329
Cisco 3900 Series, Cisco 2900 Series, and Cisco 1900 Series Integrated Services Routers Generation 2 Software Configuration Guide
Chapter Administering the Wireless Device
Configuring the Access Point for Local Authentication and Authorization
8. show running-config
9. copy running-config startup-config
DETAILED STEPS
To disable AAA, use the no aaa new-model command in global configuration mode. To disable
authorization, use the no aaa authorization {network | exec} method1 command in global
configuration mode.
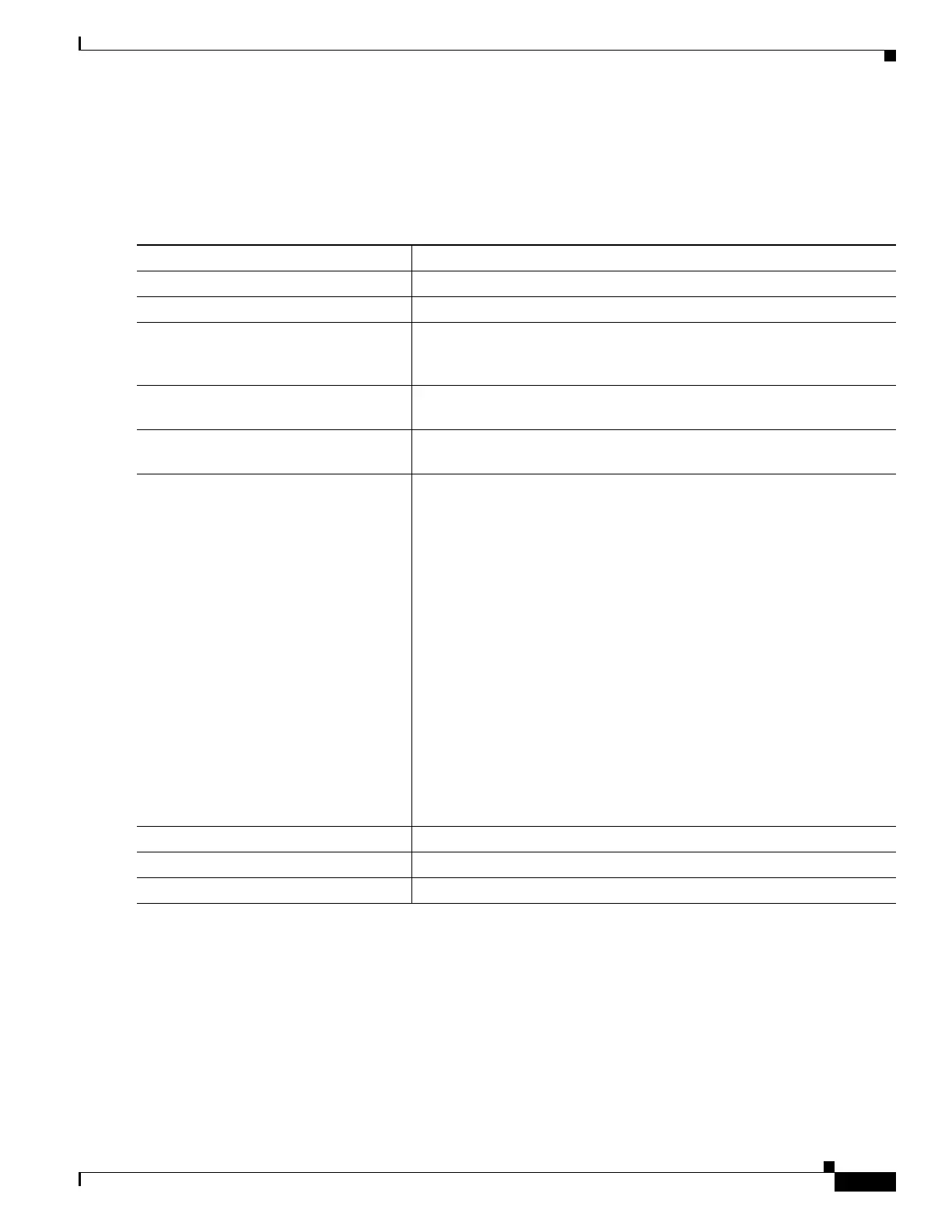
Command Purpose
Step 1
configure terminal Enters global configuration mode.
Step 2
aaa new-model Enables AAA.
Step 3
aaa authentication login default local Sets the login authentication to use the local username database. The
default keyword applies the local user database authentication to all
interfaces.
Step 4
aaa authorization exec local Configures user AAA authorization to determine whether the user is
allowed to run an EXEC shell by checking the local database.
Step 5
aaa authorization network local Configures user AAA authorization for all network-related service
requests.
Step 6
username name [privilege level]
{password encryption-type password}
Enters the local database, and establishes a username-based
authentication system.
Repeat this command for each user.
• For name, specify the user ID as one word. Spaces and quotation
marks are not allowed.
• (Optional) For level, specify the privilege level that the user has after
gaining access. The range is 0 to 15. Level 15 gives privileged EXEC
mode access. Level 0 gives user EXEC mode access.
• For encryption-type, enter 0 to specify that an unencrypted password
follows. Enter 7 to specify that a hidden password follows.
• For password, specify the password that the user must enter to gain
access to the wireless device. The password must be from 1 to 25
characters long, can contain embedded spaces, and must be the last
option specified in the username command.
Note The characters TAB, ?, $, +, and [ are invalid characters for
passwords.
Step 7
end Returns to privileged EXEC mode.
Step 8
show running-config Verifies your entries.
Step 9
copy running-config startup-config (Optional) Saves your entries in the configuration file.
 Loading...
Loading...











