System Management Guide Security
Edition: 01 3HE 11018 AAAC TQZZA 19
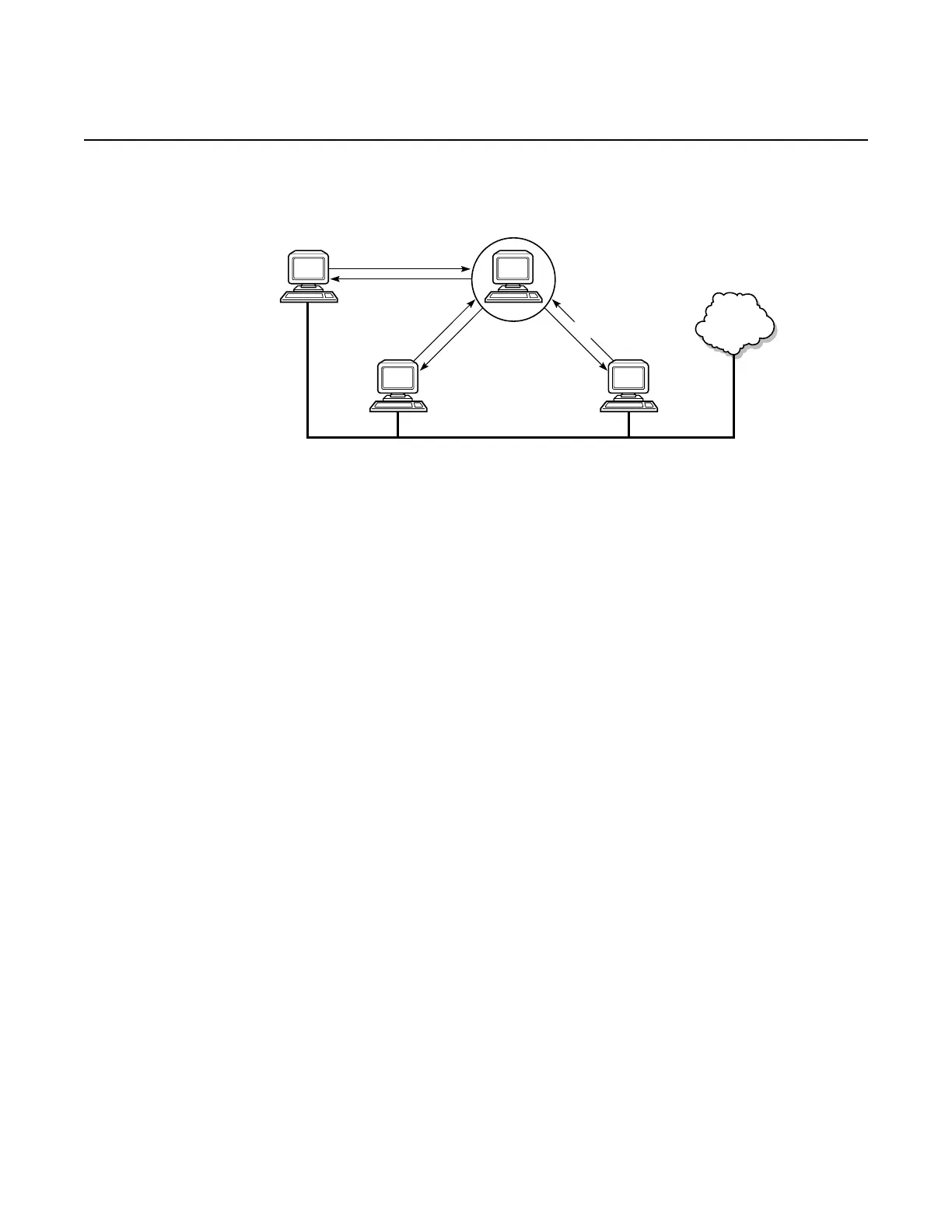
Figure 1 RADIUS Requests and Responses
3.1.1 Authentication
Authentication validates a user name and password combination when a user
attempts to log in.
When a user attempts to log in through the console or through Telnet, SSH, SFTP,
SCP, or FTP, the 7705 SAR client sends an access request to a RADIUS,
TACACS+, or local database.
Transactions between the client and a RADIUS server are authenticated through the
use of a shared secret. The secret is never transmitted over the network. User
passwords are sent encrypted between the client and RADIUS server, which
prevents someone snooping on an insecure network to learn password information.
If the RADIUS server does not respond within a specified time, the router issues the
access request to the next configured servers. Each RADIUS server must be
configured identically to guarantee consistent results. Up to five RADIUS servers can
be configured.
If a server is unreachable, it will not be used again by the RADIUS application until
30 seconds have elapsed, to give the server time to recover from its unreachable
state. After 30 seconds, the unreachable server becomes available again for the
RADIUS application.
If, within the 30 seconds, the RADIUS server receives a valid response to a
previously sent RADIUS packet on that unreachable server, the server immediately
becomes available again.
Access Request
Access Request
ALU-2
ALU-1
ALU-3
Access Request
Access Accepted
Access Accepted
RADIUS Server
Authentication
X
Network
19673

 Loading...
Loading...