63
Subnet: The subnet of the local network, for establishing an IPSec tunnel between a pair of
security gateways (network-to-network), If the remote peer is a network, select Subnet.
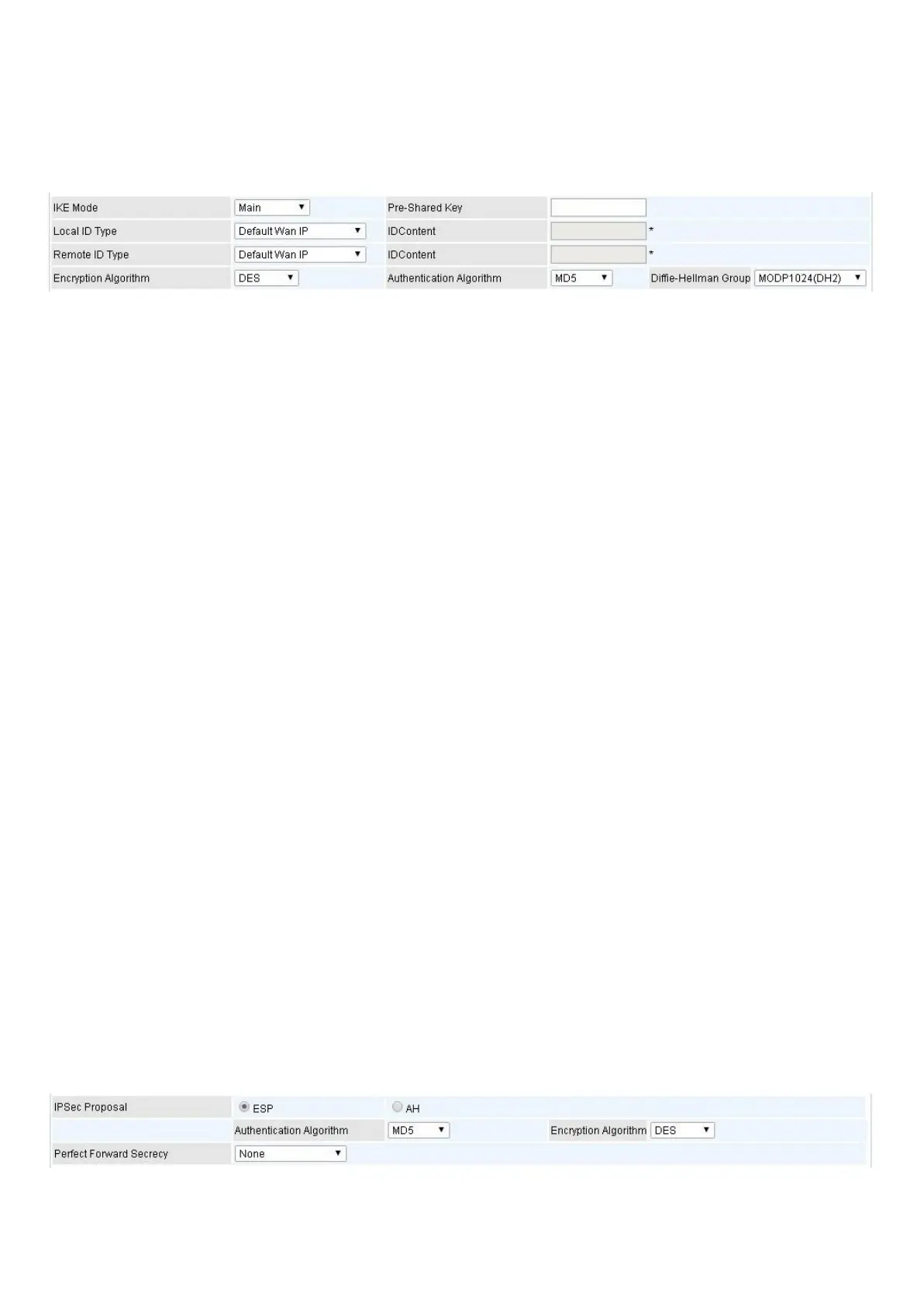
IPSec Phase 1(IKE)
IKE Mode: IKE, Internet Key Exchange, is the mechanism to negotiate and exchange parameters
and keys between IPSec peers to establish security associations(SA). Select Main or Aggressive
mode.
Pre-Shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128
characters. Both sides should use the same key. IKE is used to establish a shared security policy and
authenticated keys for services (such as IPSec) that require a key. Before any IPSec traffic can be
passed, each router must be able to verify the identity of its peer. This can be done by manually
entering the pre-shared key into both sides (router or hosts).
Local ID Type and Remote ID Type: When the mode of IKE is aggressive, Local and Remote peers
can be identified by other IDs.
IDContent: Enter IDContent the name you want to identify when the Local and Remote Type are
Domain Name; Enter IDContent IP address you want to identify when the Local and Remote Type are
IP addresses (IPv4 and IPv6 supported).
Encryption Algorithm: Select the encryption algorithm from the drop-down menu. There are several
options: DES and AES (128, 192 and 256). 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption
method.
AES: Stands for Advanced Encryption Standards, you can use 128, 192 or 256 bits as
encryption method.
Authentication Algorithm: Authentication establishes the integrity of the datagram and ensures it is
not tampered with in transmission. There are 3 options: Message Digest 5 (MD5) and Secure Hash
Algorithm (SHA1, SHA256). SHA1 is more resistant to brute-force attacks than MD5. However, it is
slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Diffle-Hellman Group: It is a public-key cryptography protocol that allows two parties to establish a
shared secret over an unsecured communication channel (i.e. over the Internet). MODP stands for
Modular Exponentiation Groups.
IPSec Phase 2(IPSec)
IPSec Proposal: Select the IPSec security method. There are two methods of verifying the
authentication information, AH(Authentication Header) and ESP(Encapsulating Security Payload).

 Loading...
Loading...











