10-42
Catalyst 3750 Switch Software Configuration Guide
OL-8550-02
Chapter 10 Configuring IEEE 802.1x Port-Based Authentication
Configuring IEEE 802.1x Authentication
This example shows how to enable AAA, use RADIUS authentication and enable device tracking:
Switch(config) configure terminal
Switch(config)# aaa new-model
Switch(config)# aaa authentication login default group radius
Switch(config)# aaa authorization auth-proxy default group radius
Switch(config)# radius-server host key key1
Switch(config)# radius-server attribute 8 include-in-access-req
Switch(config)# radius-server vsa send authentication
Switch(config)# ip device tracking
Switch(config) end
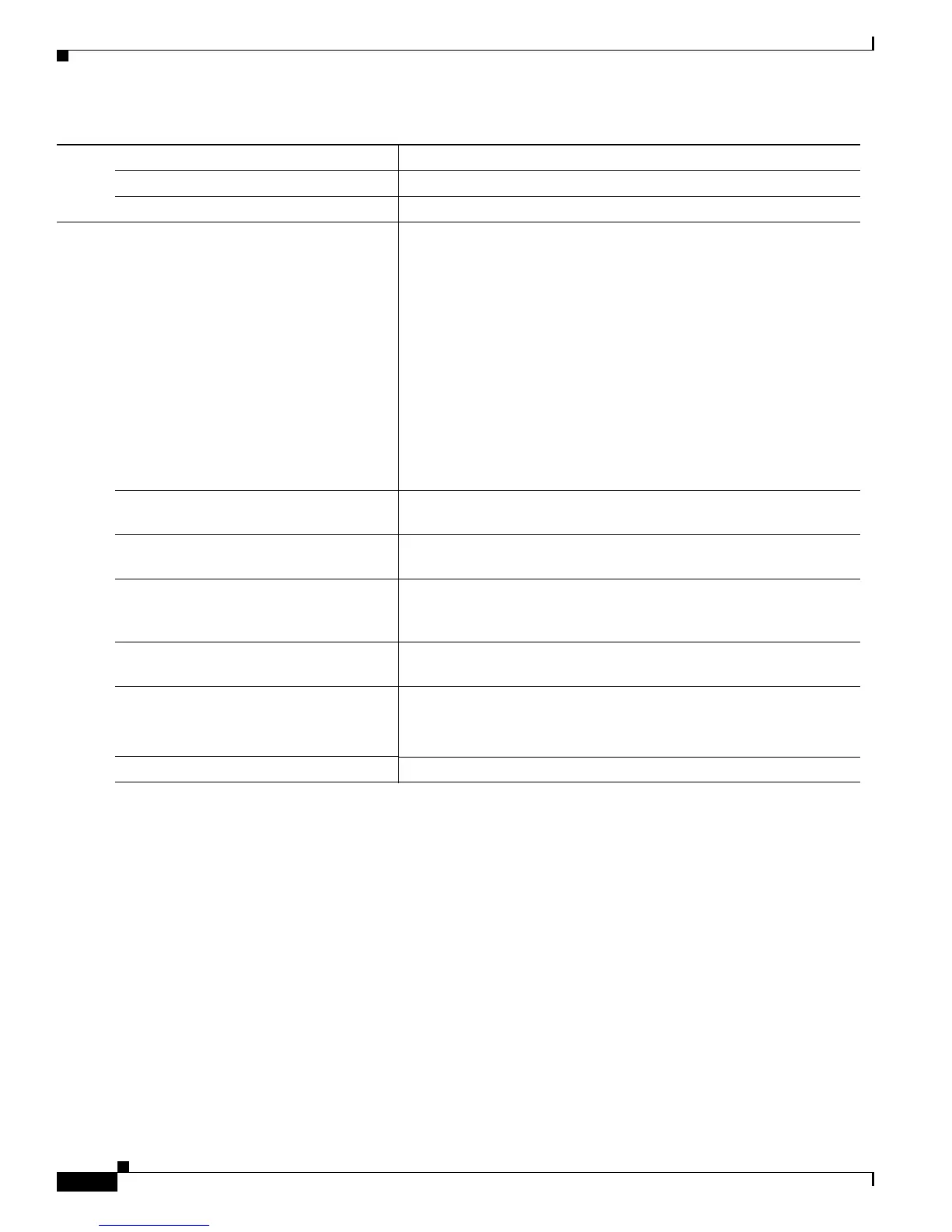
Beginning in privileged EXEC mode, follow these steps to configure a port to use web authentication:
Command Purpose
Step 1
configure terminal Enter global configuration mode.
Step 2
aaa new-model Enable AAA.
Step 3
aaa authentication login default group
radius
Use RADIUS authentication. Before you can use this authentication
method, you must configure the RADIUS server. For more
information, see Chapter 9, “Configuring Switch-Based
Authentication.”
The console prompts you for a username and password on future
attempts to access the switch console after entering the aaa
authentication login command. If you do not want to be prompted for
a username and password, configure a second login authentication
list:
Switch# config t
Switch(config)# aaa authentication login line-console none
Switch(config)# line console 0
Switch(config-line)# login authentication line-console
Switch(config-line)# end
Step 4
aaa authorization auth-proxy default
group radius
Use RADIUS for authentication-proxy (auth-proxy) authorization.
Step 5
radius-server host key radius-key Specify the authentication and encryption key for RADIUS
communication between the switch and the RADIUS daemon.
Step 6
radius-server attribute 8
include-in-access-req
Configure the switch to send the Framed-IP-Address RADIUS
attribute (Attribute[8]) in access-request or accounting-request
packets.
Step 7
radius-server vsa send authentication Configure the network access server to recognize and use
vendor-specific attributes (VSAs).
Step 8
ip device tracking Enable the IP device tracking table.
To disable the IP device tracking table, use the no ip device tracking
global configuration commands.
Step 9
end Return to privileged EXEC mode.
 Loading...
Loading...











