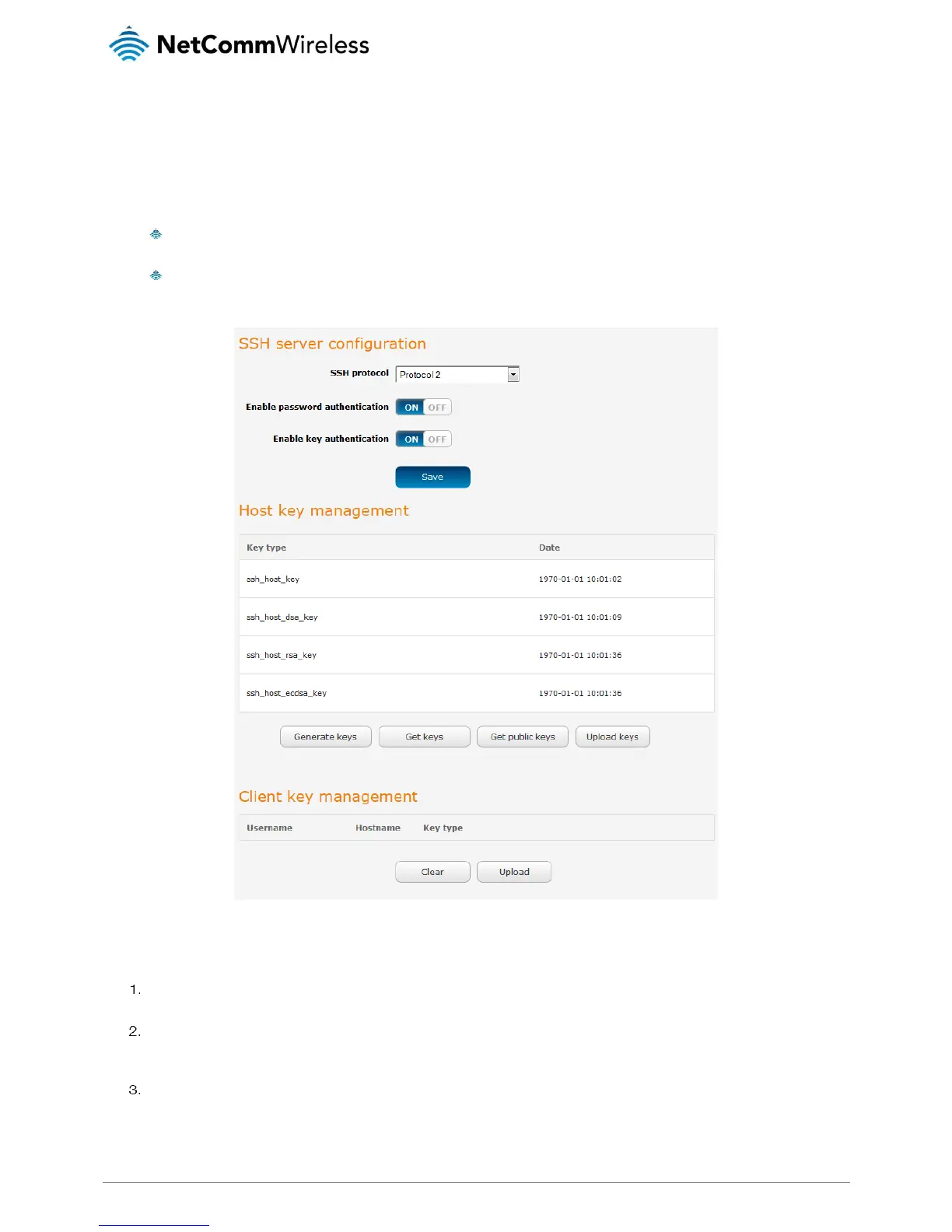
Figure 137 - SSH Server Configuration
SSH Server Configuration
To configure the SSH server settings:
Use the SSH Protocol drop down list to select the protocol that you want to use. Protocol 2 is more recent and is
considered more secure.
Select the types of authentication you want to use by clicking the Enable password authentication and Enable key
authentication toggle keys on or off. Note that you may have both authentication methods on but you may not turn them
both off.
Click the Save button to confirm your settings.
 Loading...
Loading...