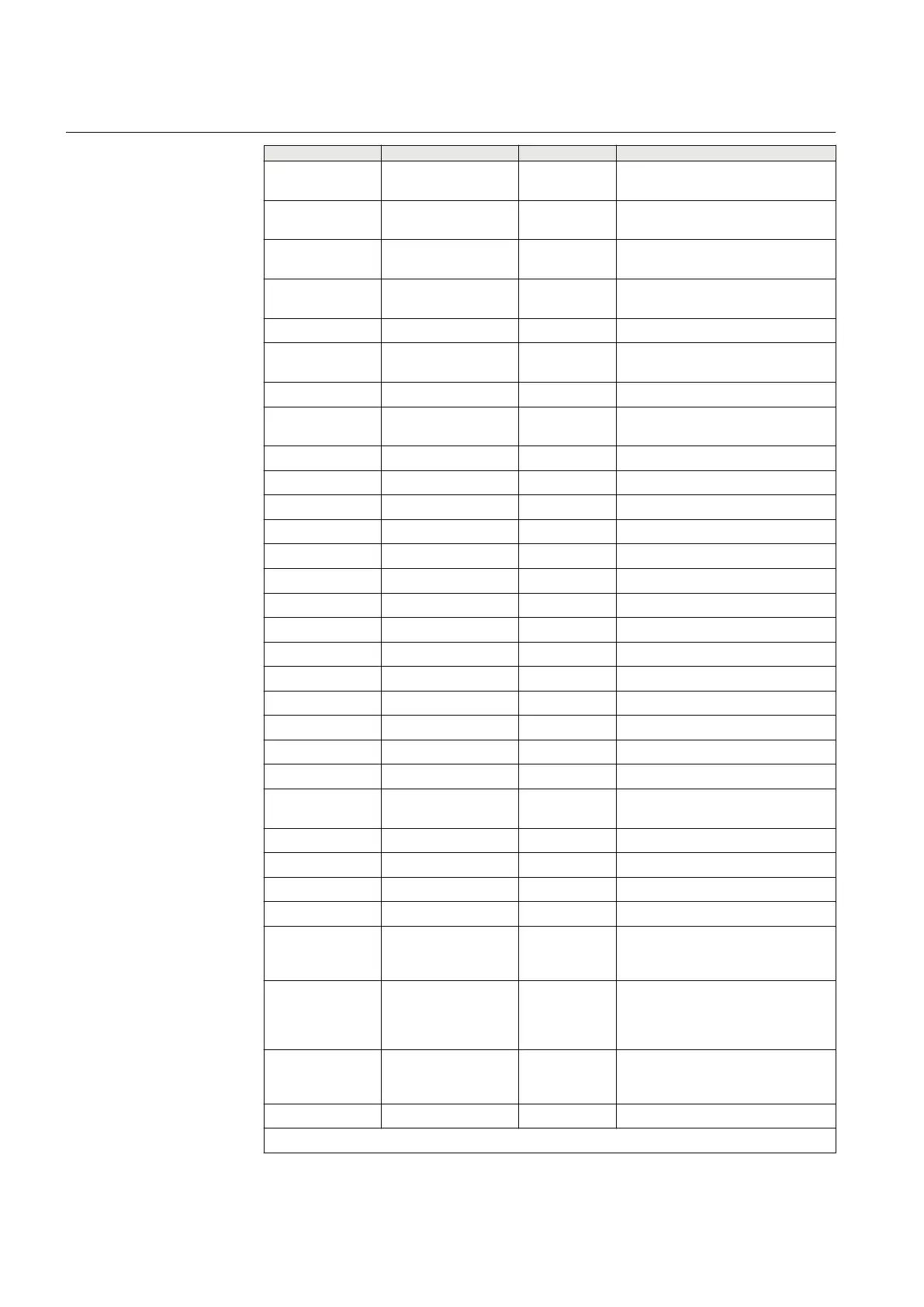
Clause Title Status Comment
5.1.6 d) Configuration change Comply Feature is accessible through
individual user accounts.
5.1.6 e) Firmware change Comply Feature is accessible through
individual user accounts.
5.1.6 f) ID/password or RBAC
management
Comply Feature is accessible through
individual user accounts.
5.1.6 g) Audit log Comply Feature is accessible through
individual user accounts.
5.1.7 Password display Comply
5.1.8 Access time-out Comply A time-out feature exists. The time
period is configurable by the user.
5.2 Audit trail Acknowledge
5.2.1 Audit trail background Comply The Audit log can be viewed through
PCM 600
5.2.2 Storage capability Comply
5.2.3 Storage record Comply
5.2.3 a) Event record number Comply
5.2.3 b) Time and date Comply
5.2.3 c) User identification Comply
5.2.3 d) Event type Comply
5.2.4 Audit trail event types Acknowledge
5.2.4 a) Login Comply
5.2.4 b) Manual logout Comply
5.2.4 c) Timed logout Comply
5.2.4 d) Value forcing Comply
5.2.4 e) Configuration access Exception
5.2.4 f) Configuration change Comply
5.2.4 g) Firmware change Comply
5.2.4 h) ID/password creation
or modification
Comply
5.2.4 i) ID/password deletion Comply
5.2.4 j) Audit-log access Comply
5.2.4 k) Time/date change Comply
5.2.4 l) Alarm incident Comply
5.3 Supervisory
monitoring and
control
Acknowledge
5.3.1 Overview of
supervisory
monitoring and
control
Comply
Made available through IEC61850
and syslog
5.3.2 Events Exception Time/date change and configuration
access not reported; Otherwise
compliance
5.3.3
Alarms Acknowledge
Table continues on next page
Section 8 1MRK 511 454-UEN A
IEEE Compliance statement
48 GMS600 1.3
Cyber security deployment guideline
 Loading...
Loading...











