FILE AUTHENTICATION
Planning for File Authentication
38 V200C REFERENCE GUIDE
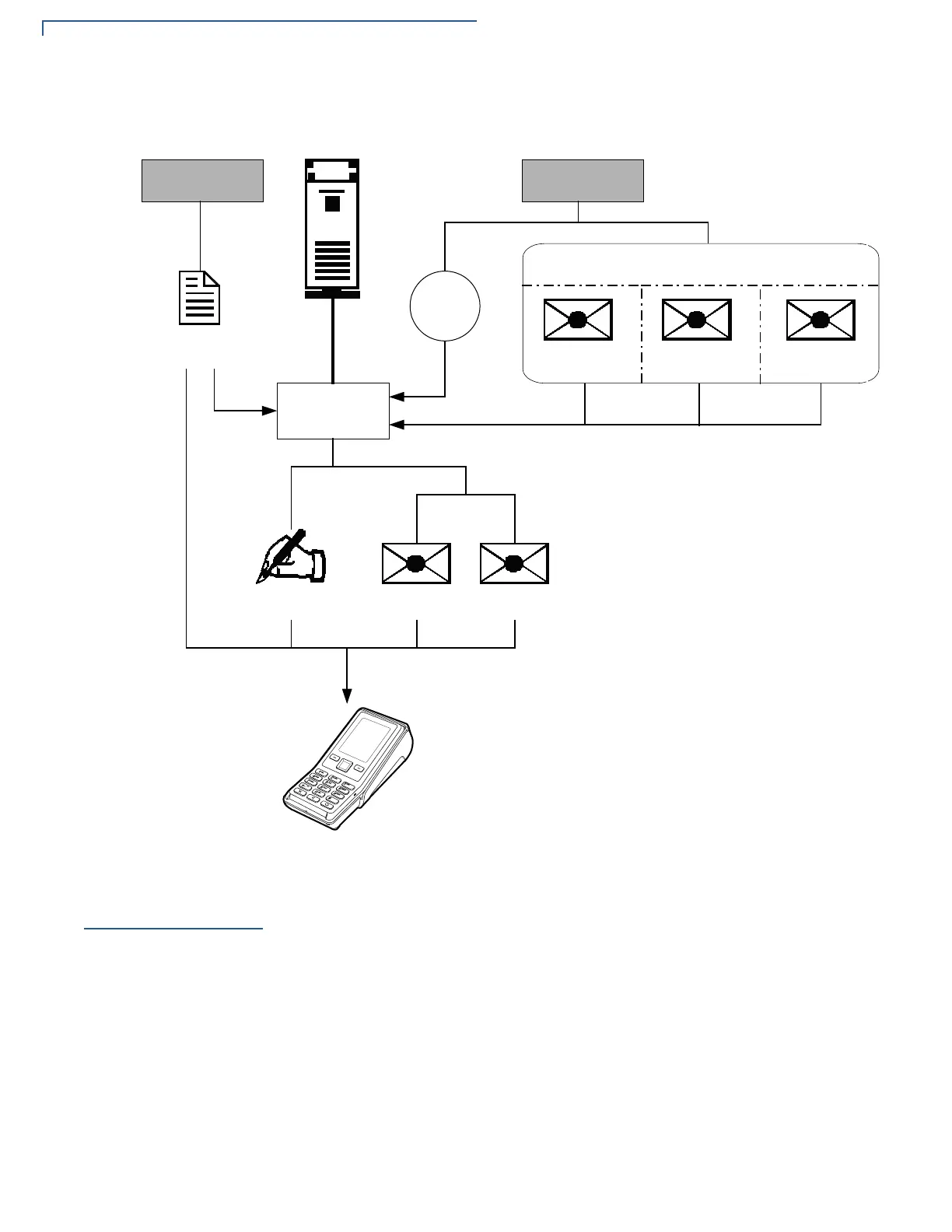
The development and/or deployment process is illustrated in the flowchart below.
Figure 5 The Development / Deployment Process
Planning for File
Authentication
File authentication is an integral part of every terminal. To safeguard the terminal’s
logical security, FA requires that any downloaded application file must be
successfully authenticated before the operating system installs on the unit.
Download and
Installation
The terminal’s Secure Installer plays a critical role on system and application
startup as well as authenticating and installing all components; application,
system and OS.
VERISHIELD
FILE SIGNING
TOOL
PRE-DEPLOYMENT
PROCESS
DEVELOPMENT
PROCESS
SMART
CARD
PIN
SIGNATURE FILE
(*.*.P7S)
SIGNER
CERTIFICATE
SPONSOR
CERTIFICATE
FULLY DEBUGGED
APPLICATION FILE
DEVELOPMENT OS SEARCHES FOR A *.*.P7S FILE.
IF A *.*.P7S FILE IS FOUND, OS THEN SEARCHES FOR
A MATCHING APPLICATION FILE.
IF A MATCHING APPLICATION FILE IS FOUND, OS
COMPARES *.*.P7S FILE'S SIGNATURE AGAINST
VALUES IN THE APPLICATION FILE'S CALCULATED
SIGNATURE.
IF THE VALUES MATCH, THE TWO FILES ARE
AUTHENTICATED, AND THE ATTR_NOT_AUTH BIT
IS SET TO 0.
1)
2)
3)
4)
SIGNER
CERTIFICATE
SIGNER SMART CARD
SPONSOR
CERTIFICATE
SIGNER
PRIVATE KEY

 Loading...
Loading...











