Section 8 IEEE Compliance statement
GUID-716DC304-B1C7-417E-BA01-DF9C5AD6660A v1
8.1 IEEE1686 compliance
GUID-009DC366-9ABB-430B-A71C-AA4E5FD1B631 v2.1.1
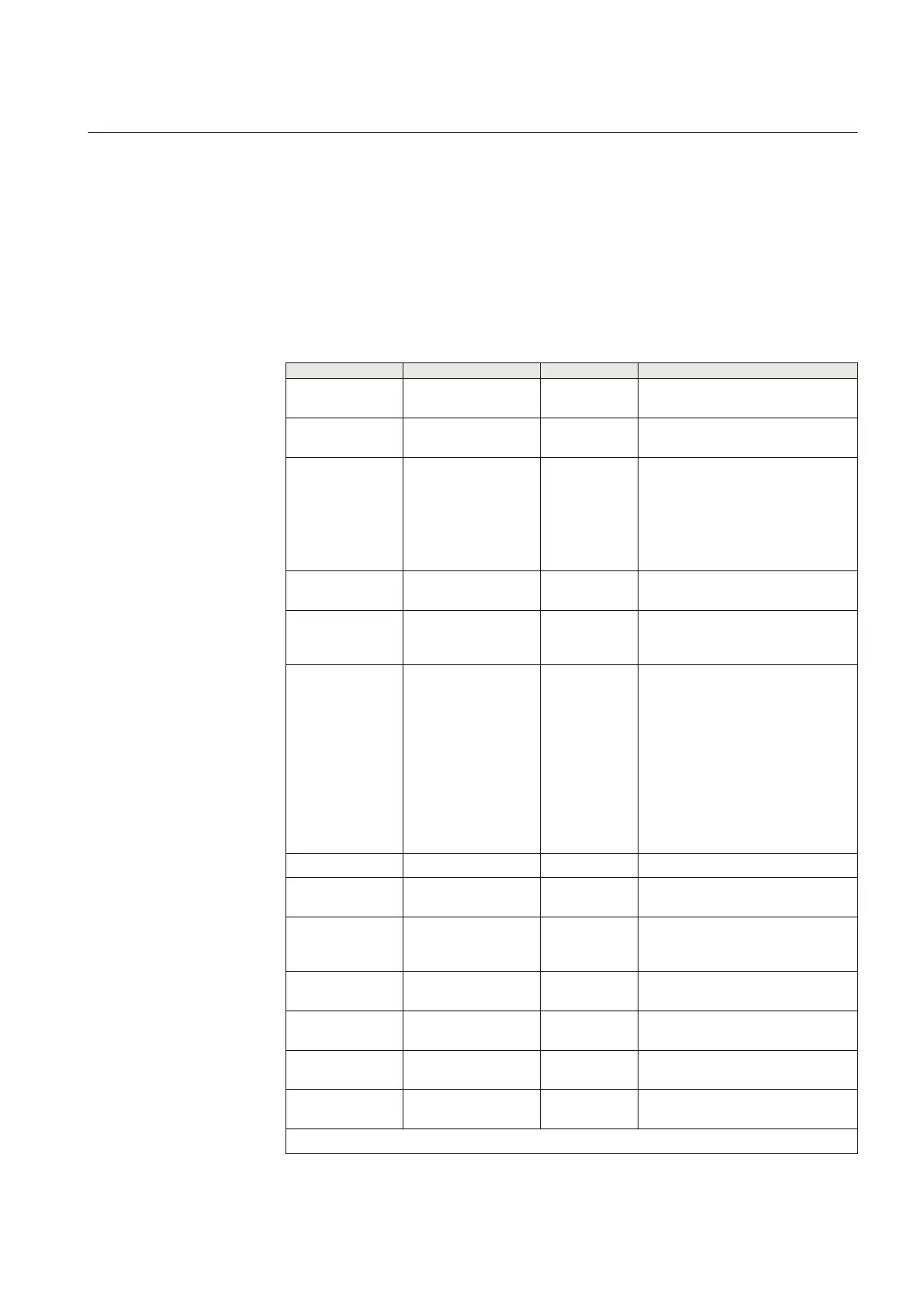
Table 10: IEEE1686 compliance
Clause Title Status Comment
5 IED cyber security
features
Acknowledge
5.1 Electronic access
control
Acknowledge
5.1.1 IED access control
overview
Comply Access is protected for local access
through control panel. Access is
protected for local access through
communication /diagnostic ports.
Access is protected for remote
access through a communication
media
5.1.2
Password defeat
mechanisms
Comply
5.1.3 Number of individual
users
Exceed 20 unique ID/password combinations
are supported (only applicable in
Local User Account Management)
5.1.4
Password
construction
Comply The minimum enforced password
length is configurable. If password
policy is enforced, minimum is 6.
Use of mix of lower and
UPPERCASE characters is
enforced, configurable in password
policies Use of numerical values is
enforced, configurable in password
policies. Use of non-alphanumeric
character (e.g. @, #, %, &, *) is
enforced, configurable in password
policies.
5.1.5 IED access control Acknowledge
5.1.5.1 Authorization levels
by password
Comply
5.1.5.2 Authorization using
role-based access
control (RBAC)
Exceed
IED provides 7 user-defined roles.
5.1.6 IED main security
functions
Acknowledge
5.1.6 a) View data Comply Feature is accessible through
individual user accounts.
5.1.6 b) View configuration
settings
Comply Feature is accessible through
individual user accounts.
5.1.6 c) Force values Comply Feature is accessible through
individual user accounts.
Table continues on next page
1MRK 511 454-UEN A Section 8
IEEE Compliance statement
GMS600 1.3 47
Cyber security deployment guideline
 Loading...
Loading...











