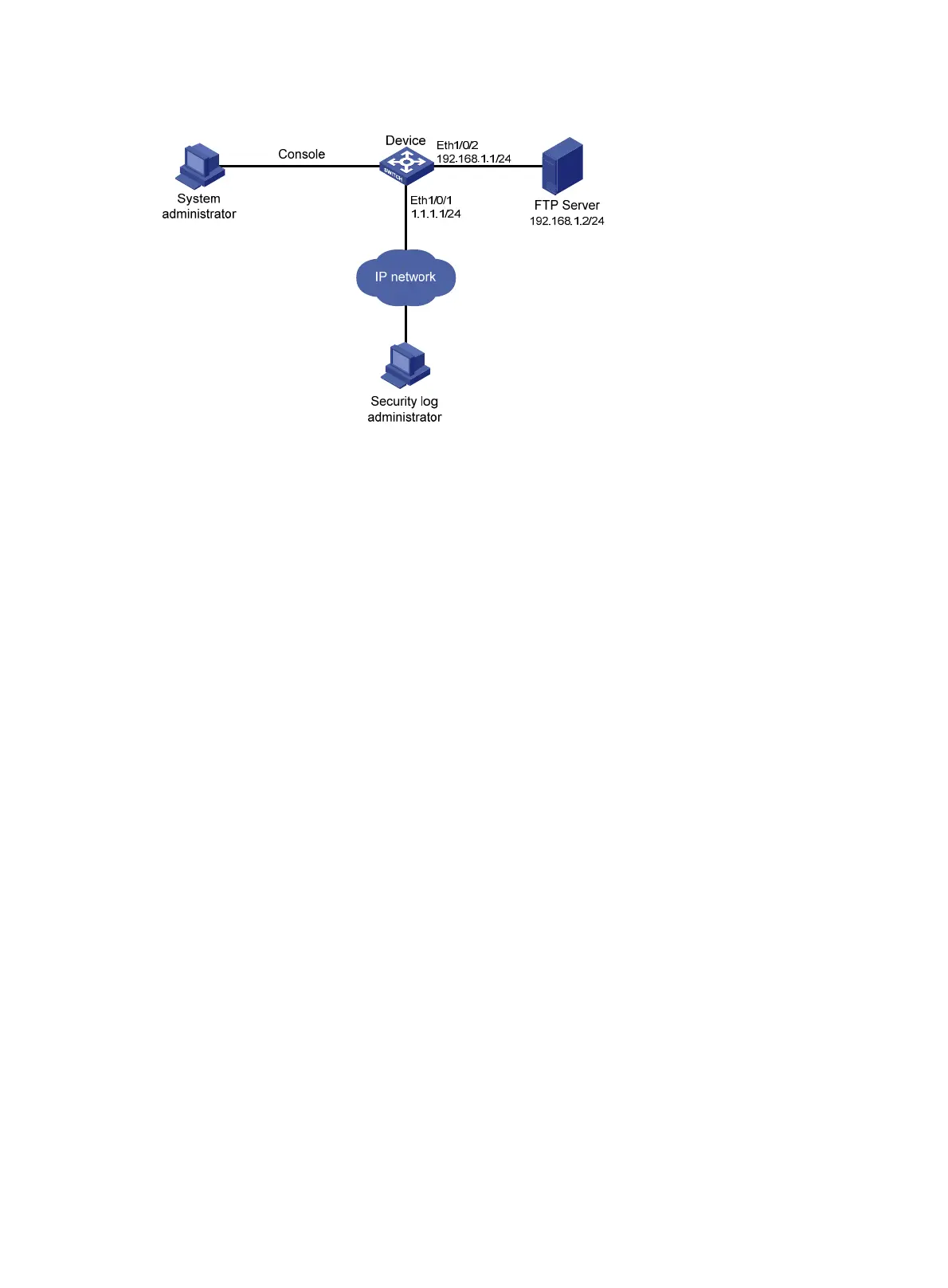
Figure 57 Network diagram for saving security logs in a specific directory
Configuration considerations
The configuration in this example includes the following parts: logging in as the system administrator and
as the security log administrator.
1. Logging in to the device as the system administrator
• Enable the saving of the security logs into the security log file and set the frequency with which the
system saves the security log file to one hour.
• Create a local user seclog with the password 123123123123 , and authorize this user as the security
log administrator. You need to use the authorization-attribute command to set the user privilege
level to 3 and specify the user role as security audit. In addition, specify the service types that the
user can use by using the service-type command.
• Set the authentication mode to scheme for the user logging in to the device, and ensure that only the
local user that has passed the AAA local authentication can view and perform operations on the
security log file.
2. Logging in to the device as the security log administrator
• Set the directory for saving the security log file to Flash:/securitylog/seclog.log.
• View the contents of the security log file to get the security status of the device.
• Back up the security log file to the FTP server.
Configuration procedure
1. Configuration performed by the system administrator
# Enable the saving of the security logs into the security log file and set the frequency with which the
system automatically saves the security log file to one hour.
<Sysname> system-view
[Sysname] info-center security-logfile enable
[Sysname] info-center security-logfile frequency 3600
# Create a local user seclog, and configure the password for the user as 123123123123.
[Sysname] local-user seclog
New local user added.
[Sysname-luser-seclog] password simple 123123123123
# Authorize the user to manage the security log file.
[Sysname-luser-seclog] authorization-attribute level 3 user-role security-audit
175
 Loading...
Loading...