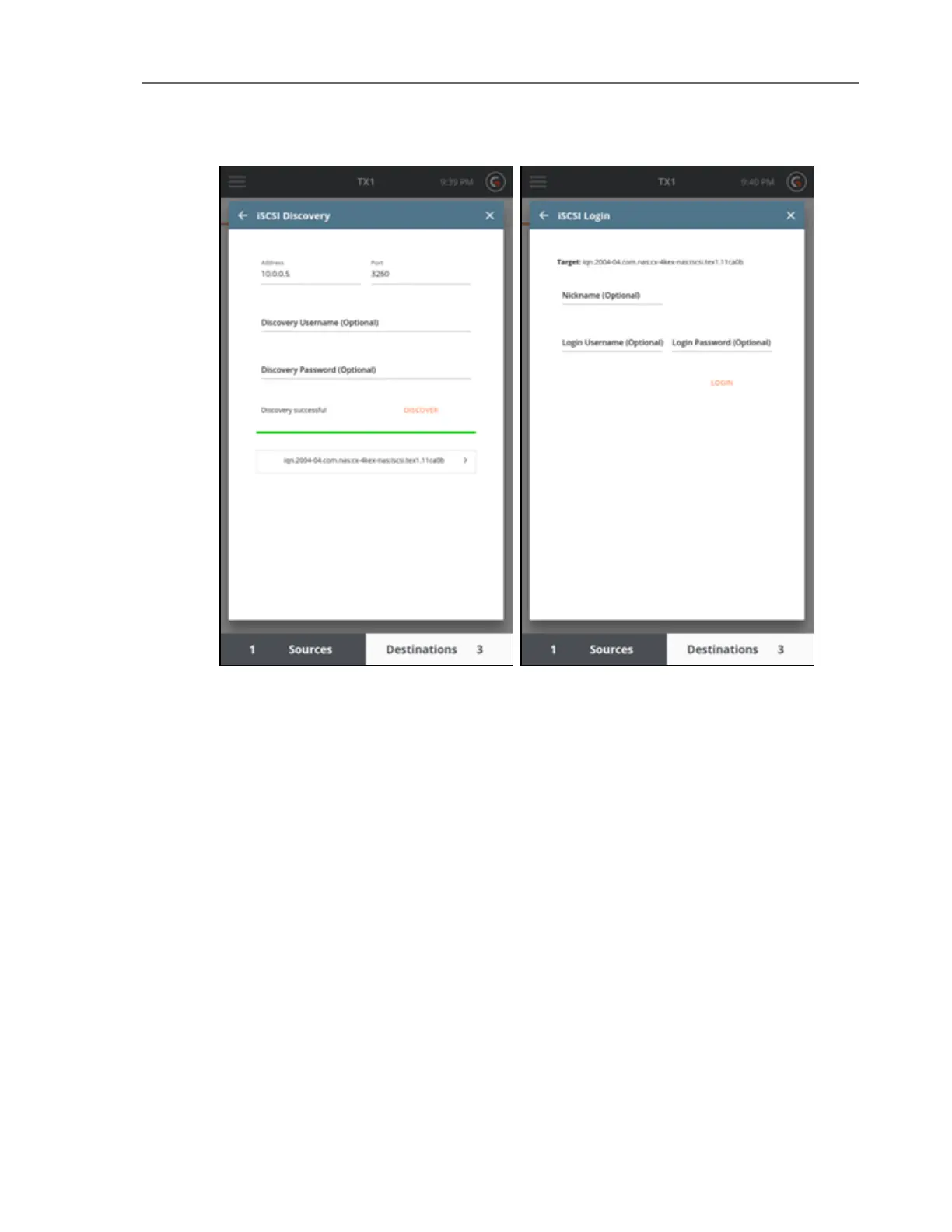
5. The target should now be listed in the Sources or Destinations list, depending on where
you chose to mount it. The target can now be accessed like a normal drive for Duplication
as a source (if mounted as a source), a Duplication as a destination (if mounted as a des-
tination), Hash (as a source), Verify (as a destination), and some media utilities.
CHAPTER 4 Using the TX1 49
 Loading...
Loading...