11.2 ARP Inspection
According to the ARP Implementation Procedure stated in 11.1.3 ARP Scanning, it can be found
that ARP protocol can facilitate the Hosts in the same network segment to communicate with one
another or access to external network via Gateway. However, since ARP protocol is implemented
with the premise that all the Hosts and Gateways are trusted, there are high security risks during
ARP Implementation Procedure in the actual complex network. Thus, the cheating attacks against
ARP, such as imitating Gateway, cheating Gateway, cheating terminal Hosts and ARP Flooding
Attack, frequently occur to the network, especially to the large network such as campus network
and so on. The following part will simply introduce these ARP attacks.
¾ Imitating Gateway
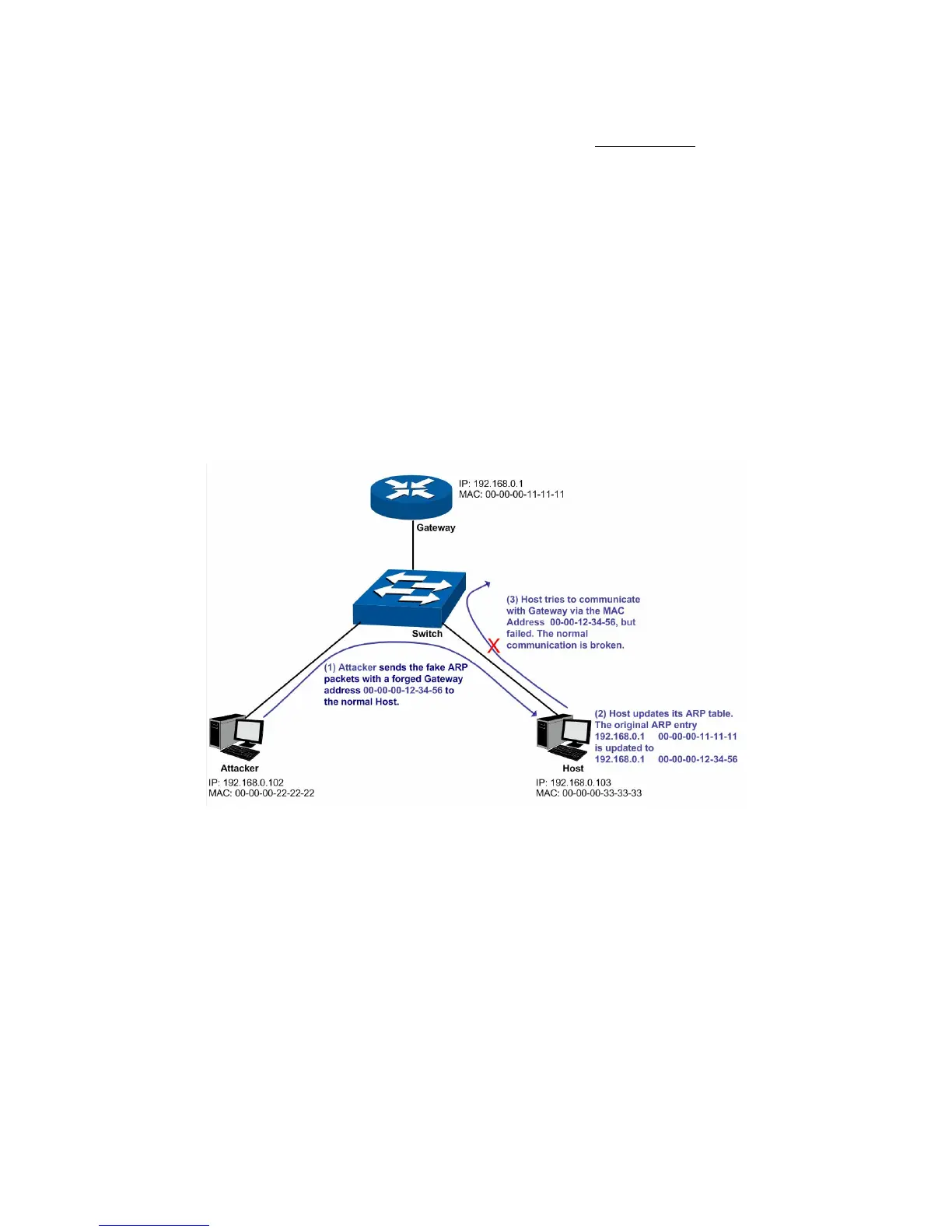
The attacker sends the MAC address of a forged Gateway to Host, and then the Host will
automatically update the ARP table after receiving the ARP response packets, which causes that
the Host can not access the network normally. The ARP Attack implemented by imitating Gateway
is illustrated in the following figure.
Figure 11-9 ARP Attack - Imitating Gateway
As the above figure shown, the attacker sends the fake ARP packets with a forged Gateway
address to the normal Host, and then the Host will automatically update the ARP table after
receiving the ARP packets. When the Host tries to communicate with Gateway, the Host will
encapsulate this false destination MAC address for packets, which results in a breakdown of the
normal communication.
¾ Cheating Gateway
The attacker sends the wrong IP address-to-MAC address mapping entries of Hosts to the
Gateway, which causes that the Gateway can not communicate with the legal terminal Hosts
normally. The ARP Attack implemented by cheating Gateway is illustrated in the following figure.
147

 Loading...
Loading...











