allowed as mail attachments and new filetypes can be added
to the list. This same option is also available in the HTTP
ALG and a fuller description of how it works can be found in
Section 6.2.2, “The HTTP ALG”.
Anti-Virus Scanning
The NetDefendOS Anti-Virus subsystem can optionally scan
email attachments searching for malicious code. Suspect files
can be dropped or just logged. This feature is common to a
number of ALGs and is described fully in Section 6.4,
“Anti-Virus Scanning”.
6.2.7. The PPTP ALG
Why the PPTP ALG is Needed
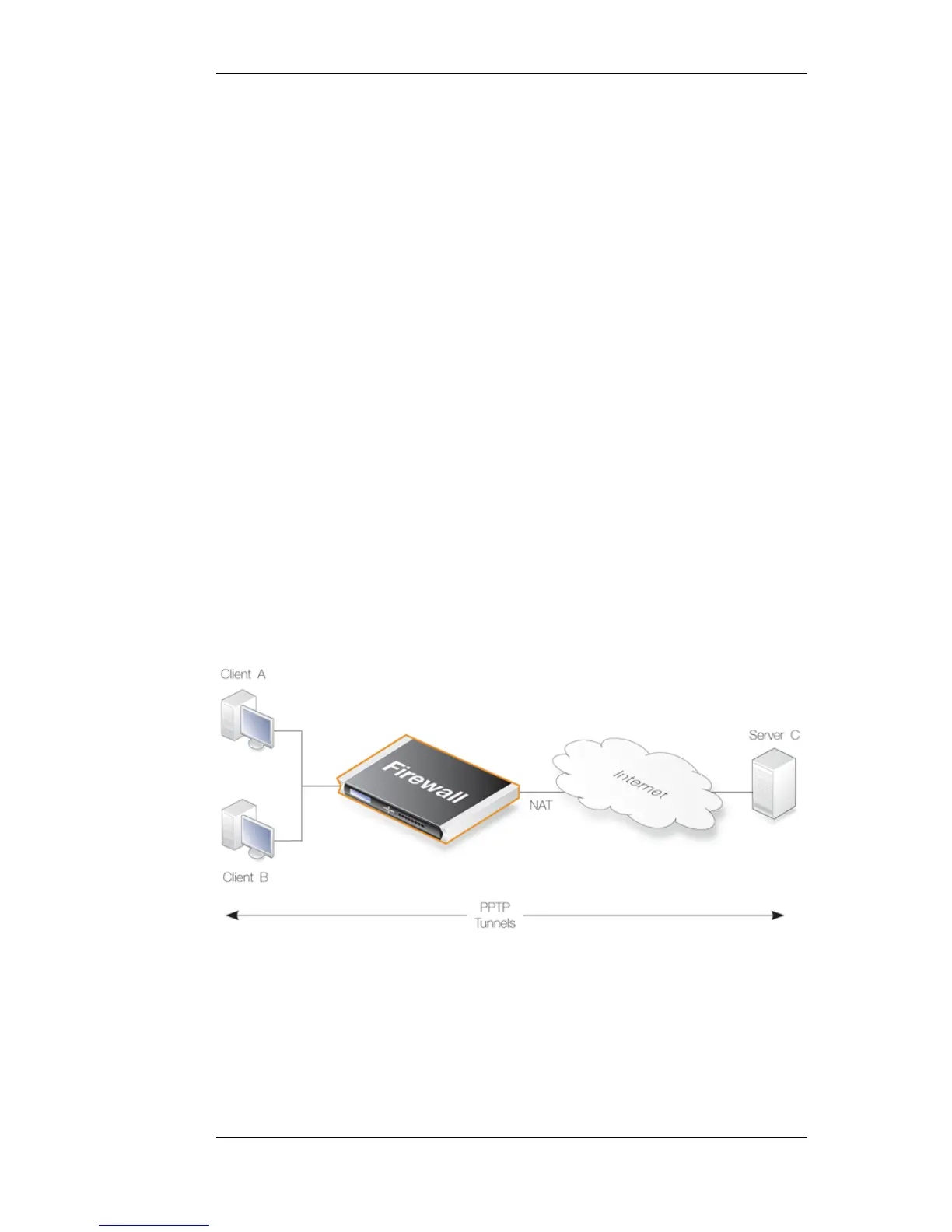
The PPTP ALG is provided to deal with a specific issue when PPTP tunnels are used with NAT.
Let us suppose we have two clients A and B on a protected inner network behind a NetDefend
Firewall. The firewall is connected to the external Internet and a NAT rule is defined to allow traffic
from the clients to flow to the Internet. Both clients will therefore appear to have from the same IP
address as they make connections to servers across the Internet.
One client A now establishes a PPTP tunnel to an external host C across the Internet. The tunnel
endpoints are the client and the external server. Because of the NAT IP rule, the tunnel connection
will appear to be coming from the external IP address on the firewall.
This first connection will be successful but when the second client B also tries to connect to the
same server C at the same endpoint IP address, the first connection for A will be lost. The reason is
that both clients are trying to establish a PPTP tunnel from the same external IP address to the same
endpoint.
Figure 6.6. PPTP ALG Usage
The PPTP ALG solves this problem. By using the ALG, the traffic from all the clients can be
multiplexed through a single PPTP tunnel between the firewall and the server.
PPTP ALG Setup
6.2.7. The PPTP ALG Chapter 6. Security Mechanisms
296
 Loading...
Loading...