Section 3 Secure system setup
3.1 Physical interfaces
GUID-DA029F79-3173-4D17-A7B9-AA213FAC8F68 v1
To reduce exposure for cyber-attacks and thus comply with cyber security
requirements, it must be possible to prevent services in the IED from operating on
other physical interfaces than the ones specified by the vendor or by the owner.
3.2 IP ports
GUID-A5E2256D-C7E2-4CAC-8EAD-E7DBBCB4AF08 v1.1.2
The IP port security guideline cannot suggest concrete products for a secure system
setup. This must be decided within the specific project, requirements and existing
infrastructure. The required external equipment can be separate devices or devices
that combine firewall, router and secure VPN functionality.
To set up an IP firewall the following table summarizes the IP ports used in the
GMS600 IED which is based on Relion 650 series of IEDs. The ports are listed in
ascending order. The column “Default state” defines whether a port is open or
closed by default. All ports that are closed can be opened as described in the
comment column in the table. Front and Rear refer to the physical front and rear
port. The protocol availability on these ports is configurable.
ABB recommends using common security measures, like firewalls, up to date anti
virus software, etc. to protect the IED and the equipment around it.
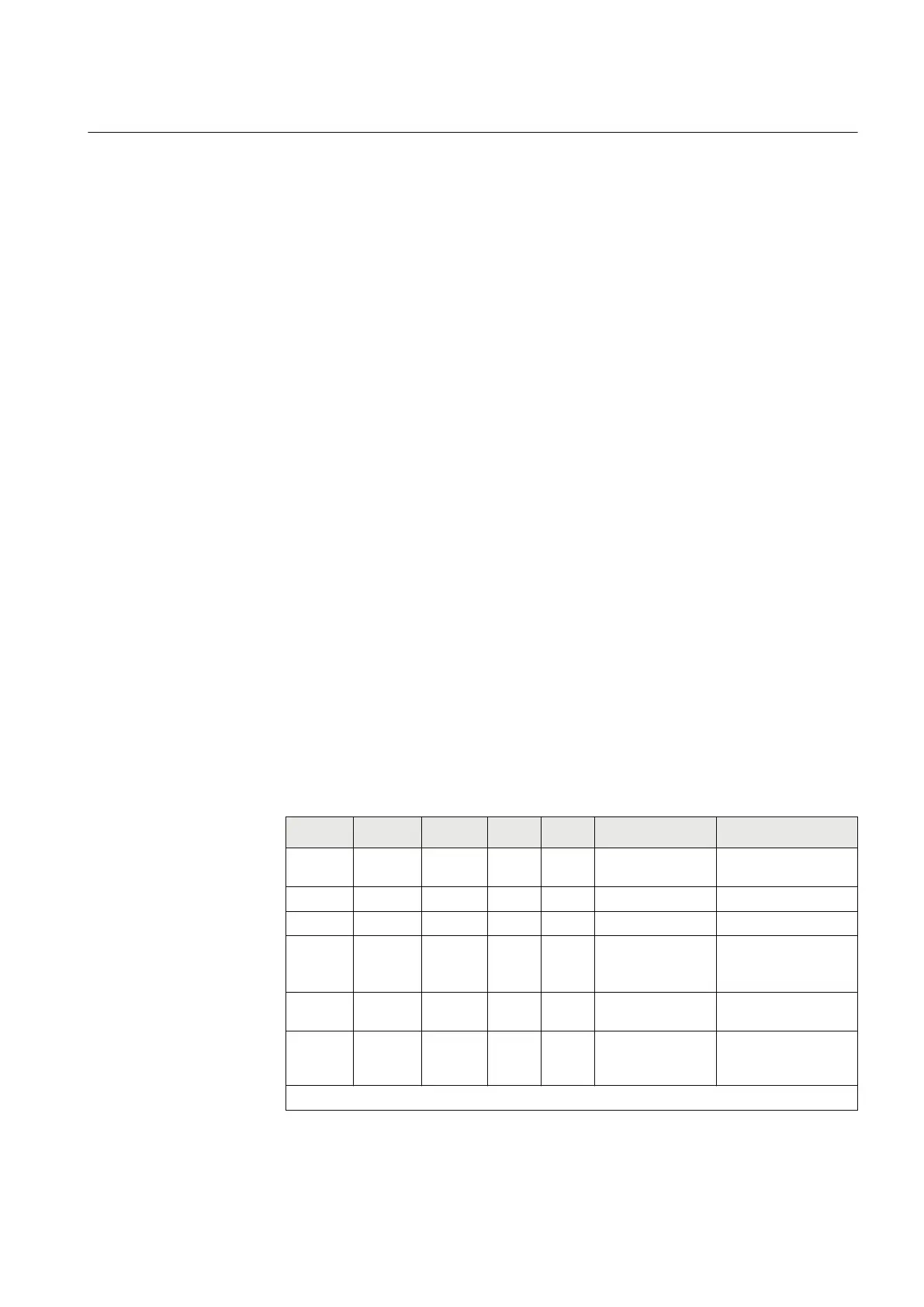
Table 1: Available IP ports
Port
Protocol Default
state
Front Rear Service Comment
21 TCP open OFF OFF FTP (clear text
password)
File transfer protocol
67 UDP open ON N/A DHCP Front port only, RJ45
102 TCP open OFF ON IEC 61850 MMS communication
123 UDP closed OFF OFF SNTP Enabled when IED is
configured as SNTP
master.
1)
443 TCP closed ON ON HTTPS WebHMI
communication
7001 TCP closed OFF OFF FST SPA protocol on
TCP/IP used by FST
(Field Service Tool)
Table continues on next page
1MRK 511 454-UEN A Section 3
Secure system setup
GMS600 1.3 7
Cyber security deployment guideline
 Loading...
Loading...











