WorkCentre 7220-7225 Information Assurance Disclosure Paper
Ver. 1.0, January 2013 Page 31 of 61
3.2.2.2. SMB Authentication (Windows 2000/Windows 2003/Windows 2008)
The authentication steps vary somewhat, depending on the network configuration. Listed below are 3 network
configurations and the authentication steps.
Basic Network Configuration: Device and Domain Controller are on the same
Subnet
Authentication Steps:
1) The device broadcasts an authentication request that is answered by the Domain Controller.
2) The Domain Controller responds back to the device whether or not the user was successfully
authenticated.
If (2) is successful, steps 3 – 5 proceed as described in steps 4 – 6 of the Kerberos section.
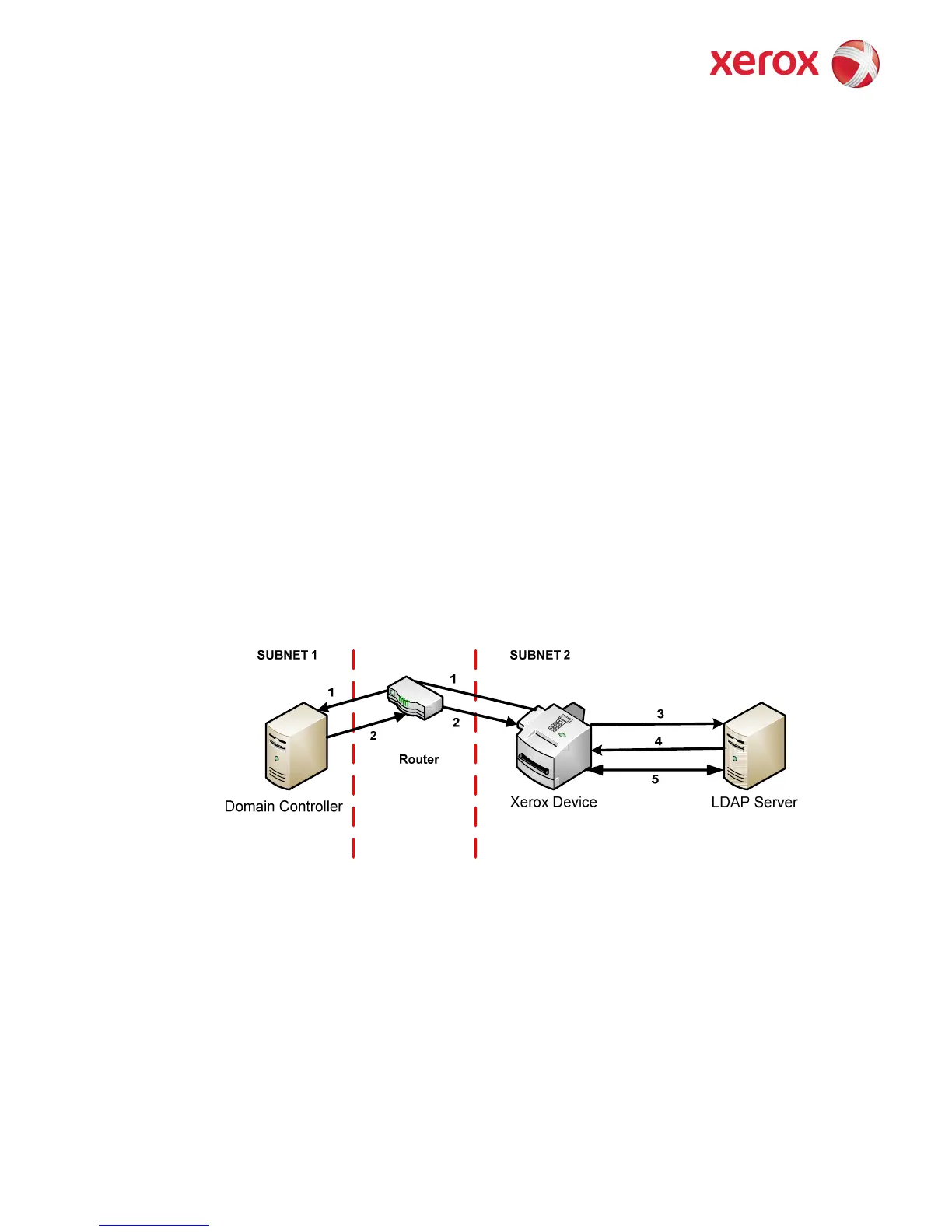
Device and Domain Controller are on different Subnets, SA defines IP Address of
Domain Controller
Authentication Steps:
1) The device sends an authentication request directly to the Domain Controller through the router using
the IP address of the Domain Controller.
2) The Domain Controller responds back to the device through the router whether or not the user was
successfully authenticated.
If (2) is successful, steps 3 – 5 proceed as described in 4 - 6 of Kerberos section.

 Loading...
Loading...