Example: Preparing a COFF File For eCAN Bootloading
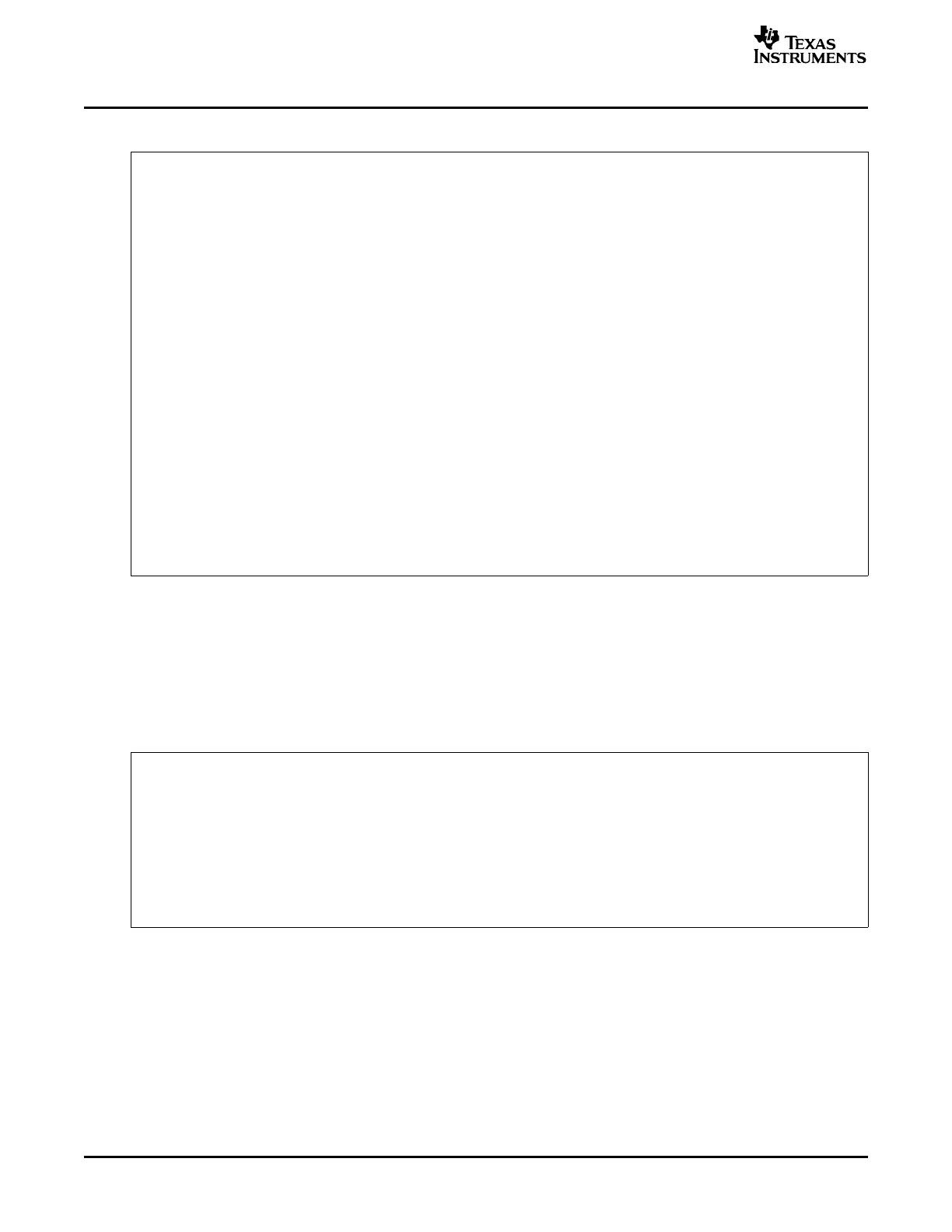
Example 3-1. GPIO34TOG Map File
output attributes/
section page origin length input sections
-------- ---- ---------- ---------- ----------------
codestart
* 0 00000000 00000002
00000000 00000002 DSP280x_CodeStartBranch.obj (codestart)
.pinit 0 00000002 00000000
.switch 0 00000002 00000000 UNINITIALIZED
ramfuncs 0 00000002 00000016
00000002 00000016 DSP280x_SysCtrl.obj (ramfuncs)
.cinit 0 00000018 00000019
00000018 0000000e rts2800_ml.lib : exit.obj (.cinit)
00000026 0000000a : _lock.obj (.cinit)
00000030 00000001 --HOLE-- [fill = 0]
myreset 0 00000032 00000002
00000032 00000002 DSP280x_CodeStartBranch.obj (myreset)
IQmath 0 003fa000 00000000 UNINITIALIZED
.text 0 003fa000 00000155
003fa000 00000046 rts2800_ml.lib : boot.obj (.text)
To load the code using the CAN bootloader, the host must send the data in the format that the bootloader
understands. That is, the data must be sent as blocks of data with a size, starting address followed by the
data. A block size of 0 indicates the end of the data. The HEX2000.exe utility can be used to convert the
COFF file into a format that includes this boot information. The following command syntax has been used
to convert the application into an ASCII hex format file that includes all of the required information for the
bootloader:
Example 3-2. HEX2000.exe Command Syntax
C: HEX2000 GPIO34TOG.OUT -boot -gpio8 -a
Where:
- boot Convert all sections into bootable form.
- gpio8 Use the GPIO in 8-bit mode data format. The eCAN
uses the same data format as the GPIO in 8-bit mode.
- a Select ASCII-Hex as the output format.
The command line shown in Example 3-2 will generate an ASCII-Hex output file called GPIO34TOG.a00,
whose contents are explained in Example 3-3 . This example assumes that the host will be able to read an
ASCII hex format file. The format may differ for your application. . Each section of data loaded can be tied
back to the map file described in Example 3-1 . After the data stream is loaded, the boot ROM will jump to
the Entrypoint address that was read as part of the data stream. In this case, execution will begin at
0x3FA0000.
52 Building the Boot Table SPRU722C – November 2004 – Revised October 2006
Submit Documentation Feedback

 Loading...
Loading...











