FILE AUTHENTICATION
Introduction to File Authentication
V
X
810 REFERENCE GUIDE 75
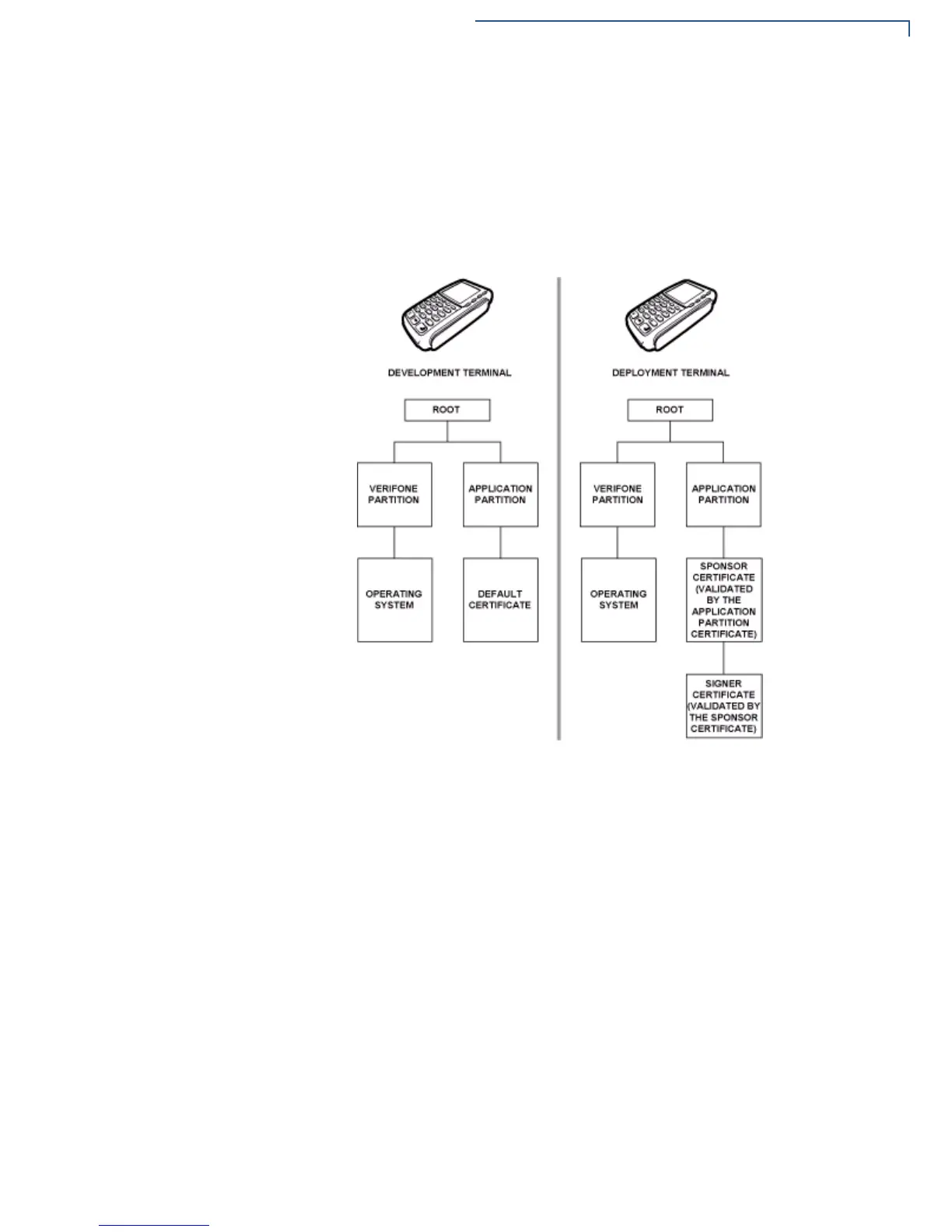
Ultimately, it is the sponsor’s decision how to implement the logical security
provided by file authentication on a field-deployed device. Additional certificates
can be obtained from the VeriFone CA anytime to implement new sponsor and
signer relationships in deployment devices. VeriShield allows for multiple
sponsors and signing certificates in a device. This allows the flexibility of unique
signatures for each executable or data files.
Figure 20 Certificate Trees in Development and Deployment Devices
Permanency of the Certificate Tree
The data contained in a digital certificate is stored in the device’s certificate tree
when the certificate is authenticated, and the certificate file itself is erased from
SRAM.
The certificate tree file is stored in a reserved area of non-volatile memory and is
therefore relatively permanent. New certificate data can be added to the existing
certificate tree (up to a maximum of 21 certificates).
 Loading...
Loading...