____________________________________________________________________________________
____________________________________________________________________________________
34 VoIP subscriber gateways
When ‘Add VLAN for Management’ is set, configuring by using DHCP and TR-069 protocol will be available
through ‘Management’ service. If the checkbox is disabled, configuring by using DHCP and TR-069 protocol will
be available through ‘Internet’.
Description of fields (accessible to configure) are described in section 3.1.2.1.1. ‘Network settings’
submenu, ‘Internet’ service.
To save changes into operative memory of the device, click ‘Save changes’ button. To write settings into
non-volatile memory, click ‘Apply’ button.
3.1.2.2 ‘IPSec’ submenu
Use the menu to configure encryption on IPSec (IP Security) technology. IPSec is a set of protocols to
provide data protection (data is transmitted via IP). IPSec allows you to provide authentication, integrity check
and/or IP-packets encryption. IPSec includes protocols for tamper-free key exchange in Internet.
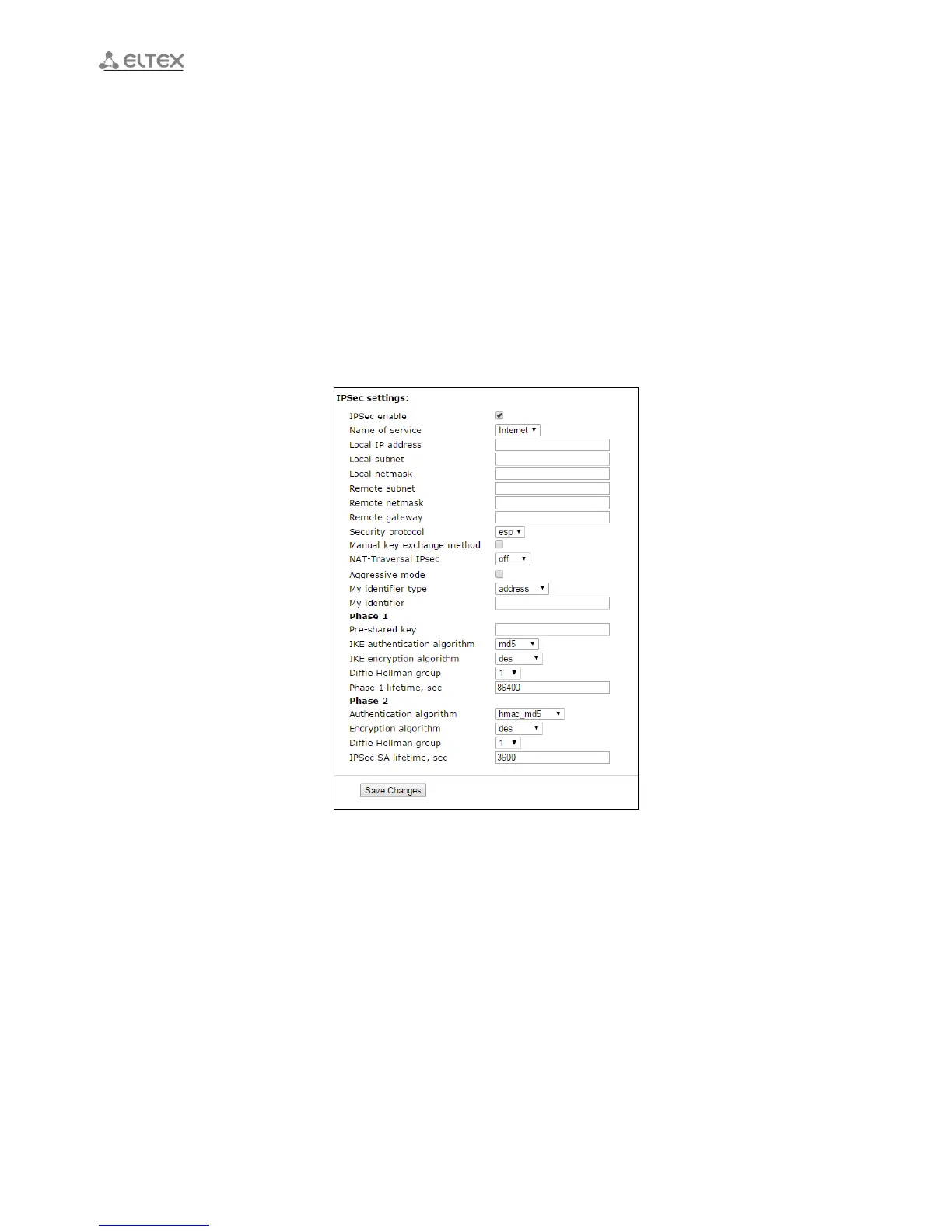
IPSec settings:
– IPSec enable – permit to use IPSec protocol for data encryption;
– Name of service – service selection where encryption via IPSec protocol will be used;
– Local IP address – the device address for operation via IPSec protocol;
– Local subnet in cooperation with Local netmask determine local subnet for creation network-to-
network or network-to-point topology;
– Remote subnet in cooperation with Remote netmask determines address of remote subnet for
connection with using encryption via IPSec protocol. If mask has value 255.255.255.255 then
connection is established with a single host. Mask (distinct from 255.255.255.255) allows you to
specify whole subnet. Thus, functionality of the device allows you to organize the following 4
network topologies with using encryption traffic via IPSec protocol: point-to-point, network-to-
point, point-to-network, network-to-network;
– Remote gateway – gateway providing access to the remote subnet;
– Security protocol – there are two key protocols: AH (Authentication header) and EPS
(Encapsulating Security Payload). The first provides data authentication except data encryption;
the second provides both operations. IPSec can operate in one of the two modes: ‘transport’ or

 Loading...
Loading...