LLDP-MED endpoint devices are located at the network edge and communicate using the LLDP-MED framework.
Any LLDP-MED endpoint device belongs to one of the following three classes:
•Class1(GenericEndpointDevices):ThesedevicesofferthebasicLLDPdiscoveryservices,networkpolicy
advertisement (VLAN ID, Layer 2/802.1p priority, and Layer 3/DSCP priority), and PoE management. This
class includes such devices as IP call controllers and communication-related servers.
•Class2(MediaEndpointDevices):ThesedevicesofferallClass1featuresplusmediastreamingcapability,
and include such devices as voice/media gateways, conference bridges, and media servers.
•Class3(CommunicationDevices):ThesedevicesaretypicallyIPphonesorend-userdevicesthatotherwise
support IP media and offer all Class 1 and Class 2 features, plus location identification and emergency 911
capability, Layer 2 switch support, and device information management.
Appendix F: Virus Throttle security
Virus Throttle is based on the detection of anomalous behavior of network traffic that differs from a normal
activity. Under normal activity, a computer will make fairly few outgoing connections to new computers, but
instead is more likely to regularly connect to the same set of computers. This is in contrast to the fundamental
behavior of a rapidly spreading worm, which will attempt many outgoing connections to new computers. For
example, while computers normally make approximately one connection per second, the SQL Slammer virus
tries to infect more than 800 computers per second.
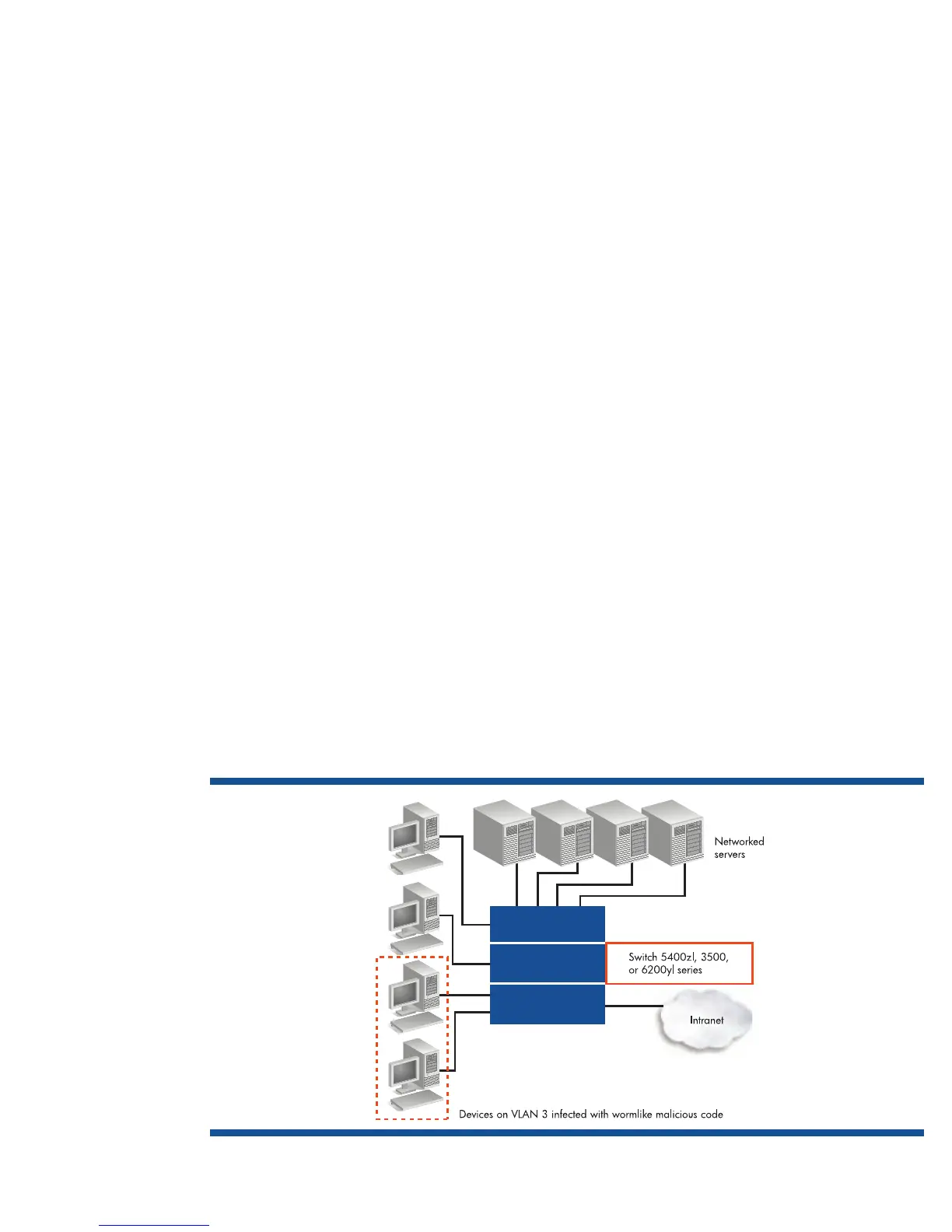
Virus Throttle works by intercepting IP connection requests, that is, connections in which the source subnet and
destination address are different. The Virus Throttle tracks the number of recently made connections. If a new,
intercepted request is to a destination to which a connection was recently made, the request is processed as
normal. If the request is to a destination that has not had a recent connection, the request is processed only if
the number of recent connections is below a pre-set threshold. The threshold specifies how many connections
are to be allowed over a set amount of time, thereby enforcing a connection rate limit. If the threshold is
exceeded, because requests are coming in at an unusually high rate, it is taken as evidence of a virus. This
causes the throttle to stop processing requests and, instead, to notify the system administrator.
This capability can be applied to most common Layer 4 through 7 session and application protocols, including
TCP connections, UDP packets, SMTP, IMAP, Web Proxy, HTTP, SSL, and DNS—virtually any protocol where
the normal traffic does not look like a virus spreading. For Virus Throttle to work, IP routing and multiple VLANs
with member ports must first be configured.
Note that some protocols, such as NetBIOS and WINS, and some applications such as network management
scanners, notification services, and p2p file sharing are not appropriate for Virus Throttle. These protocols
and applications initiate a broad burst of network traffic that could be misinterpreted by the Virus Throttle
technology as a threat.
Figure A6.
65
VLAN 1
VLAN 2
VLAN 3

 Loading...
Loading...











