TASKalfa 3500i, TASKalfa 4500i, TASKalfa 5500i
Data Security Kit (E) Overseas Version Security Target
© 2011 KYOCERA MITA Corporation
20
Dependent
Relations
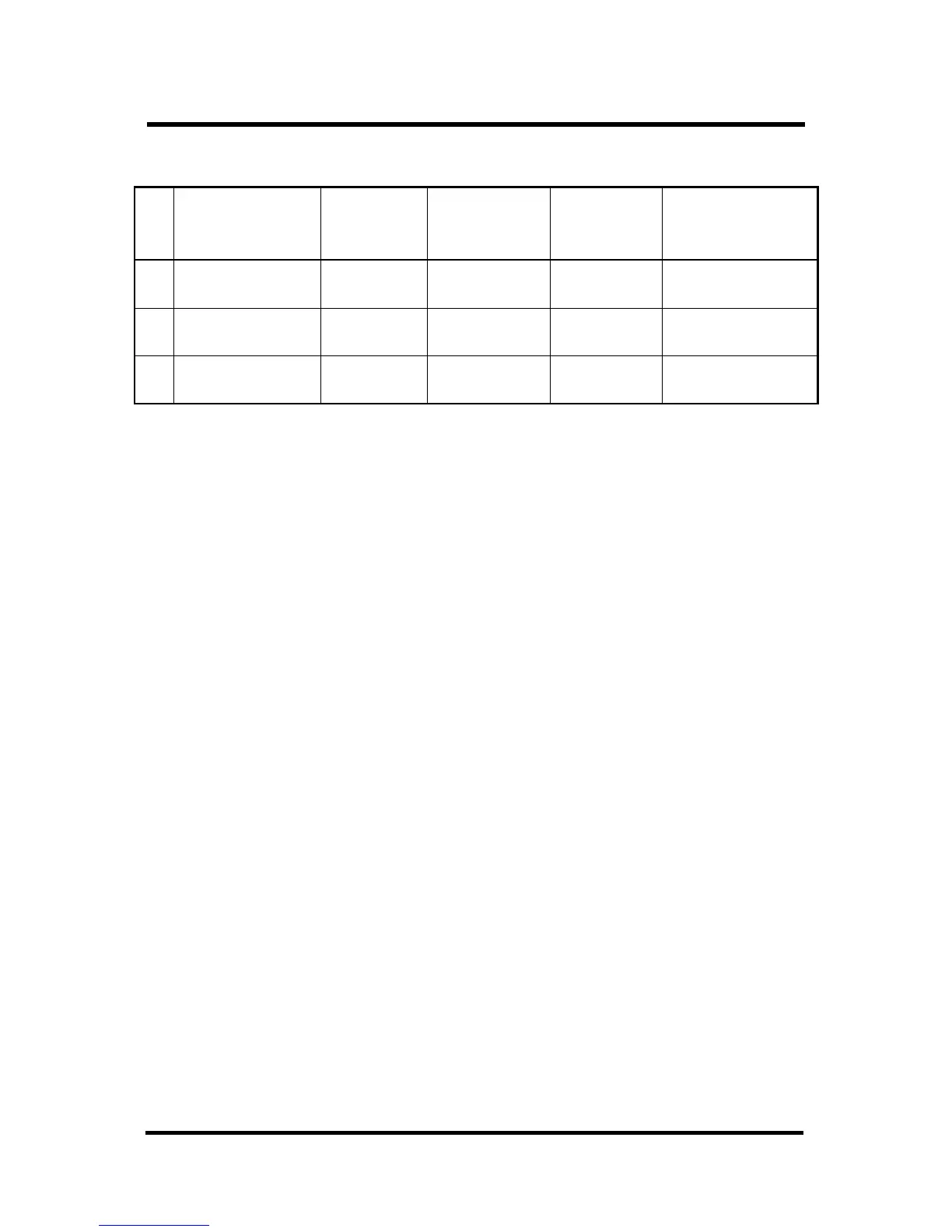
Reference
No.
Note
1 FCS. CKM.1 None FCS_COP.1
FCS_CKM.4
2
Not needed
Refer to 6.3.2.1
2 FCS_COP.1 None FCS_CKM.1
FCS_CKM.4
1
Not needed
Refer to 6.3.2.1
3 FDP_RIP.1
None None
-
6.3.2.1. Rationale for why dependency on FCS_CKM.4 is not needed
The cryptographic key is generated when the main power is tuned on, and is stored
for encryption operation that is to read and write the image data on the HDD while
the power is turned on. Beside this purpose, there is no interface available to
allow unauthorized users to get access. Thus the requirement for the
cryptographic key destruction is not needed.
6.3.3. Rationale for Security Assurance Requirements
Since this TOE aims to counter the attacks from low level attackers to access
image data, the TOE is required to ensure the counter-measure against the low
level attacks. EAL3 includes analysis of the security measures of the TOE at
development phase (performing and analyzing systematic tests, and evaluating
the management of the development environment and the developed products)
and also includes analysis whether the sufficient guidance information is included
so that the security can be used safely. The assurance requirement conforms to
EAL3. Thus selection of EAL3 is reasonable.

 Loading...
Loading...











