1-2
Cisco TrustSec Configuration Guide
OL-22192-01
Chapter 1 Cisco TrustSec Overview
Information about Cisco TrustSec Architecture
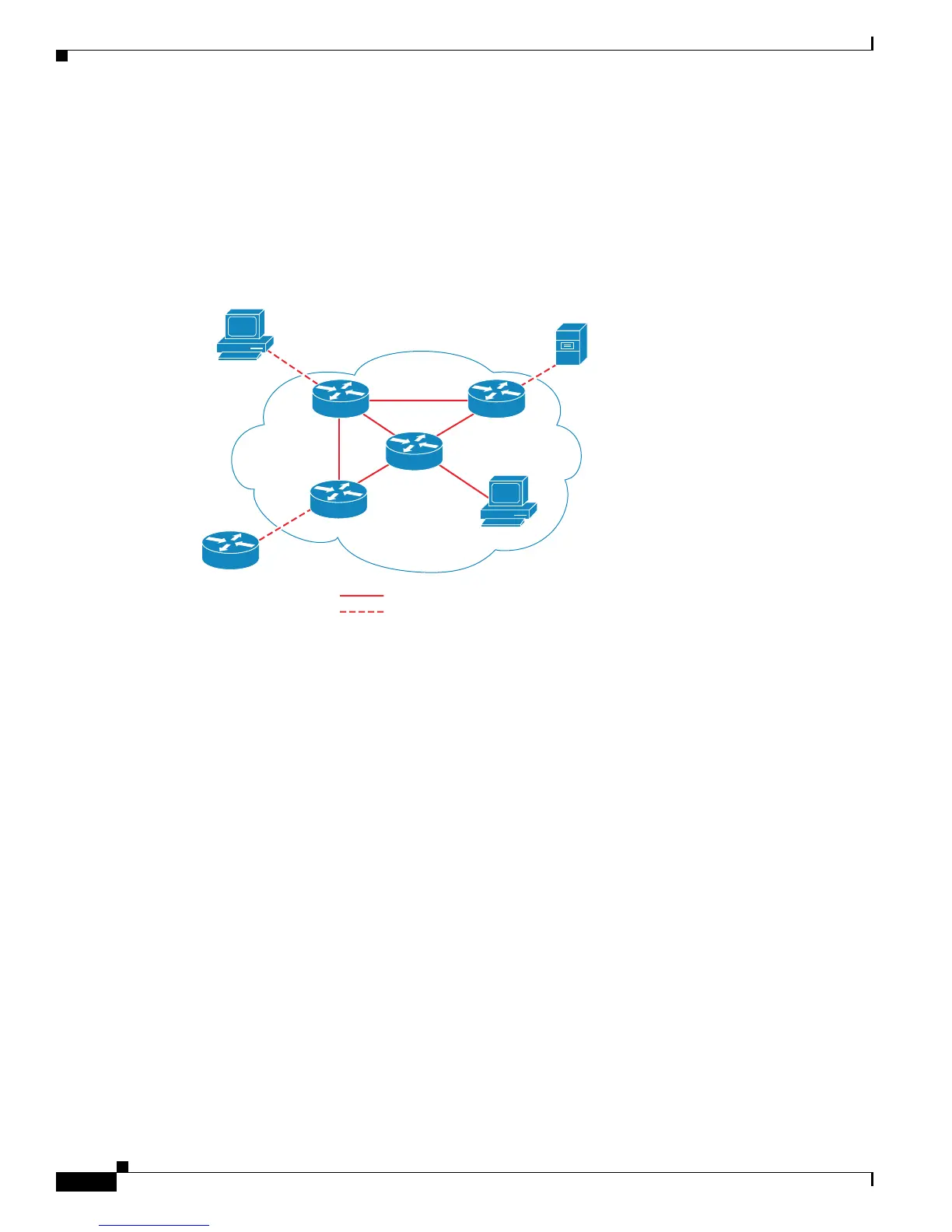
Figure 1-1 shows an example of a Cisco TrustSec domain. In this example, several networking devices
and an endpoint device are inside the Cisco TrustSec domain. One endpoint device and one networking
device are outside the domain because they are not Cisco TrustSec-capable devices or because they have
been refused access. The authentication server is considered to be outside of the Cisco TrustSec domain;
it is either a Cisco Identities Service Engine (Cisco ISE), or a Cisco Secure Access Control System
(Cisco ACS).
Figure 1-1 Cisco TrustSec Network Domain Example
Each participant in the Cisco TrustSec authentication process acts in one of the following roles:
• Supplicant—An unauthenticated device connected to a peer within the Cisco TrustSec domain, and
attempting to join the Cisco TrustSec domain.
• Authentication server—The server that validates the identity of the supplicant and issues the policies
that determine the supplicant’s access to services within the Cisco TrustSec domain.
• Authenticator—An authenticated device that is already part of the Cisco TrustSec domain and can
authenticate new peer supplicants on behalf of the authentication server.
When the link between a supplicant and an authenticator first comes up, the following sequence of events
typically occurs:
1. Authentication (802.1X)—The supplicant is authenticated by the authentication server, with the
authenticator acting as an intermediary. Mutual authentication is performed between the two peers
(supplicant and authenticator).
2. Authorization—Based on the identity information of the supplicant, the authentication server
provides authorization policies, such as security group assignments and ACLs, to each of the linked
peers. The authentication server provides the identity of each peer to the other, and each peer then
applies the appropriate policy for the link.
3. Security Association Protocol (SAP) negotiation—When both sides of a link support encryption, the
supplicant and the authenticator negotiate the necessary parameters to establish a security
association (SA).
When all three steps are complete, the authenticator changes the state of the link from the unauthorized
(blocking) state to the authorized state, and the supplicant becomes a member of the Cisco TrustSec
domain.
Unprotected link
Protected
Switch 1
Switch 2
Switch
Host 1
Cisco TrustSec
253096
Authentication
Server (AS)
 Loading...
Loading...











