User manual for poly-phase meter
37
18 Client management
The meter shall fully support DLMS Security as described in the 8
th
DLMS/COSEM Green Book and it can transmit the data with/without encryption and
authentication.
Several authentication mechanisms are used to authenticate communication
entities during AA establishment. Data transportation security is based on a role-based
security. Each role has its own access privileges. And all these authentication and
encryption algorithms are limited to security policy. Here as following is the list
with all the roles, their privileges and authentication mechanism:
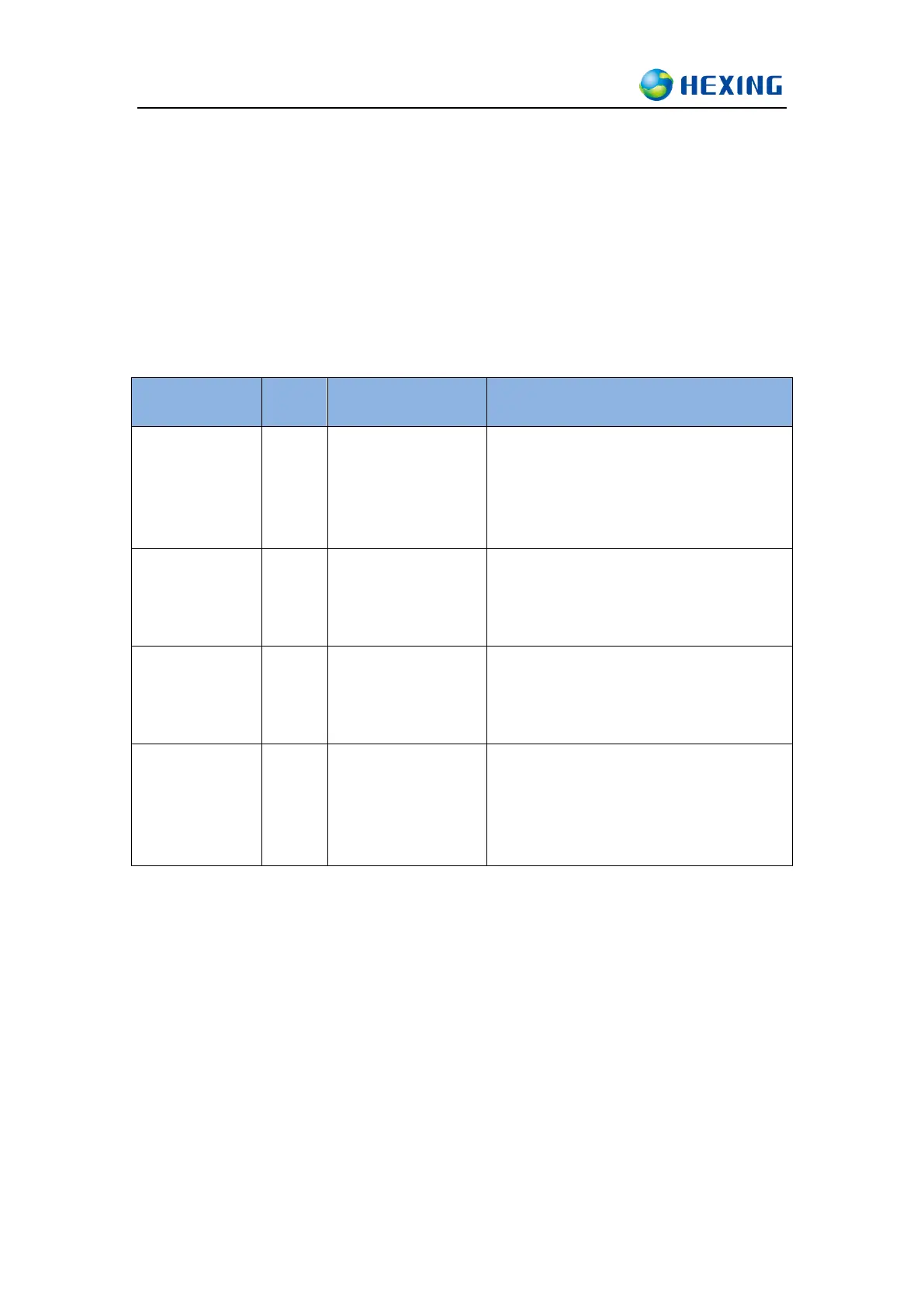
Read limited
meter information,
like the meter
serial number,
clock, etc.
Accessible via remote communication
and local interface without any
security
Read meter data
and parameters
Established with authentication HLS
(LLS backup)
Data transmission with none security,
or authentication and encryption
Read meter data,
configure meter
parameters and
control meter
Established with authentication HLS
(LLS backup)
Data transmission with none security,
or authentication and encryption
Receive broadcast
commands, and
push data
Accessible only via remote
communication
Always Established
Data transmission with none security,
or authentication and encryption
 Loading...
Loading...