1-11
Cisco TrustSec Configuration Guide
OL-22192-01
Chapter 1 Cisco TrustSec Overview
Information about Cisco TrustSec Architecture
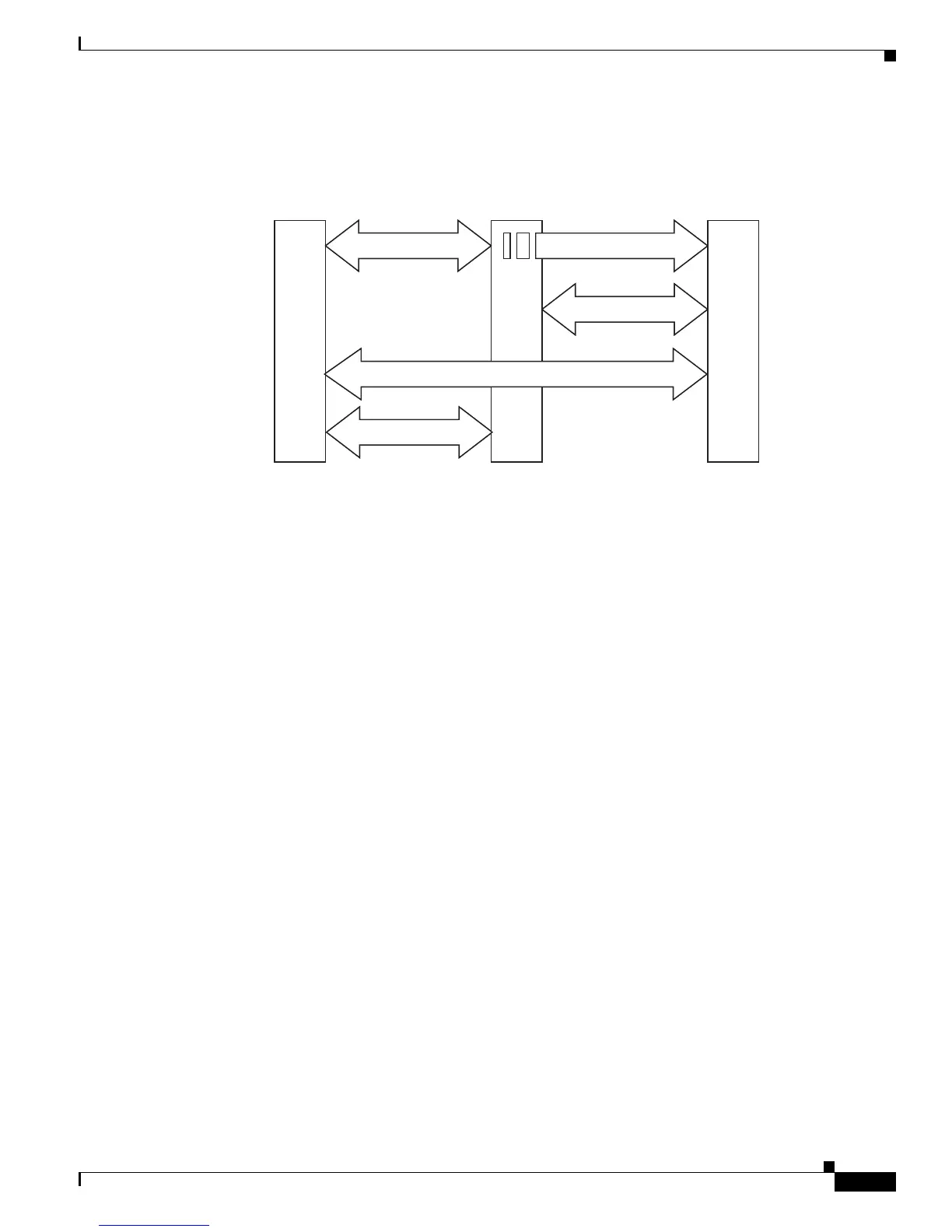
The NDAC and SAP negotiation process is shown in Figure 1-5.
Figure 1-5 NDAC and SAP Negotiation
Environment Data Download
The Cisco TrustSec environment data is a collection of information or policies that assists a device to
function as a Cisco TrustSec node. The device acquires the environment data from the authentication
server when the device first joins a Cisco TrustSec domain, although you might also manually configure
some of the data on a device. For example, you must configure the seed Cisco TrustSec device with the
authentication server information, which can later be augmented by the server list that the device
acquires from the authentication server.
The device must refresh the Cisco TrustSec environment data before it expires. The device can also cache
the environment data and reuse it after a reboot if the data has not expired.
The device uses RADIUS to acquire the following environment data from the authentication server:
• Server lists—List of servers that the client can use for future RADIUS requests (for both
authentication and authorization).
• Device SG—Security group to which the device itself belongs.
• Expiry timeout—Interval that controls how often the Cisco TrustSec device should refresh its
environment data.
SAP negotiation
authentication
authorization
authorization
authentication
supplican
Supplicant
Authentication Authentication
Authorization
Authorization
SAP negotiation
authentication
authorization
AT AS
Authentication Authentication
Authorization
Authorization
187007
 Loading...
Loading...











