You cannot use the system-defined any-ipv4 object, because Auto NAT rules add NAT as part
of the object definition, and you cannot edit system-defined objects.
Note
• Translated Source—Choose Destination Interface IP.
Step 7 Click Save to add the rule.
The rule is saved to the Rules table.
Step 8 Click Save on the NAT page to save your changes.
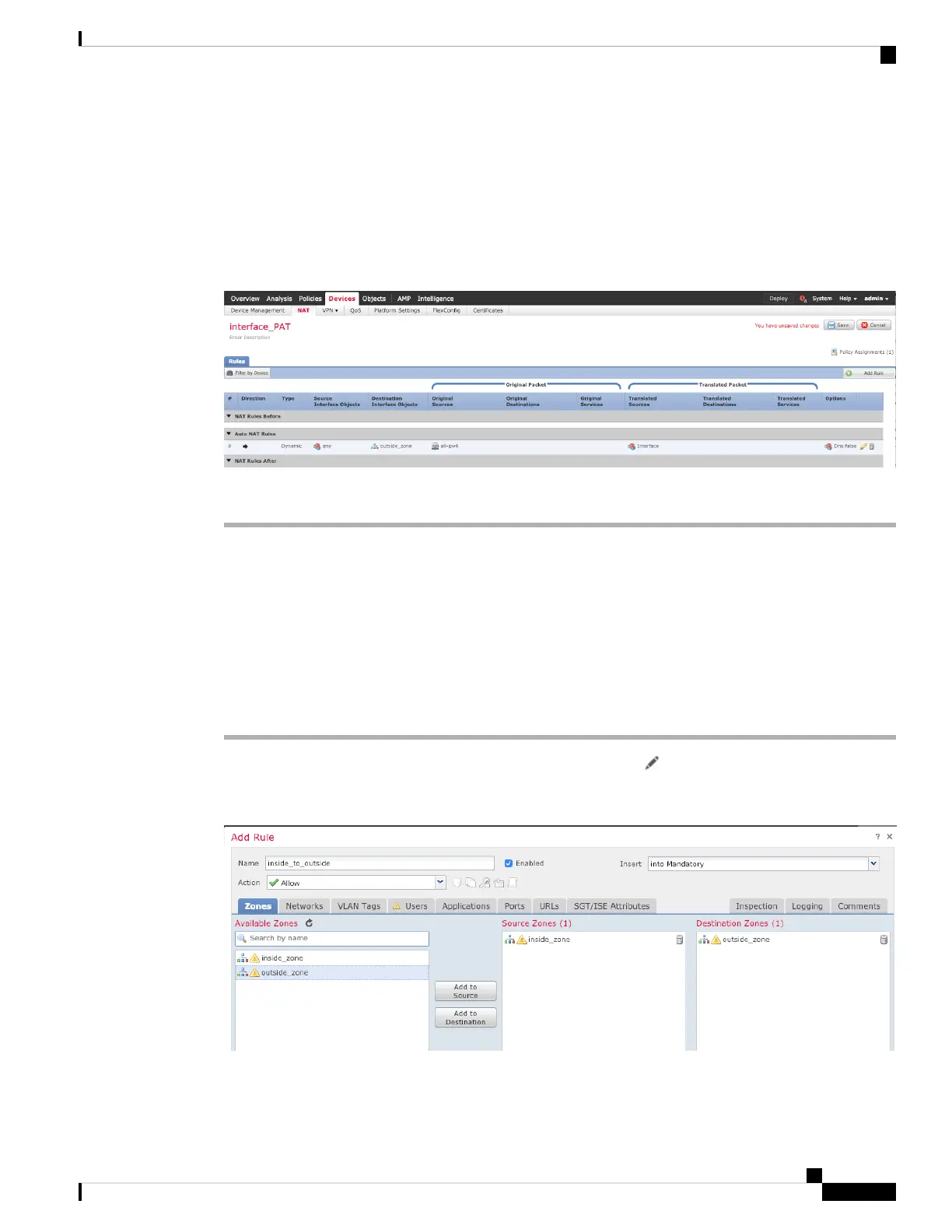
Allow Traffic from Inside to Outside
If you created a basic Block all traffic access control policy when you registered the threat defense, then you
need to add rules to the policy to allow traffic through the device. The following procedure adds a rule to
allow traffic from the inside zone to the outside zone. If you have other zones, be sure to add rules allowing
traffic to the appropriate networks.
Procedure
Step 1 Choose Policy > Access Policy > Access Policy, and click the Edit ( ) for the access control policy assigned
to the threat defense.
Step 2 Click Add Rule, and set the following parameters:
• Name—Name this rule, for example, inside_to_outside.
Cisco Firepower 1100 Getting Started Guide
35
Threat Defense Deployment with the Management Center
Allow Traffic from Inside to Outside

 Loading...
Loading...











