Rockwell Automation Publication 1783-UM001B-EN-P - May 2010 45
Switch Management Chapter 4
• Remove Selected - Click to remove the selected MAC ID from the
authorized list.
• Learned MAC Addresses - This table lists the MAC IDs detected on the
network by the 1783-EMS switch. The port number and MAC ID are
shown for each device detected on the network. This list is built
automatically by the 1783-EMS switch.
• Authorized MAC Addresses - This list indicates which MAC IDs are
allowed on the network. You must create this list. Whenever a new device
comes online, this list is checked to determine if the device is authorized. If
the device is not authorized, an input is sent the controller. (See
Appendix D
for the I/O table of the 1783-EMS switch.)
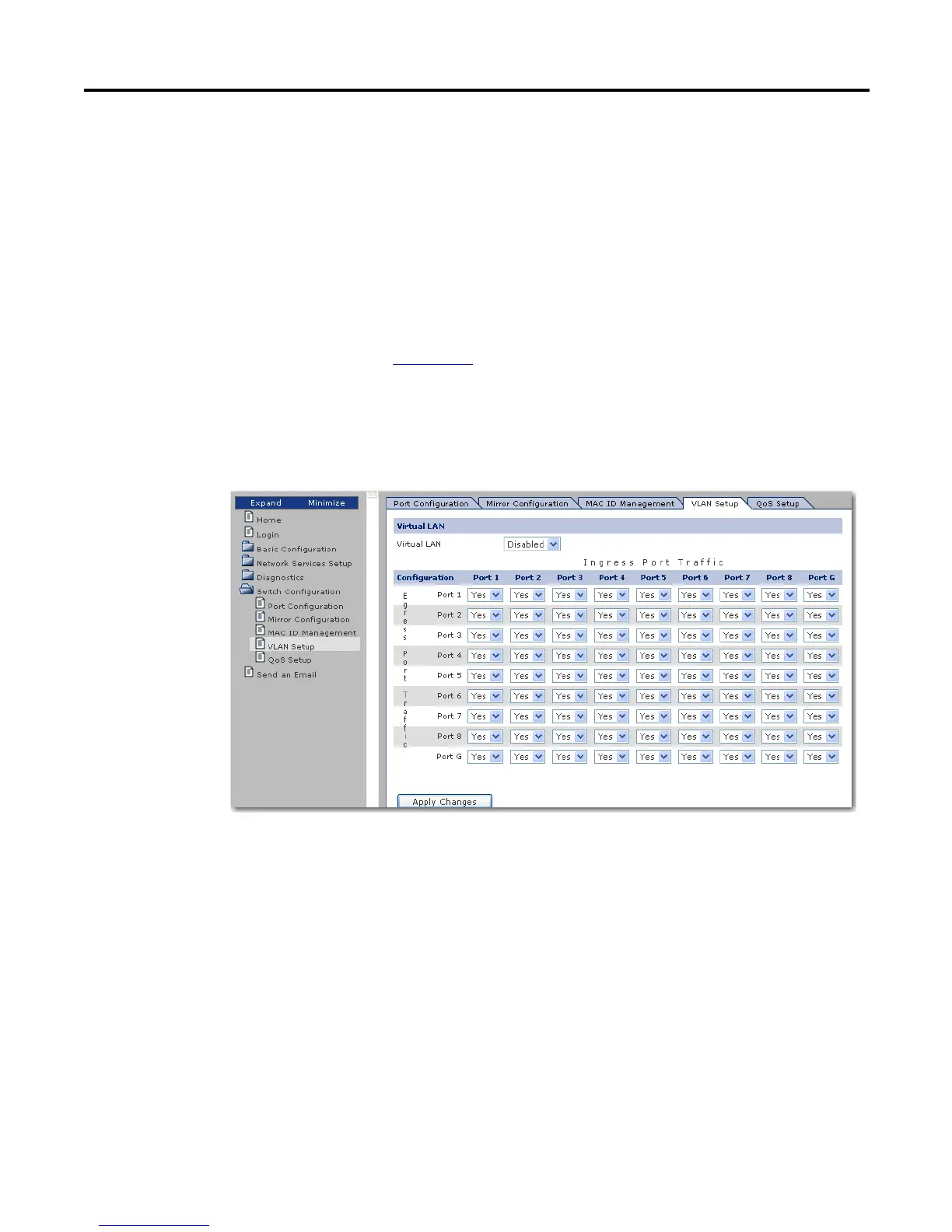
VLAN Setup
Used when network bandwidth becomes critical, VLAN is used to eliminate
traffic caused by multicast and broadcast Ethernet traffic. With this feature, we
can partition the switch ports into different private virtual networks.
For each received packet, the switch resolves the destination address and
determines the appropriate port. The VLAN configuration is then checked to see
if the destination address is configured to receive traffic from the source port.
For example, if a FLEX I/O module is connected to port 2 on the 1783-EMS08T
switch, the I/O module is communicating with a ControlLogix module on
port 3. We want the ControlLogix module on port 3 to receive traffic from the
FLEX I/O module on port 2. VLAN can be used to prevent other devices on the
network from receiving packets from the FLEX I/O module.
Our VLAN configuration would look as shown in the figure. The Egress port
(source port 2) transmits to the Ingress port (destination port) 3.
 Loading...
Loading...