Wireless-N 150 Router WNR1000v3 User Manual
Safeguarding Your Network 2-3
v1.0, February 2010
– Advanced Wireless Settings. You access these under Advanced in the main menu (see
“Viewing Advanced Wireless Settings” on page 2-11).
• Use Wi-Fi Protected Setup (WPS) to automatically set the SSID and implement WPA/
WPA2 security on both the router and the client device. If the clients in your network are
WPS capable, you can use Wi-Fi Protected Setup (WPS) to automatically set the SSID and
implement WPA/WPA2 security on both the router and the client device (see “Using Push 'N'
Connect (Wi-Fi Protected Setup)” on page 2-13).
Basic security options are listed in order of increasing effectiveness in Table 2-1. Other features
that affect security are listed in Table 2-2 on page 2-4. For more details on wireless security
methods, click the link to the online document “Wireless Networking Basics” in Appendix B.
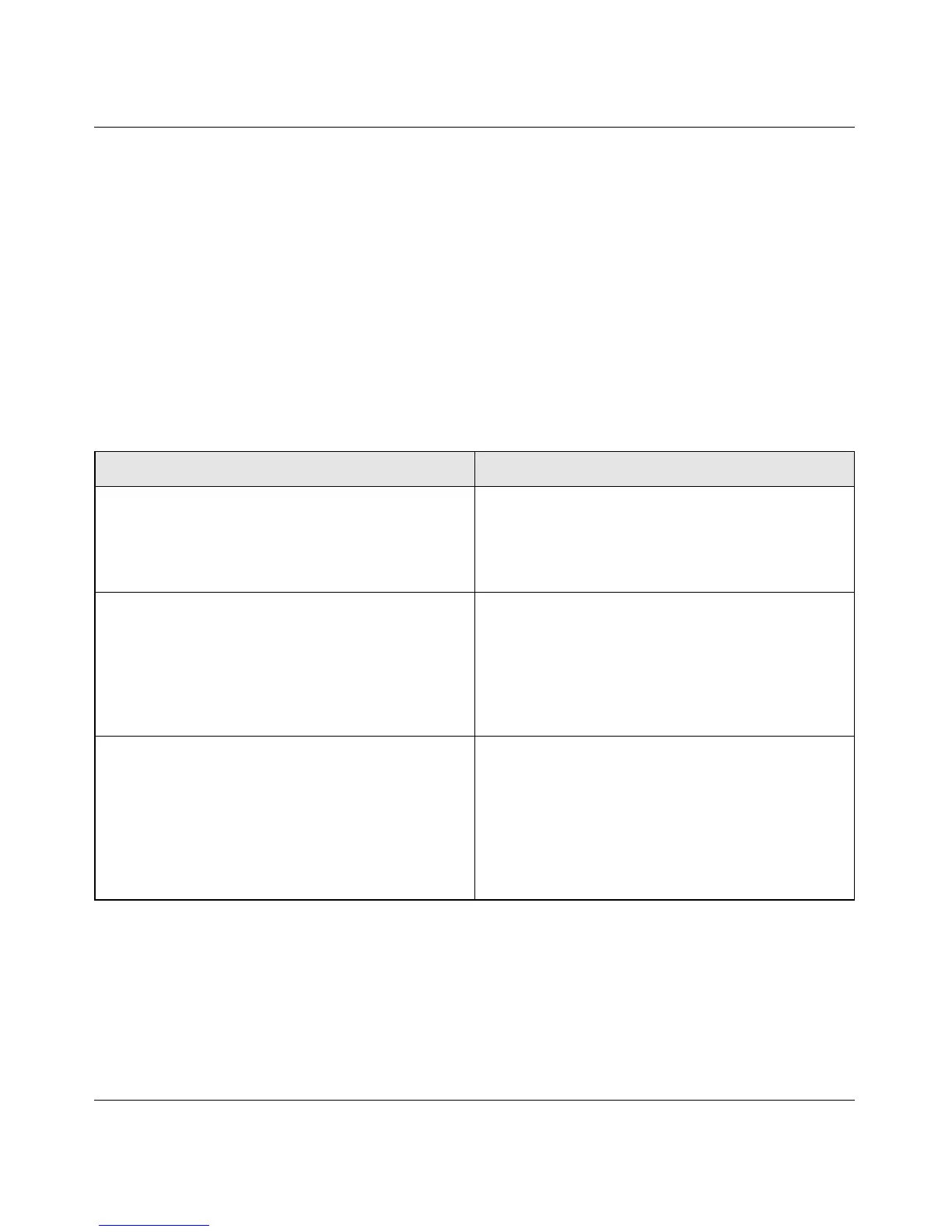
Table 2-1. Wireless Security Options
Security Type Description
None. No wireless security. Recommended only for
troubleshooting wireless connectivity. Do not run an
unsecured wireless network unless it is your
intention to provide free Internet access for the
public.
WEP. Wired Equivalent Privacy. Wired Equivalent Privacy (WEP) data encryption
provides moderate data security. WEP Shared Key
authentication and WEP data encryption can be
defeated by a determined eavesdropper using
publicly available tools.
For more information, see “Configuring WEP
Wireless Security” on page 2-8.
WPA-PSK (TKIP). WPA-PSK standard encryption
with TKIP encryption type.
WPA2-PSK (AES). Wi-Fi Protected Access version 2
with Pre-Shared Key; WPA2-PSK standard
encryption with the AES encryption type.
WPA-PSK (TKIP) + WPA2-PSK (AES). Mixed mode.
Wi-Fi Protected Access with Pre-Shared Key (WPA-
PSK and WPA2-PSK) data encryption provides
extremely strong data security, very effectively
blocking eavesdropping. Because WPA and WPA2
are relatively new standards, older wireless adapters
and devices might not support them.
For more information, see “Configuring WPA-PSK
and WPA2-PSK Wireless Security” on page 2-10.

 Loading...
Loading...











