6-7
Cisco Wireless ISR and HWIC Access Point Configuration Guide
OL-6415-04
Chapter 6 Configuring Authentication Types
Understand Authentication Types
Note Unicast and multicast cipher suites advertised in WPA information element (and negotiated during
802.11 association) may potentially mismatch with the cipher suite supported in an explicitly assigned
VLAN. If the RADIUS server assigns a new vlan ID which uses a different cipher suite from the
previously negotiated cipher suite, there is no way for the access point and client to switch back to the
new cipher suite. Currently, the WPA protocol does not allow the cipher suite to be changed after the
initial 802.11 cipher negotiation phase. In this scenario, the client device is disassociated from the
wireless LAN.
See the “Assigning Authentication Types to an SSID” section on page 6-9 for instructions on configuring
WPA key management on your access point.
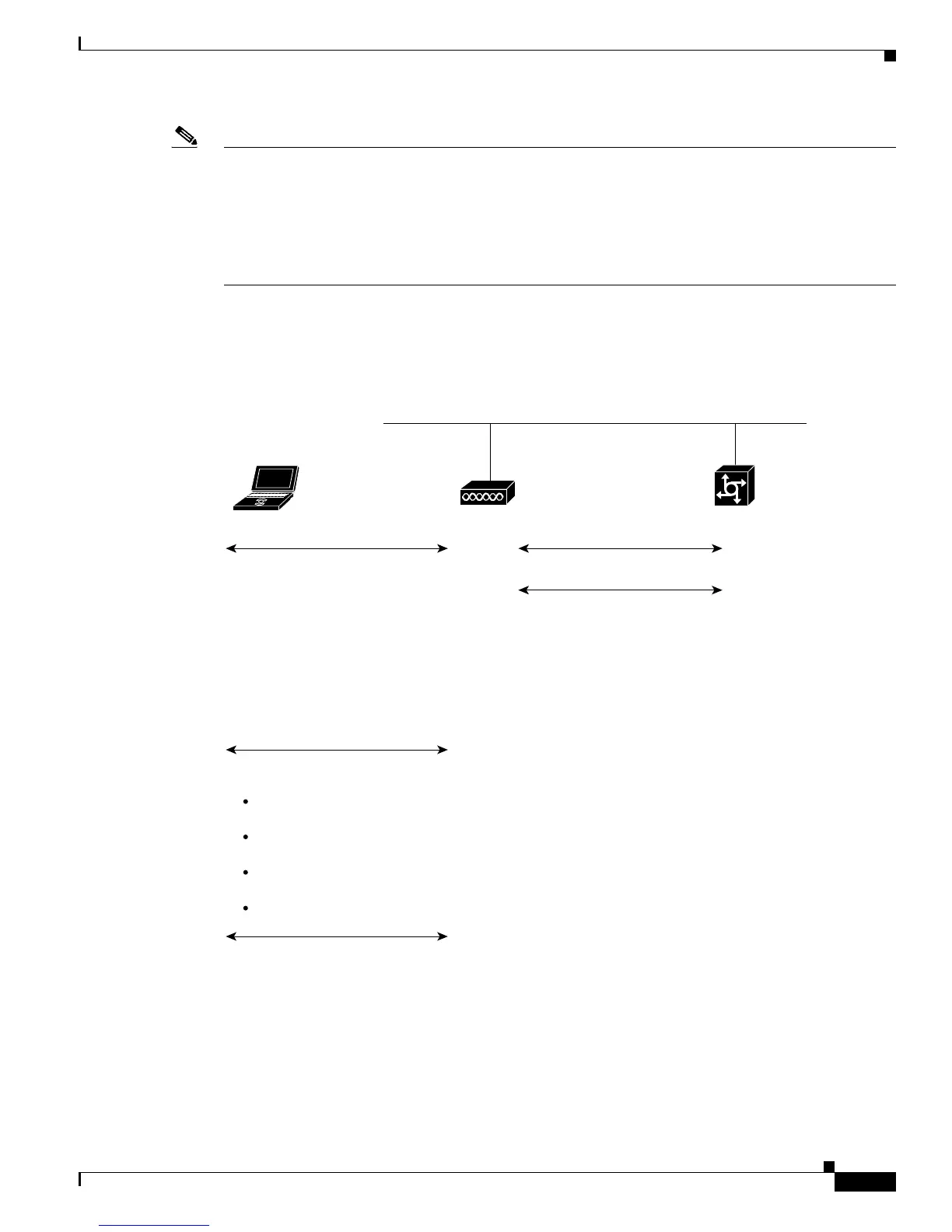
Figure 6-5 shows the WPA key management process.
Figure 6-5 WPA Key Management Process
88965
Client and server authenticate to each other, generating an EAP master key
Client device
Access point
Authentication
server
Wired LAN
Server uses the EAP master key to
generate a pairwise master key (PMK)
to protect communication between the
client and the access point. (However,
if the client is using 802.1x authentication
and both the access point and the client
are configured with the same pre-shared key,
the pre-shared key is used as the PMK and
the server does not generate a PMK.)
Client and access point complete
a four-way handshake to:
Client and access point complete
a two-way handshake to securely
deliver the group transient key from
the access point to the client.
Confirm that a PMK exists and that
knowledge of the PMK is current.
Derive a pairwise transient key from
the PMK.
Install encryption and integrity keys into
the encryption/integrity engine, if necessary.
Confirm installation of all keys.
 Loading...
Loading...











